[Update April 4, 2014 9:21AM PDT] Our friends at PhishLabs recorded and posted a video of a fake Google Drive and Docs phishing scam in action. Check out their post here.
Original story:
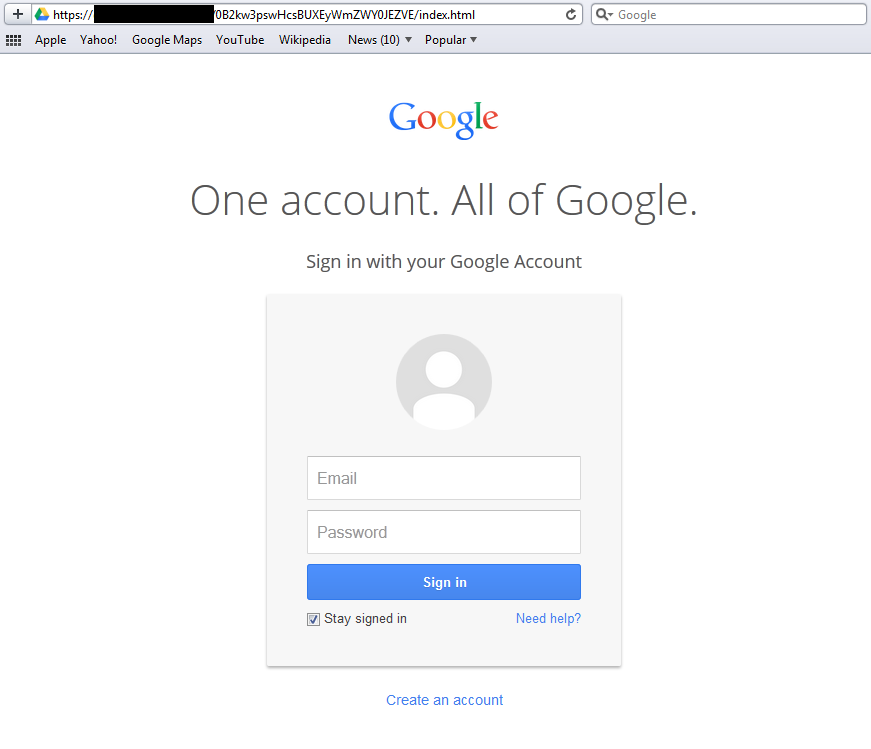
Every now and again, we read reports about phishing sites that look dangerously convincing—you can hardly tell the real one apart from the fake one anymore, unless you know what to look for and where. Our friends at Symantec found one such site some time in March.
The interesting bits about their find are that the scam page was actually hosted on Google’s server and sported an https scheme name in front of the URL, which is what a genuine Google URL normally looks like. These made spotting the phish page almost impossible for anyone attempting to access their Google Docs or Google Drive account.
There are several fake Google sites out there that may not look as compelling and sophisticated as the Symantec find, but I have no doubt that these sites would have their share of victims, too.
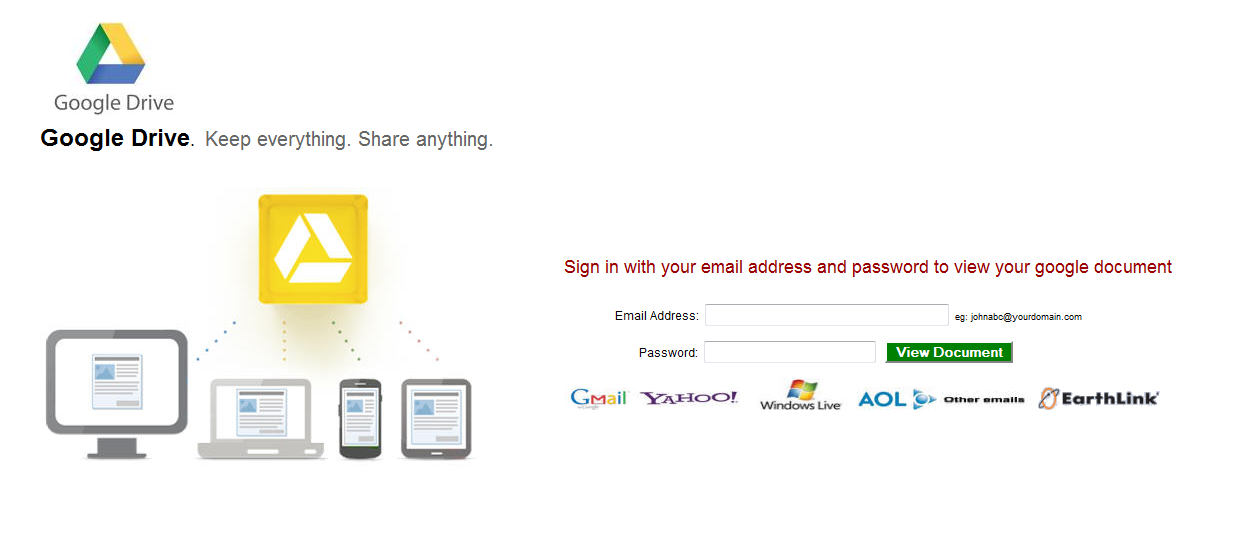
Sample of a Google Docs phishing page in the wild
Our research has led us to a fresh Google login clone that has the same interesting bits I mentioned above; however, not only does this page cater to stealing credentials but also on the downloading of malicious payload.
Users of our products are protected from this web threat as Malwarebytes Anti-Malware already detects asdf.exe and its duplicates as Backdoor.Bot. This executable has a VirusTotal rating of 16/51 as of this writing.
The phishing page in question contains code that allows it to identify the browser type used to access it. It pops up an overlay message notifying the user that he/she needs to download a supposed set-up file in order to update their browser (and perhaps eventually the “outdated plug-ins”).
We have observed that the overlaying only works on selected browsers, particularly Internet Explorer, Chrome, and Firefox. If you may recall, these are the top three most used browsers worldwide.
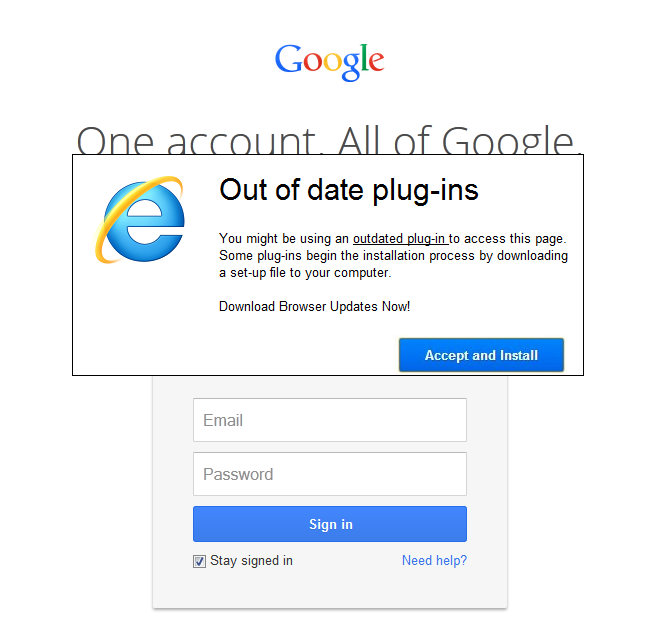
Phish page accessed via IE (click to enlarge)
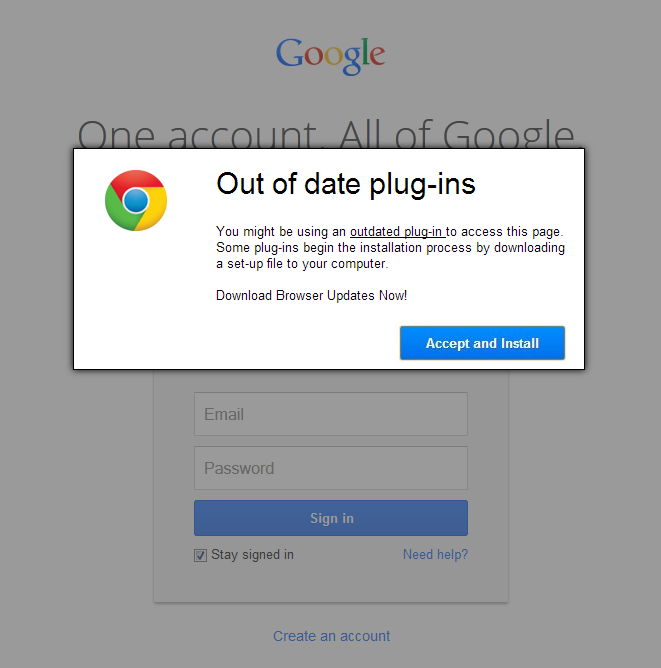
Phish page accessed via Chrome (click to enlarge)
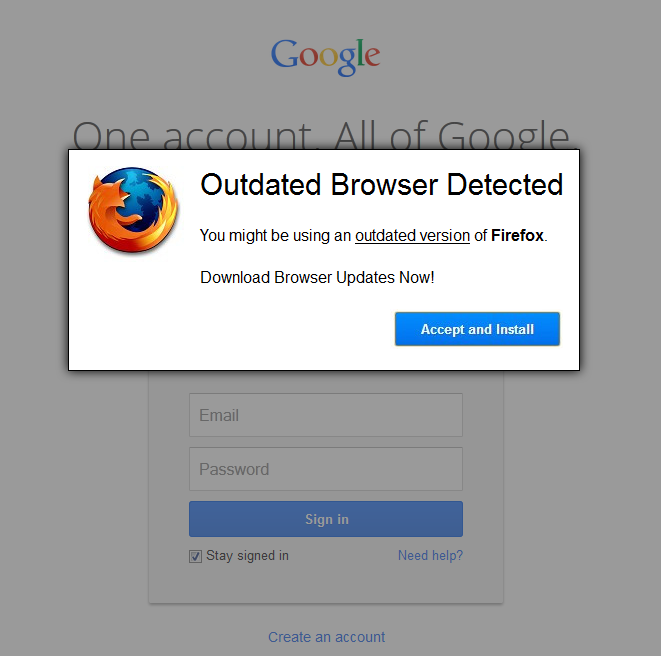
Phish page accessed via Firefox (click to enlarge)
Once Chrome and IE users click “Accept and Install”, Chrome_Plug-in_EN-US_WOL_WIN.exe and Internet_Explorer_EN-US_WOL_WIN.exe are downloaded onto their machines, respectively. These files are actually duplicates of each other.
For Firefox users, the scenario is quite different: instead of an executable file, they are asked to download a browser add-on or extension named addon.xpi from a publicly accessible Dropbox folder.
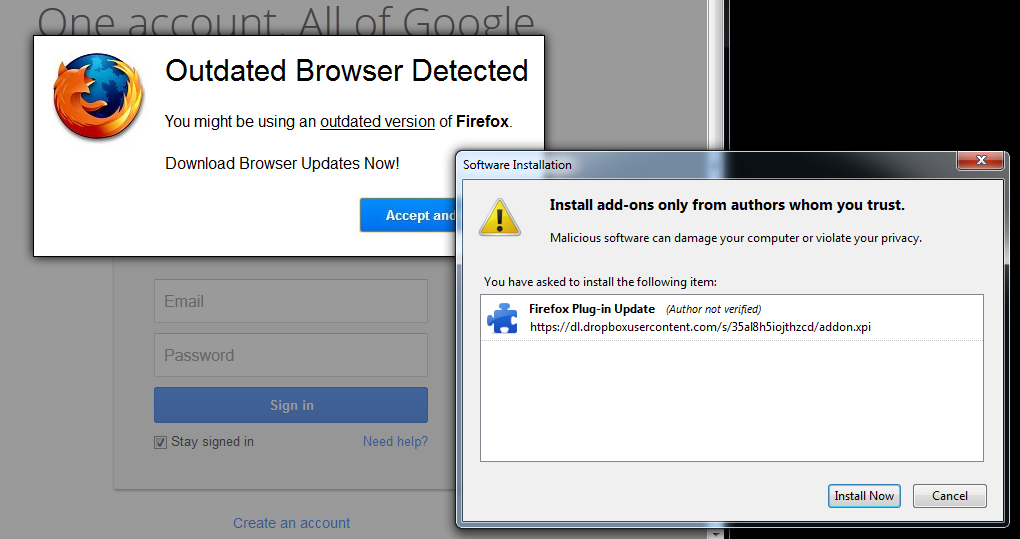
The said .XPI, once expanded, contains the executable file, asdf.exe—another copy of the IE/Chrome download file. The JavaScript file, which is contained within the package, consists of instructions that run the malicious executable at the same time as the add-on is being installed.
Finally, this extension uninstalls itself from Firefox, thus, restoring the original state of the browser before the user encountered the phishing page. The system, however, is already infected by a malicious payload without the user’s knowledge.
Although the downloading of malicious payloads cannot be replicated on the side of users who normally make use of Safari, Opera, or other browsers, we urge them to keep their guard up.
The phishing page can and will fool users into thinking that they are logging on to their Google Drive accounts if they’re not careful. It’s no longer enough to see https on the address bar and think it’s the real thing.
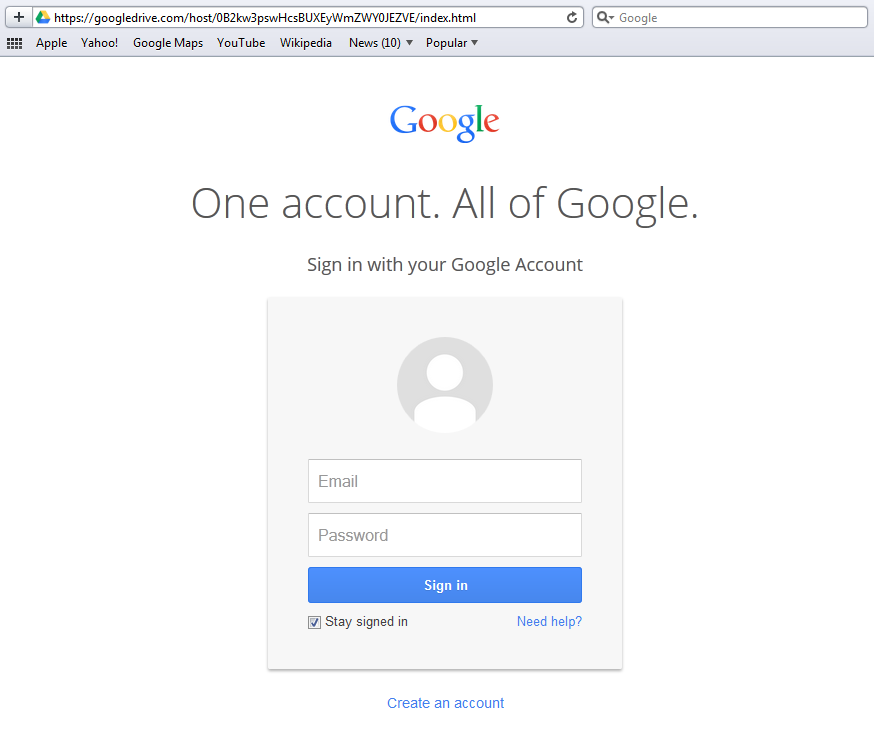
Eyes open, everyone.
Jovi Umawing