Over the last couple of months, we’ve heard a lot about a huge attack at Target stores where thousands of credit card numbers had been stolen. The attack was pulled off by a strain of malware located on the point of sale systems for the stores.
Though the exact malware has not been disclosed as of yet, apparently it used a tactic known as RAM scraping to grab CC numbers. Threats like this one and others are forcing retailers, financial institutions and security services to reconsider how we deal with in-person financial transactions.
RAM Scraping in Target Hacks
RAM or Random Access Memory is a part of your system that does things like store variables for mathematical calculations and general memory space for various applications. In this case, it’s where the credit card numbers are stored before they get encrypted and sent across the net to the retailer.
RAM scraping is where a piece of malware watches the memory space of the application doing the encrypting and then parse out all credit card numbers. It then sends those numbers off to its command and control server, completely circumventing the encryption measures put in place for protecting the numbers.
Think of it this way, a soldier is going to send a secret message to his General by using a one time encryption key to encode the message. Once that message is encoded, he can send it.
However, the soldier first needs to write down that message so he can use it as well as the encryption key to produce the Ciphertext. If a spy was able to view the original message while it was being encrypted, he wouldn’t need to decrypt anything. That’s basically what is going on here.
In the case of the POS breaches, it’s really not possible to remove the CC data from ever being on the system, you would need to change either how Credit Card information is sent or change how the credit cards work.
Current Technology
I found two examples of current credit card concepts that are similar to this, one from MasterCard that allows a person to create sub-credit cards with dynamic numbers that only have a set limit and therefore decrease the potential for a criminal using ALL of your credit.
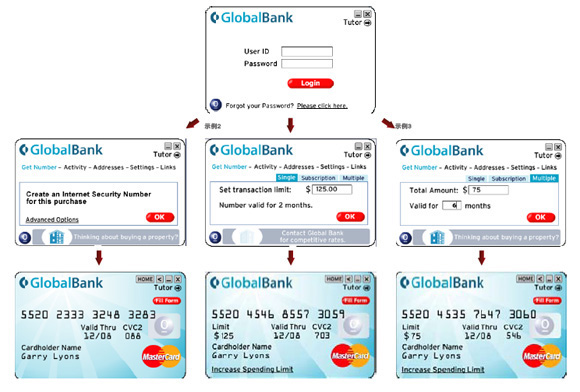
The other concept involves using an LCD screen and a few key buttons in order to hide/show the card number.

The card is developed by Dynamics Inc, who create other types of “smart cards” in an attempt to make the banking world more secure. An additional feature of this card is that every time the card is not in use, the financial data located on the “strip” is erased. It is then re-written once the proper pin is entered into the card using the keys on the front.
While this technology would prevent anyone just copying down the card number or stealing it and attempting to use/copy the card, it would not prevent RAM scraping malware.
Security over the Pond
While technologies are still being developed here in the states, Europe and Asia are already ahead of the game with their smart card technology. Using built-in computers for authentication, processing and storage, the smart cards are far more secure than what we use in the U.S.
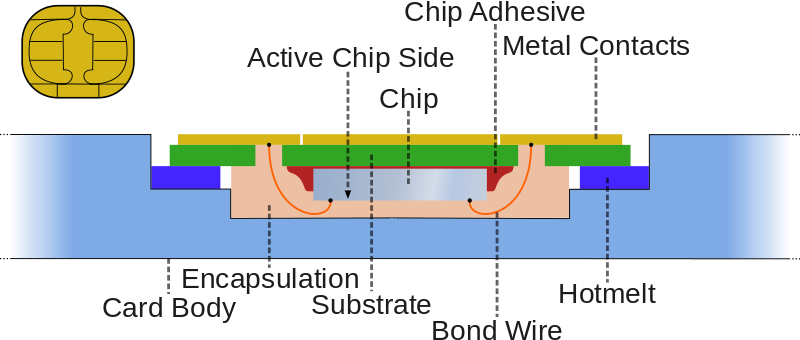
The main reason why we here in the states don’t have access to these types of cards is that they cost a significant amount more money to produce than do our normal 50 cents cards.
Though even the smart cards employed overseas are not completely secure, certain types of malware have been developed to counter their security when using them on a home system (some PC developers create slots for smart cards in the hardware). In addition, numerous “walk-by” attacks have been tested and put into action where the “swipe-less” technology allows for malicious characters to steal your financial data just by walking by.
New Forms of Payment
RAM Scraping is only one of a multitude of different attacks that steal cards from average users and retailers alike. The first line of defense is always security by protecting your systems, but it’s possible to circumvent these securities when warnings are ignored or maintenance isn’t done.
So rather than relying on the use of an unsecured and outdated monetary trading system trying to work in a digital world, why not consider changing the way we do business so that even when numbers are stolen, they are worthless.
Two Factor Purchasing
Taking a lesson from Bitcoin, what if our credit cards only stored address information, like an account username. If stolen by a cyber criminal it would be useless and not worth anything but for a consumer scanning that “username” and having a request made to transfer funds could be authenticated by the user in real-time.

For example using an App on a phone that would require the user to enter something secure and unique like a thumbprint or answer private questions. Once the transaction has been authenticated, the money is transferred.
At any rate, while there would still be a card number on the POS system, if a cyber-criminal stole it, without the proper authentication, it would be worthless.
Although, what about folks who don’t have mobile phones or any way authenticate their purchase?
Dynamic Credit Card Numbers
Another idea is to have a card that never uses the same numbers, but changes with every purchase. This would make it so that even if a cyber criminal were to obtain your CC number, it would be worthless after you had used it once.
Using a computer chip in the actual card, the number can be shown on an LCD screen for user use and the actual number associated with the bar would automatically be changed. The only limitation of employing this with current standards is that there are only 1,099,511,627,776 unique numbers available.
In order to fix this limitation, why not take a page from the cyber security community and use the same type of format as hashing algorithms. MD5 hashes are 32 characters long and use hexadecimal values (0-09, ABCDF) so an example would be:
22b5 a4f9 c360 4e8b e02d de40 7ba4 56d7
The total amount of possible results from using this standard would be 1.2089258e+24 or 1,208,925,819,614,629,174,706,176. This might make online purchasing a bit more difficult when plugging in actual numbers into a form, however from a physical security standpoint, it would be incredibly secure.
Conclusion
In the meantime, before we get dynamically generated credit card numbers and highly technical cards connected to the internet of things, we just have to be careful where we swipe our cards. It’s best to keep an eye on your credit use as often as possible, especially when you’ve been traveling places, specifically to purchases made using your card that you weren’t involved in and if you get really paranoid, the other option is just to use cash.
Replacing cards when you suspect they have been stolen or compromised might be dissuaded by possible drops in your ability to use the card until it is replaced. Banks have attempted to make this process less painful by sending overnight cards to members, but for some folks, that’s too long to go without their money. Hopefully the near future will bring us a secure option for using our money, or at least an easier way to replace our cards.
Thanks for reading and DFTBA!











