I was digging through some recent Steam related phish pages, and came across something I haven’t seen before: a new way to steal Steam accounts while bypassing an additional security measure.
Typically a Steam phish page asks for username and password, like all phish attacks – often these can be foiled by enabling Steam Guard on your account.
What is Steam Guard?
When logging in on a PC you haven’t used before, Steam Guard will pop a window asking for a verification code which will have been sent to your email address. Without the code, you can’t log in. Scammers have come up with a somewhat novel way to try and get around this security measure.
How do they do it?
A potential victim will navigate to the phish page and enter their Username and Password.
At this point, they’ll be greeted with the following pop-up box:
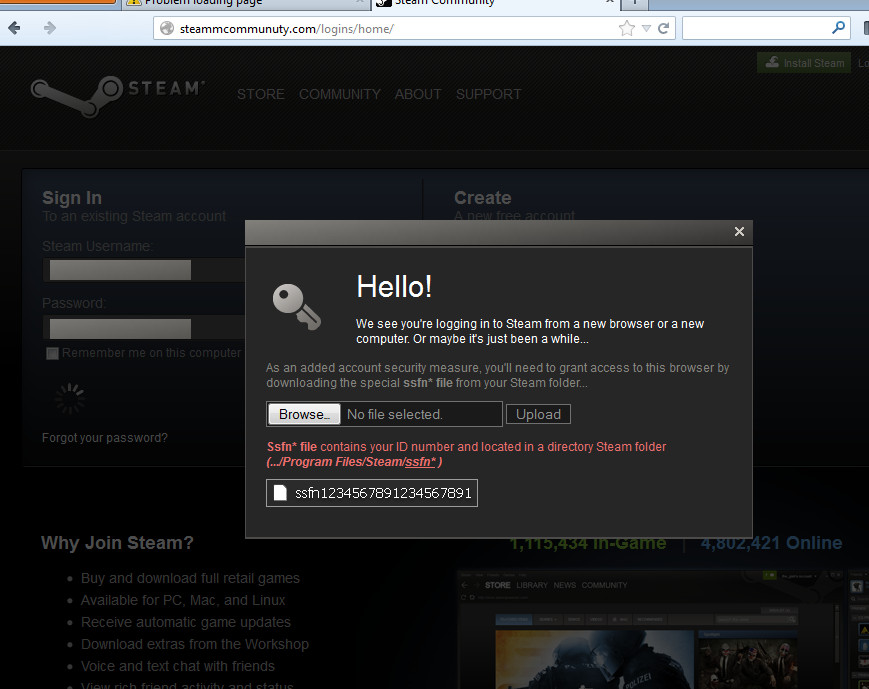
Looking very similar to the usual Steam Guard pop-up box, it says:
We see you’re logging in to Steam from a new browser or a new computer. Or maybe it’s just been a while…
As an added account security measure, you’ll need to grant access to this browser by uploading the special ssfn* file from your Steam folder…
Ssfn* file contains your ID number and located in a directory Steam folder (…/Program Files/Steam/ssfn* ) Sending this file to the scammer allows them to place it into their Steam directory and login as the victim while avoiding the Steam Guard security prompt asking for a verification code sent to the email address on file.
What is the SSFN File?
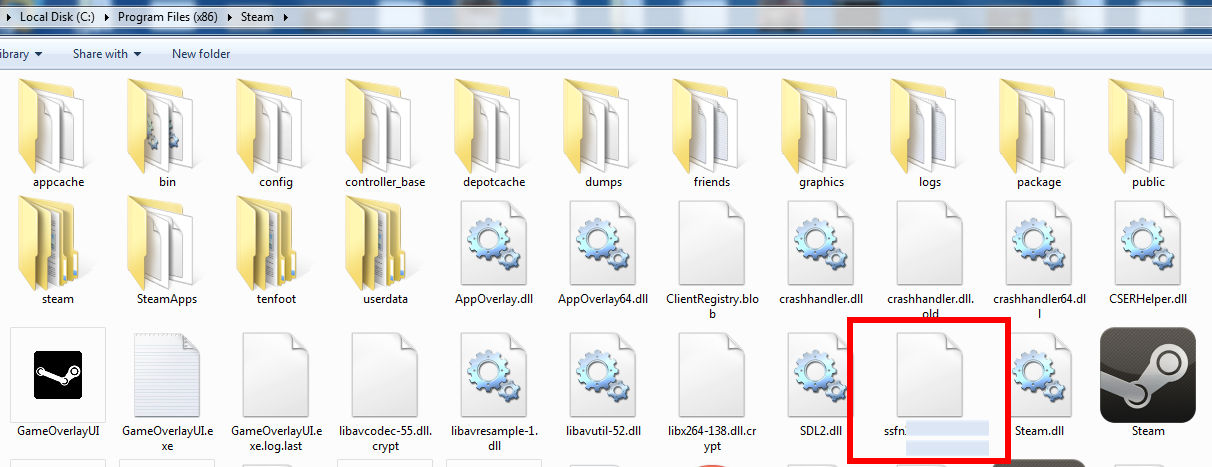
The SSFN file is the one that stops you from having to verify your identity through Steam Guard every time you login to Steam on your PC. If I delete mine, for example, I’ll have to go to my email account and dig out a brand new verification code sent to me from Steam.
After I’ve done this and entered the code, a brand new SSFN file is created in the Steam folder and I’m back to being protected by an additional layer of security. Here’s the file in question:
Testing, Testing…
We did some testing and can confirm that this technique – asking a victim to send their SSFN file to the scammer – does indeed work. In the below screenshot, we’re attempting to login to a Steam Guard protected account from a new machine / IP / location / everything else:
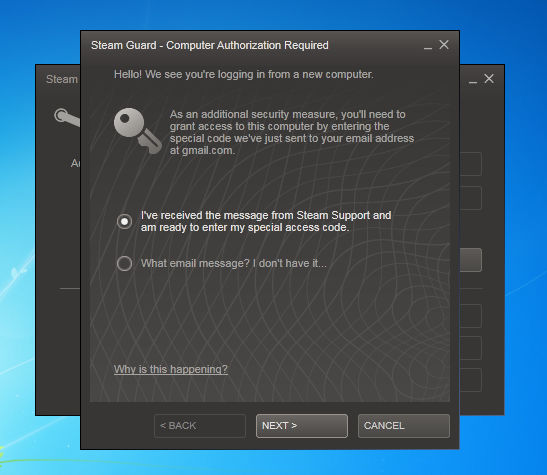
“Hello! We see you’re logging in from a new computer. As an additional security measure, you’ll need to grant access to this computer by entering the special code we’ve just sent to your email address”
At this point, the scammer would be foiled unless they also have access to the victim’s email account. However, let’s assume the victim here has sent their SSFN file via a phishing page. From there, we take the victim’s SSFN file, drop it into the Steam directory on the scammer’s computer, try to login again and…
Success! We’re in.
It seems this one has been around for at least a month or so – after a little more digging, we came across a thread on Reddit about it.
Compromised Steam accounts are big business, especially for those wanting to hijack accounts which have rare in-game items in their inventory (they’ll “trade” the items off to an account owned by the scammer, who will then go on to sell them for their own gain on the Steam Marketplace, buying games with the newly acquired funds in their Steam Wallet).
Not to mention, they can play all your games for free while logged in as you. Whoops!
While logged in as a Steam user, they’ll be able to see the victim’s purchase history, change current email address, current Steam password, disable Steam Guard, change the profile name and update the stored payment method (if any).
They can’t make purchases with the stored card because Steam requires you to re-enter the security code when making payments.
Steam themselves are aware of this issue, and the Steam forum mods are warning users that sending scammers their SSFN files will not end well [1], [2]. The forums themselves are stacking up a nice line in victims [1], [2], [3], [4], [5], [6], [7], [8], [9].
Here’s a screen one user posted of their support ticket detailing the game items they’d lost while being tricked into uploading their SSFN.
In one of those weird twists of fate, some mods had previously been advising users to copy their SSFN from one machine to another to avoid the 15 day trading delay when moving to a new machine. That desire for convenience has come back to bite some gamers in a way they probably couldn’t have imagined.
What can Steam do about this?
That’s a good question. The great thing about Steam is flexibility – if you want to switch between desktop and laptop in a hurry, it’ll let you. Steam Guard isn’t cumbersome, nor does it nag you or get in the way once you’ve authorised a machine.
And with some 65 million active accounts out there, scammers have a sizeable chunk of the global gaming population to pick and choose their targets from (according to Wikipedia, that figure is now at some 75 million, with 75 percent of all games being purchased on PC through Steam).
The moment they make Steam Guard more intrusive or tighten the security screws, they risk alienating gamers and the less appealing using the feature will become.
We spend a lot of time advising people not to download files from non-trusted sources, but it’s clear that we all need to start letting people know that sometimes uploading files to strange destinations can also result in a bad experience for all concerned (except the scammer, who is having a wonderful time in your copy of Half-Life 2).
Christopher Boyd (Thanks to Joshua for help with setting up the testing)










