UPDATE: As of 1/28, the Facebook page for Malwarebiter appears to have been deleted.
Overview A few days ago Malwarebytes Intelligence Analyst Adam Kujawa released a Cyber-Threat Advisory on a fairly new anti-malware product on the web called “Malwarebiter”. This product grabbed our attention because of its similar name to Malwarebytes. After taking a look at the two products, it’s easy to instantly notice similarities between the two, below are just a few:
| Name: | Malwarebytes | Malwarebiter |
| Slogan: | “Taking the Byte out of Malware” | “Bite down on Malware” |
| Price: | $24.95 | $24.95 |
| Website: | Blue theme | Blue theme |
Various reports on the web suggest this advertised anti-malware product has been around since at least May 2012, while its Facebook page appears to have been created just last month. Facebook users will notice the software claims to have received an award for being the “World’s Best Anti-Malware Software”.
Malwarebiter Facebook Page
Furthermore, its Facebook page has some 26,000 likes, a rather high number for only being a month old but not completely unrealistic. Since Facebook keeps record of users talking about topics and stores the data, our team looked at Malwarebiter discussions on the social media giant. The results were interesting. Here is a graph showing the history of users talking about Malwarebiter on Facebook. Our company’s data is provided to the left just to show our readers what a typical graph might look like.
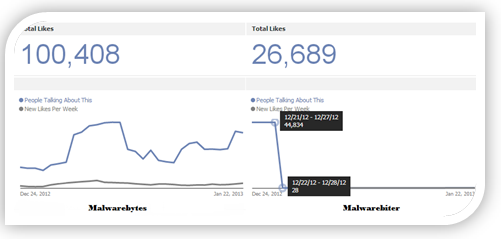
Facebook showing strange community data on Malwarebiter
As seen from the Malwarebiter graph, the number of people talking about the product started at nearly 45,000 on 12/21/2012, and then flat-lined to a mere 28 the next day. These sharp differences are highly indicative of spamming and perhaps other forms of foul-play. Considering these facts, our analyst team decided to visit the company’s site and see what the alleged “world’s best” protection looked like. Their entire site took us less than a minute to navigate and doesn’t have a lot to see, only an apparent rip-off of our company’s product. Afterward, we took a look at data captured from our visit.
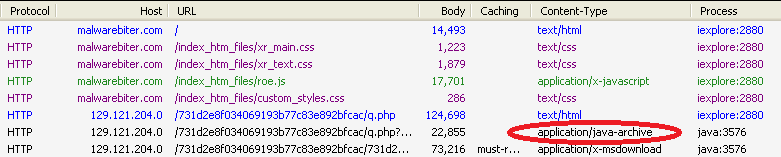
Malwarebiter.com – Behind the scenes Traffic analysis from our visit revealed “roe.js”, a file containing javascript. Upon further inspection the file revealed an embedded iFrame object that links to a rogue IP hosting the Blackhole Exploit Kit, a somewhat funny outcome to visiting a supposed anti-malware site.
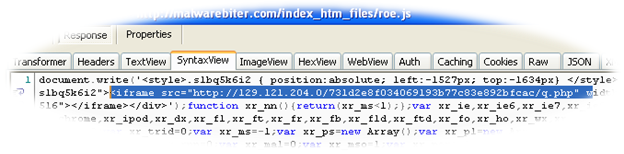
roe.js – Malicous javascript file
In case our readers aren’t familiar with iFrames, these allow web developers to embed the contents of one webpage within another. Using iFrames for drive-by malware attacks is common since they can be crafted invisible to the naked eye. Malicous iFrames often redirect users to malware URLS unbeknownst to them, as seen frequently in Blackhole, Crimepack, and other exploit kits.
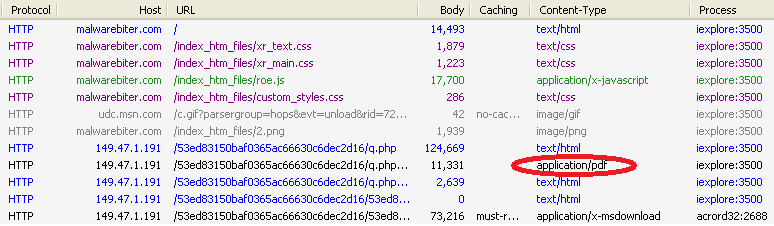
The “roe.js” file seen in the image executes either a java or PDF exploit, which downloads a malicious payload to the visitor’s PC. The java exploit has been identified as CVE-2013-0422, posted recently as a CTA in our Unpacked blog, and the PDF exploit was identified as the notorious libtiff integer overflow as seen in CVE-2010-0188. In addition, a malicious file is served to visitors after the exploit; this was identified by our intel team as the infamous Zeus botnet after observing packets from the malware making requests for “gate.php”.
Java Exploit:
PDF Exploit:
Malicious payload (Zeus):
It’s clear based on the evidence that malwarebiter.com is delivering web exploits to its visitors and spreading the popular Zeus botnet. After viewing the product’s website, our team decided to head over to the downloads page and check out the Malwarebiter scanner.
Malwarebiter – Scanner Review The installation is pretty straightforward and doesn’t raise a lot of flags. After installing and skipping through some annoying dialogs, you’ll arrive at the program’s main screen. Our analysts ran a “Smart Scan” to see if it found anything on the host. As predicted, the software doesn’t appear to find anything too relevant, including our newly acquired Zeus bots. Here is what it did find:
- Various cookies
- A CoolWebSearch false positive
- The WinPcap Dll
The file wpcap.dll is for WinPcap and is required to run Wireshark on Windows. Some scanners pick up this file because it’s argued that it could be used for malicious purposes. However, the other detection of “CoolWebSearch” is entirely a False Positive. Malwarebiter states that the registry value “Tries to lock you out of certain parts of your computer so that you cannot remove malicious software.” Whenever you report a false positive through the program’s interface, it asks for additional info, and then requests data from www.ad-purge.com. Ad-purge is reported as a fake spyware remover and has a very similar interface to Malwarebiter.
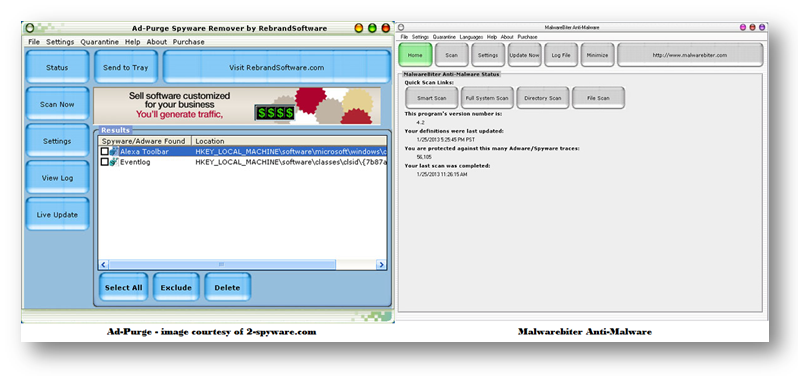
Comparison of Ad-purge and Malwarebiter interface, displaying many similarities.
Malwarebiter also has a button to update its definitions database, but to our surprise it doesn’t even require an active internet connection (it is the world’s best, after all). The following network request was observed when updating the program’s definitions.
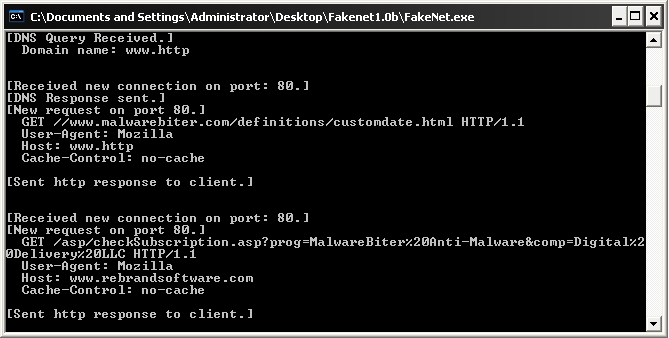
Malwarebiter program contacts rebrandsoftware.com domain
When visiting rebrandsoftware.com our intel analysts found they create software products to sell to private buyers, who in-turn resell the product as if it were their own (thereby “rebranding” it). Below is a statement from their site.
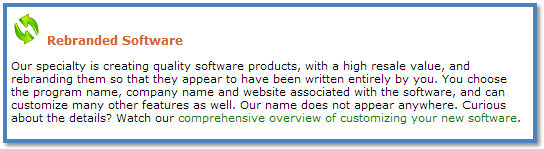
Description of rebrandsoftware from website
Interestingly, Malwarebiter and Ad-Purge both contact rebrandsoftware.com, and numerous pieces of malware have also been discovered contacting this domain. At face-value it appears that Malwarebiter and Ad-purge are both fake programs developed by this vendor. In addition, this isn’t the first time Malwarebytes has had issues with this domain, so we would caution our readers before considering the use of any software from this supplier.
Conclusion It’s vital to protect yourself from software exploitation at all angles, as detailed in a recent Unpacked article by Jerome Segura. Protection from these exploits will prevent further infection from malware to your PC. The java and PDF exploits found on Malwarebiter’s website could be prevented by keeping your software patched and up to date. However, this doesn’t always solve the problem, as both Java and PDF viewers are highly-targeted for exploitation, with new vulnerabilities discovered every day. In light of this, users might want to stop using java altogether, at least in conjunction with less-secure web browsers, like Internet Explorer. As for protection from malicious PDFs, there are alternatives to Adobe’s reader that exist, such as Foxit, but this product still has its own vulnerabilities. Users might be better off viewing their PDF documents in secure browsers, like Google Chrome.
Also, it’s imperative for our readers to understand the greater danger posed from Malwarebiter and other scams like it (and there are plenty). These fake programs put users at an even higher risk of infection as they offer virtually no protection. Even worse, some alleged security products infect your PC with malware when installed, or in this case, simply visiting the product’s website.
PC users should consider carefully before making the choice on Antivirus/anti-malware software. Here are some tips when choosing reliable solutions.
- Choose a product that’s well-known in the Computer Security industry.
- NEVER pay for a product until you try it.
- Be wary of products that make bold claims without quantifying data to back it up.
- Verify that detected malware is in fact malware.
If you’re looking for a place to start, here at Malwarebytes we offer Malwarebytes Anti-Malware (MBAM) in a free version. MBAM is updated multiple times daily and offers the latest in cutting-edge malware detection. Head over to our product comparison page for more information.
Thanks to Adam Kujawa, Jerome Segura, and Steven Burn for additional research material and input.
_______________________________________________________________________________
Joshua Cannell is a Malware Intelligence Analyst at Malwarebytes where he performs research and in-depth analysis on current malware threats. He has over 5 years of experience working with US defense intelligence agencies where he analyzed malware and developed defense strategies through reverse engineering techniques. His articles on the Unpacked blog feature the latest news in malware as well as full-length technical analysis. Follow him on Twitter @joshcannell