The tech support scam (AKA the Microsoft/Windows support technician call), which is essentially about social engineering a mark over the phone by making up non-existent problems and extorting money, is evolving.
I had already documented how scammers were also targeting Apple Mac users in a similar fashion to what they do to their Windows counterparts. Now, those same crooks are going after smart phone and tablet users.
This is not too surprising since the market for mobile is surpassing that of the traditional desktop computer.
Companies involved in these scams can use one of two methods (or both) to reach out to potential victims: cold calling and/or online advertising.
In this example, online adverts are the lure but keep in mind that the same could (and most certainly will) apply to cold calls.
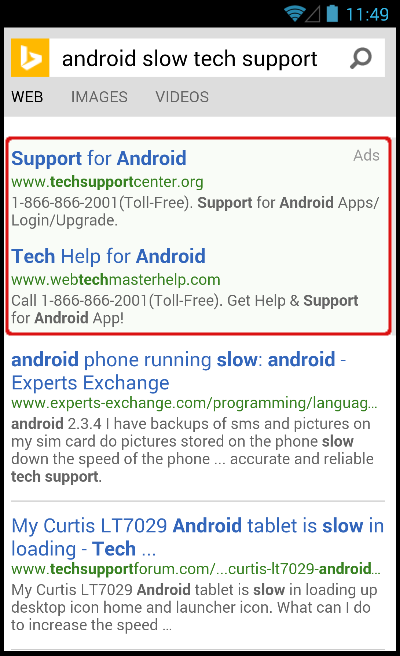
Figure 1: Bing search results for Android support
While paying for ads requires a certain budget, ads have the advantage of funnelling higher quality prospects because people are actually already experiencing an issue.
In contrast, cold-calling is a very wasteful approach (low ratio of interested people for the number of outgoing calls) and not to mention that in many countries cold-calling is completely illegal.
The following (Figure 1) is a search that was performed directly from an Android tablet, querying the Bing search engine for “android slow tech support”.
The top two results are actually paid ads (as opposed to organic results) which guarantees the buyer best placement and therefore more traffic.
Now onto the website itself (Figure 2). It is your typical, run-of-the-mill online tech support page whose main goal is to incite the visitor to call the 1-800 number for assistance.

Figure 2: a tech support website
Very often, the same company will register different domain names with different phone numbers while in reality they all belong to the same group. This technique allows them to create multiple identities which they can cycle through in case of abuse/complaint reports.
Such sites can easily be spotted because the content is almost identical (copy/paste) and some of the graphics are the same (Figure 3).

Figure 3: safety seals
So what exactly happens if you call the number? How are these people able to fix your phone or tablet remotely?
I was prepared for every possibility, having a Virtual Machine running Android’s Jelly Bean and also a real physical Motorola Droid 4.
Interestingly enough, the tech support technician told me that he would not be able to directly connect to our phone and that I had to plug it into a computer (laptop or desktop) first.
What their intent was quickly became clear when they asked me to download remote login software so they could connect to our PC.
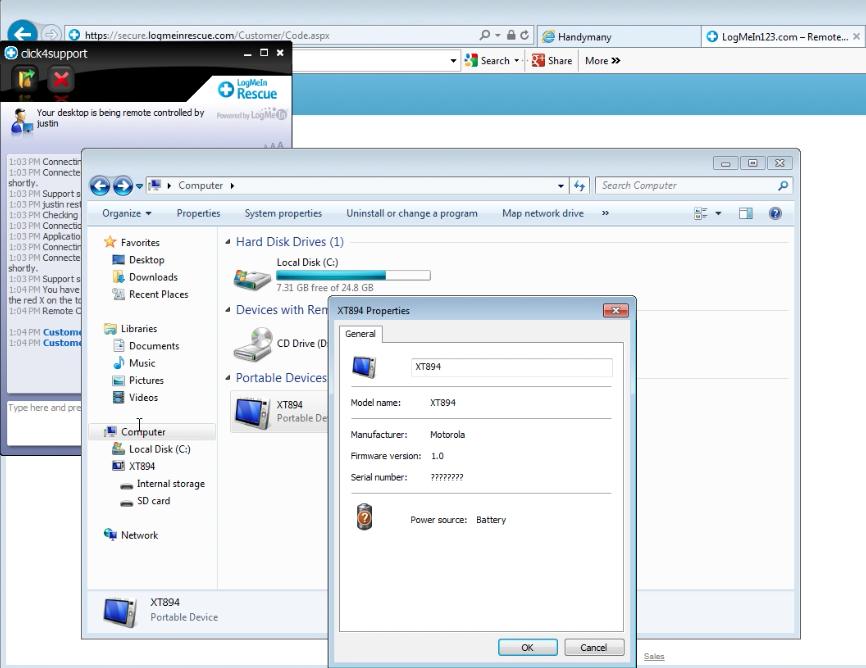
Figure 4: LogMeIn’s remote software allows technician to check my phone
Now what were they going to do once connected? Run some sort of a scan or diagnostic on our connected phone? This is the least I was expecting from any decent technician.
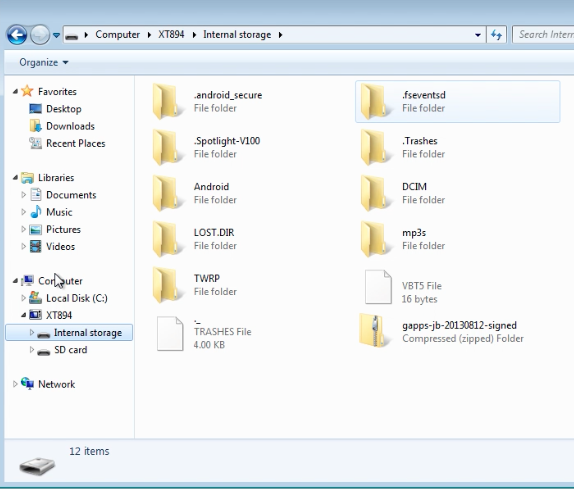
Figure 5: Browsing the phone’s internal storage
After checking the phone’s properties (Figure 4) and quickly browsing through its internal storage (Figure 5), they finally gave up and went back to their bread and butter.
Alright Sir. Just let me know one thing Sir. So when you are doing work on your mobile phone or on your computer ok, do you receive any kinds of pop ups for operation {inaudible} like Adobe Flash Player, or anything like Java as well as on your mobile phone?You get a pop up right? And you always connect your mobile phone with your wifi right?
So the thing is there are some kind of infection over here, so that’s why the infections transfer from your network to your phone ok?
You can probably guess where this is going if you are familiar with tech support scams. It’s far easier to get back to making up stories about Windows ‘errors’ than Android or iOS ones.
You know there is something really wrong when the technician asserts that:
There is one file which is installed in your computer as well as in your mobile phone and that is a very bad file. The name of that file is rundll ok? r-u-n-d-l-l number 32 dot exe alright?
Last time I checked, rundll32.exe was a standard Windows executable, so how could it possibly be installed on my Android phone since that uses a completely different operating system?
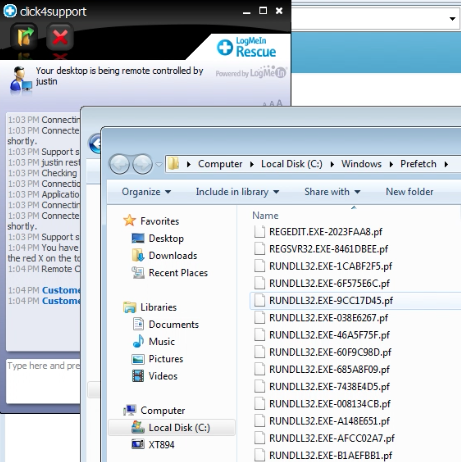
Figure 6: Windows Prefetch files
The Windows prefetch files are often used by scammers to make up non-existing threats. In this case the technician removed all the ‘infected files’ and simulated a ‘re-infection’ by quickly restoring them from the Recycle Bin (Ctrl+Z trick).
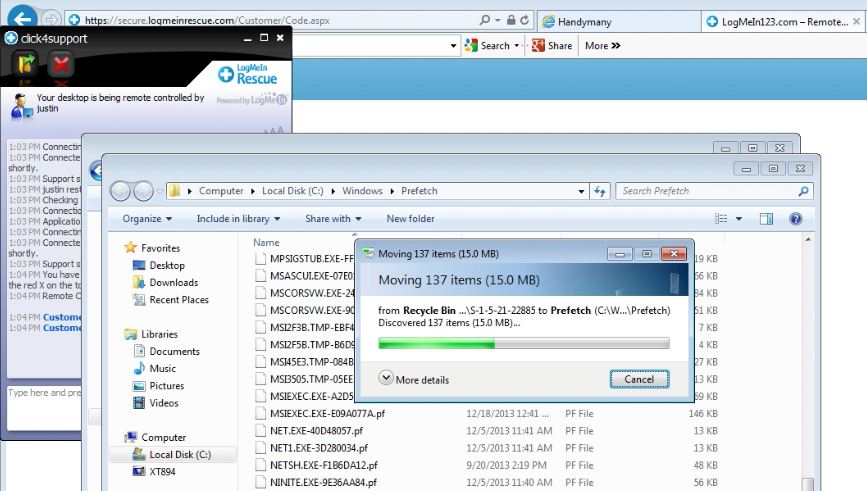
I’m going to delete all these files for you Sir…. and they’re all gone. But after very quick time the old files will come back automatically. Can you see that?
It’s quite hard to keep your composure when hearing such blatant lies. It’s not that the technician is poorly informed but he is in fact fully aware of what he’s doing and yet does not have a problem with it at all.
The scary thing is that many people that aren’t too tech-savvy will believe these words at face value and end up paying several hundred dollars for dubious services from rogue technical support companies.
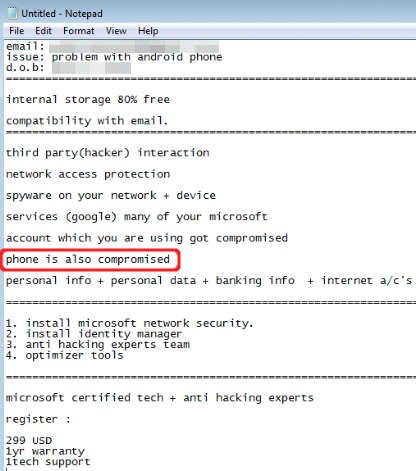
Figure 8: Invoice
Figure 9: Payment page
In this case the bill (Figure 8) was $299 for one year of so-called support. Not only is it a lot of money, keep in mind that those miscreants have direct access to your computer and data with all the risks that this entails.
I can imagine that in a near future those fake support companies will remotely access the phone or tablet directly because more and more people no longer own a ‘traditional’ computer.
The tech support scam lives on by adapting to its environment and exploiting the never failing human factor.
If you can stand listening to outrageous lies, feel free to watch the video segment for this scam.
For a complete guide on tech support scams, please check out our page here.
—
Jérôme Segura @jeromesegura










