
So You Want To Be A Malware Analyst
Adam Kujawa
In war, there are always two sides: the attackers and the defenders. A less focused on group is the researchers and developers. While soldiers are fighting a war on the front lines, scientists and engineers are researching and developing new weapons, defenses and tools; things that give their side an advantage. If one of these such creations is ever captured by the opposing forces, it is reverse engineered to understand exactly how it works, how it can be defended against and even how to re-purpose it. The same goes for war on the cyber front, malicious attackers and system administrators (Black and White Hats) are the soldiers, malware authors develop new and dangerous forms of malware and Malware Analysts reverse engineer these weapons to find out how to stop them.
What is a Malware Analyst?
A Malware Analyst is a highly specialized reverse-engineer, programmer and detective. They accomplish their task by using various tools and expert level knowledge to understand not only what a particular piece of malware can do but also how it does it. Becoming a Malware Analyst requires a large amount of focus and discipline as well as training and practice of the inner workings of computer systems, programming methodologies in multiple languages and a keen mind for solving puzzles and connecting the dots.
You might consider becoming a Malware Analyst if you have a passion for computer security, enjoy solving puzzles and like the prospect of always learning new things. You might also enjoy it if you prefer a profession that always poses a challenge or if you look forward to working on new and interesting things. No day is ever the same as the previous, everyday is an opportunity to learn something new and fine-tune your skills. In addition to the personal satisfaction you would get from being a Malware Analyst, you would also become a samurai in the fight to make the cyber world a safer place.
The type of person who would be perfect for becoming a Malware Analyst would be:
- A fast learner
- Able to derive meaning from nonsense
- A good puzzle solver
- Able to think outside of the box
- Willing to frequently use the scientific method
- Resourceful
Prerequisites
Prior to walking the path to become a Malware Analyst, a person should be familiar with:
- Operating System Concepts
- High Level & Low Level Programming (familiarity is fine, working knowledge not required at first)
- Fundamentals of networking
- How to use the internet to perform research
Building the basics
Being a Malware Analyst can take you many different places during your career and you can end up analyzing all types of malware, from normal application malware to exploits hidden in PDF files or malware found on smart phones. So where should you start when it comes to your training? You should master a few basics before trying anything too advanced:
Learn Assembly Language
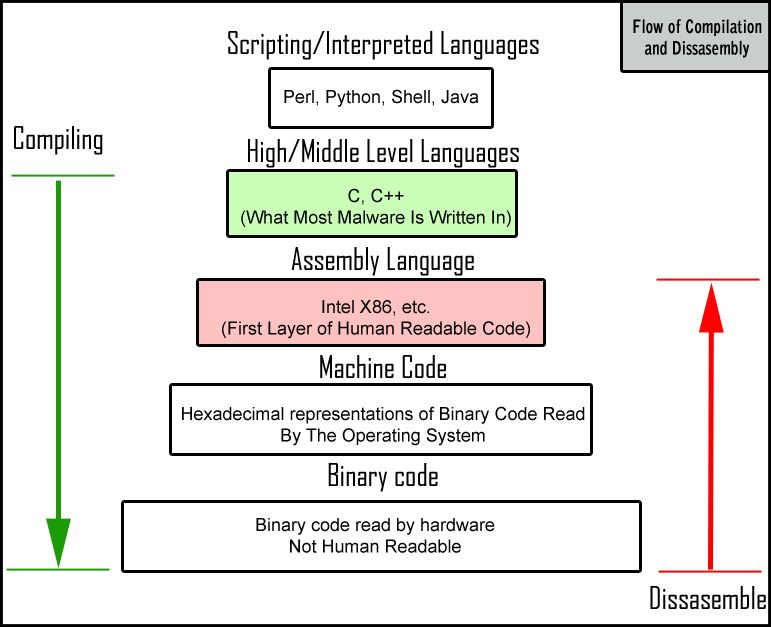
In the hierarchy of programming languages, you have at the very top scripting languages like PERL or Python, followed by high and middle level languages like C++, C. Followed down by Assembly language, machine language and finally binary code which is read by the hardware.
Most malware is written in a Middle Level language and once the code is completed, it is compiled all the way down so it can be read by the hardware and/or operating system. At this level, the code is not “Human Readable” or easily read by human eyes. In order for a Malware Analyst to be able to read the malware code, they will need to disassemble it. Unfortunately, the highest language derived from binary code is Assembly, which is the last level of human readable code. Therefore, it is imperative that a would-be Malware Analyst, also learn how to read and write Assembly code.
Assembly language is low-level and therefore involves many more instructions than you would see in a higher-level program. For example, the code required to print something in the console in a higher-level languages is usually just one line and sometimes just one symbol. In Assembly, this simple procedure may require anywhere from 5 to 20 lines of code.
Analysts Tip: Learning Assembly is easy if you already know a higher-level language, imagine what the operating system needs to do in order for a single function call to execute, this is what you will see in Assembly. By learning shortcuts to parsing Assembly, you will find what you are looking for much faster.
Learn how to use the tools
As a construction worker needs to know how to use a hammer and a mechanic needs to know how to use a wrench, a Malware Analyst needs to know to work their own set of unique and powerful tools. Some tools are easy to use and some are not, some have clear output and some dump you with lots of data that you need to be able to parse. The tools of a Malware Analyst are incredibly important and usually one of the first things learned. Here is a list of the types of tools required and some examples of them:
- Disassembler – IDA Pro
- Debugger – OllyDbg, WinDbg
- System Monitor – Process Monitor, RegShot. Process Explorer
- Network Monitor – TCP View, Wireshark
- Packer Identifier – PEID
- Unpacking Tools – Qunpack. GUNPacker
- Binary Analysis Tools – PE Explorer, Malcode Analysts Pack
- Code Analysis Tools – LordPE, ImpRec
Once you learn how the tools work and what you could do with them, your quest in analyzing malware will become easier and easier. Also, keep in mind that while you might originally learn how to use a specific suite of tools, new tools are being developed all the time that might be more helpful in both their design and function.
Learn about malware
Learning about malware might seem a bit redundant when you are training to become a Malware Analyst; however, it is a very important aspect of your training. Malware evolves and changes every year, it uses new methods to infect as well as operate and sometimes brings back old methods if they are applicable again. If you were writing a program to play Tic-Tac-Toe, you could try to write it from scratch, or you could see how other people have written it before and get an idea of what you need to do. The same applies for malware analysis; reading white papers and analysis reports about different types of malware will give you an idea of what you might be seeing while reversing.
Process injection is a method that malware uses to hide its operations, it must go through a set of functions in order to perform this technique and it is important that you be able to identify it happening in the code based upon prior experience and knowledge about how malware works. Research, practice, knowledge and experience are key to being able to effectively analyze new malware and should be the staples of your Malware Analyst training.
Helpful Links and Sources
There are many different ways to learn about becoming a Malware Analyst; some people choose to go through courses taught online or in person, which can cost upwards of a few thousand dollars. Other people choose to learn as they go, picking up information where they can and learning from their own experience. Both are decent ways of learning about malware analysis but the cheap and easy way would be through doing online research and reading lots of books. Here is a list of my favorite sources for learning about malware analysis:
Online Sources:
- Sans.org and anything by Lenny Zeltser
- Google Searches for “Malware Analysis”
Books:
- Malware Analyst’s Cookbook
- Rootkits: Subverting the Windows Kernel
- Practical Malware Analysis
- The IDA Pro Book
- Reversing: Secrets of Reverse Engineering
Conclusion
Whether it is to start a new career or just simple curiosity, learning about Malware Analysis can be a very challenging and rewarding path. It can test your patience, concentration and sometimes even your temper, but the payoff when you have been working on a file for hours and finally come across the key function or piece of data you were looking for, cannot be duplicated by anything else. The future holds a war between those who use malware and those who fight against it and as technology advances, so too does the methods in which malware authors write programs to exploit and control it. The next generation of malware fighters will require a more advanced knowledge than ever before they will be the cyber samurai.



