Over the last few weeks I have described numerous methods of phishing attacks and a few examples what they do or may look like. In this final installment, I will shed some light on how phishing attacks are done and a few real world examples of techniques used by Phishing scammers. Finally, I will discuss why phishing is still so popular and not only how you can protect yourself but how you can help protect others too.
How it’s done
Most cyber-attacks which are aimed at either gaining access or stealing information are fairly difficult and require a decent level of technical knowledge; this is not the case with Phishing however. Phishing attacks are incredibly easy to both setup and execute. It really only requires a light amount of technical know-how and the ability to do some research as well as think up possible reasons for people to blindly click a link or give up their user credentials.
Tools
While manually setting up Phishing attempts is simple enough, it can be even more streamlined with the use of tools which make the job easier for a would be scammer. These tools will copy legitimate web pages for you; they will generate fake emails or be used to collect email addresses to send phishing attacks to. In addition to actual software tools, there are numerous tutorials and walk-throughs all over the internet which describe, in detail, how to setup a phishing attack and the best way to execute it on a large group of people. With these resources available to anyone with the will to perform this type of attack, it’s no wonder that phishing attacks are one of the biggest problems facing computer users today.
Pay Pal Example
A few years back, I had heard about buyer scams on sites like Craig’s List and decided to see what kind of attacks I might be able to summon on my own. So I put up an ad for one of my laptops and waited to see what kind of responses I would get. Well it turns out I got a lot of them, appearing to be from all kinds of people, I responded to many of them and they all had the same story:
Buyer: This laptop is for my friend who lives overseas, can you just send it to him. Me: Sure Buddy! Buyer: Ok well as soon as I get the confirmation that you sent the item, I will send the money through Pay Pal, don’t worry though, you should be getting an e-mail soon from PayPal saying that I am bound to this agreement. Me:……Okie Dokie.
A short while later I would receive such an e-mail from “service@paypal.com” with all the appropriate information. I couldn’t help but be a little suspicious so I began to investigate the e-mail:
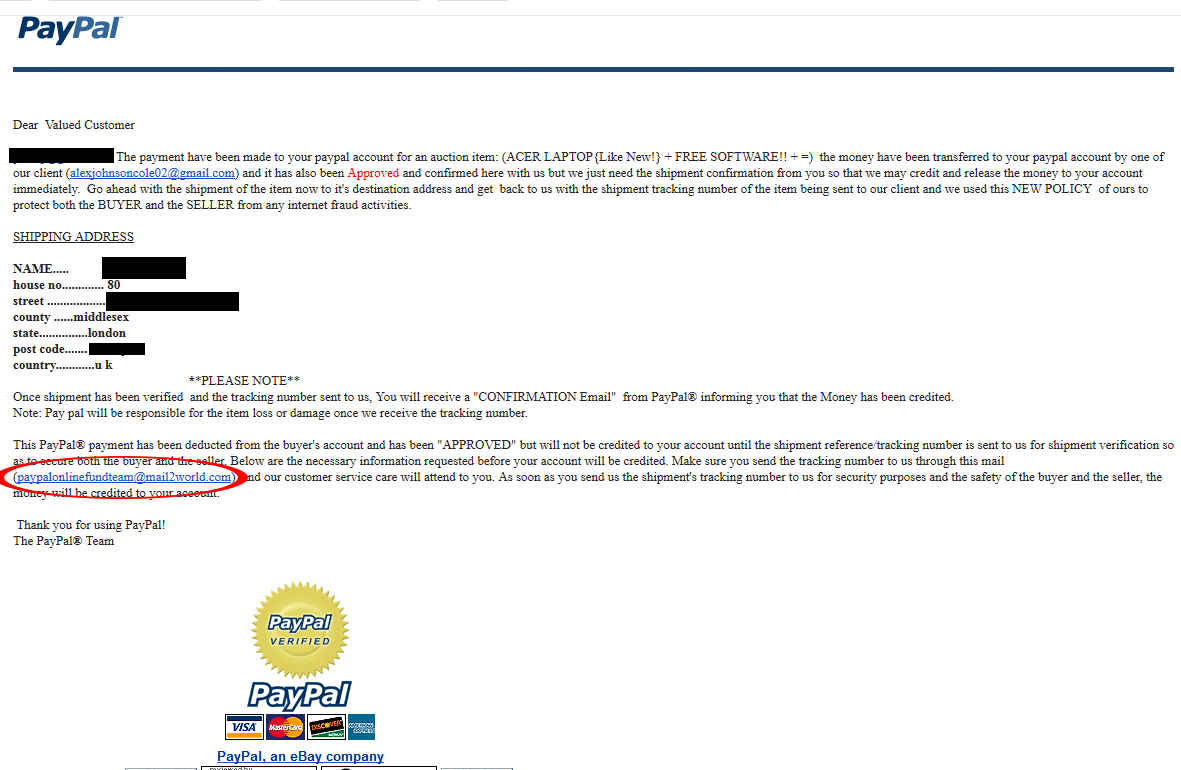
The first thing that tipped me off to something being wrong was the use of the email address “paypalonlinefundteam@mail2world.com” as a link in the text. I thought that it was odd that PayPal was using a domain for their email that wasn’t ‘paypal.com’. So I checked out Mail2World.com for investigative purposes:

Wait…Free E-mail hosting service? No no no! This is all wrong! I decided that since this looked a little too “phishy”, I needed to make sure that this e-mail is actually coming from PayPal and not being spoofed:
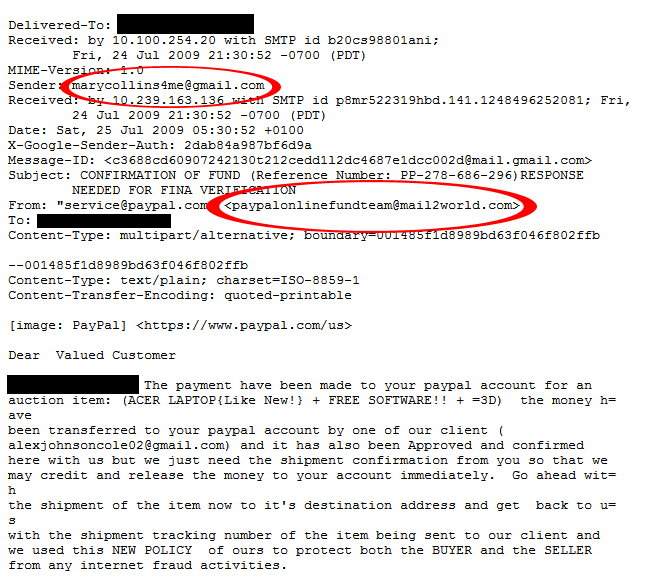
Ok, why is a PayPal email coming from this Mary Collins person? Also, it turns out that the legitimate email address of “service@paypal.com” was only the display name for the Mail2World account! The jig was up and so after a few emails grilling the attackers about their sloppy attempts at tricking people, I reported the addresses to PayPal and Craigslist and went on my happy way. Another possible way to call out illegitimate email headers is by checking the ‘Received’ lines in the header and finding out where the e-mail apparently originated from and how it traveled. Scammers will often modify this field to make the e-mail appear even more legitimate. A great tutorial on how to check for this type of scam as well as other useful tips can be found on the blog of one of our Researchers, Steven Burn:
Decoding the Spam: From Head to Eternity
So why am I mentioning this in a blog post about Phishing? Well email spoofing is one of the most commonly used tricks that Phishers use in order to trick the user into believing that the e-mail is legitimate.
Security Tip: Always mouse over any links in an e-mail to identify their destination. Also, if you are suspicious about the source of an e-mail it doesn’t hurt to check the message headers. You can do this by clicking on “Original Email” or “Source” or whatever option your email client has to see the mail headers.
Why is it still around?
Phishing attacks have been around for years and they will continue to plague users for years to come. While most cyber-threats seem to vanish into the void after a few years because of security patches, phishing is ‘unpatchable’ because it attacks the user, not the system. The best chance a user has is learning how to spot and avoid the attacks.
How can you help others?
So you might not be a member of the computer security community but you still want to help people avoid being victims of these attacks. There are numerous methods of accomplishing this but the simplest way would be to check out PhishTank.com. PhishTank.com is a site devoted to discovering and shutting down phishing pages and while they have a unique automated system to find phishing pages and a determined group of researchers who provide them with this information, they can’t cover everything and you can help them out by submitting the URL provided in your phishing email so they can check and confirm as to whether or not the site is legitimate or not. This is also a great way to double check a shady e-mail before you click any links.
How can you protect yourself?
To reinforce what I advised the last few weeks:
Phishing Attacks can fail by simply keeping an awareness of computer security practices in your mind whenever you check your email, read Facebook posts or play your favorite online game. Here is a list of a few of the most important tactics to keeping your information safe:
- Don’t open e-mails from senders you are not familiar with.
- Don’t ever click on a link inside of an e-mail unless you know exactly where it is going.
- To layer that protection, if you get an e-mail from a source you are unsure of, navigate to the provided link manually by entering the legitimate website address into your browser.
- Look out for the digital certificate of a website
- If you are asked to provide sensitive information, be sure to check and make sure that the URL of the page starts with ‘HTTPS’ instead of just ‘HTTP’
- This is important not only for securing yourself against phishing attacks but also, ‘HTTP’ can be intercepted by hackers watching your network connection.
- If you suspect the legitimacy of an e-mail, take some of the text or names used in it and type it into your search engine to see if any known phishing attacks exist using the same methods.
- Obtain ‘Password Manager’ tools which can auto-fill login information for you, if you navigate to a page which you had been to before, the fields should be filled in. If they are not, you may be on a phishing page.
Conclusion
In this third and final installment of the Phishing series, I gave you some insight into how phishing is done as well as an example of real world methods used and how to call them out. I hope that if you do decide to help out with the never-ending fight against phishing, that you submit URLs to PhishTank.com or any other service which fights against this attack. It is also important to not only keep this information for yourself but inform your friends and family so they aren’t compromised by an easy to avoid attack. Always be vigilant and always be suspicious whenever you sit down in front of a computer, doing so might save you or others from losing data, money or your identity.











