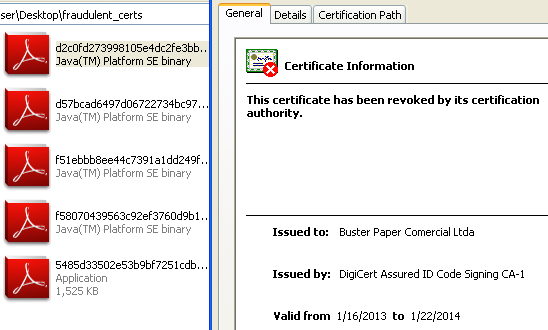
Update (Feb 6th): The digital certificates have been revoked by DigiCert.
Update (Feb 4th, 3:44 PM): Egnyte has promptly taken down the illicit account following our call. However, digital signature is still in use.
In the past few days we have heard several stories about major corporations getting hacked and their security systems completely bypassed. If anything, that should remind us of how vulnerable our data and privacy are. The fact of the matter is that there are so many angles one can get exploited that at the end of the day it can leave us wondering what or who to trust.
Take, for example, digital certificates which have been in the spotlight after Stuxnet used some or after Adobe’s servers were breached to sign malware. The purpose of a digital signature is to guarantee the authenticity of a file from a particular vendor and is provided by one of a few certificate authorities.
Well, we just spotted a new malware sample (Brazilian banking/password stealer) which happens to be signed with a real and valid digital certificate issued by DigiCert:
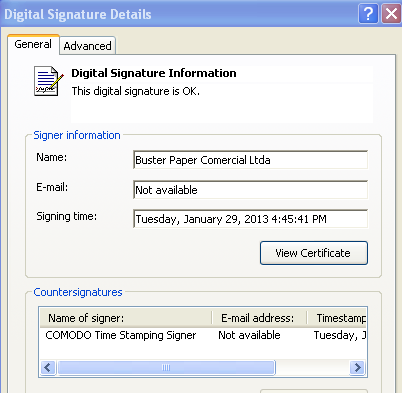
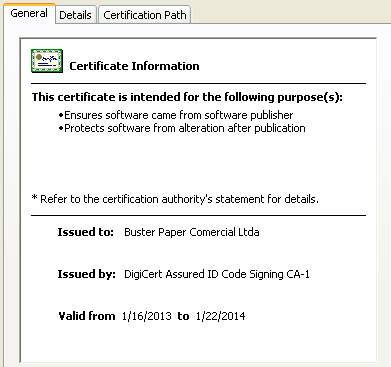
This certificate is issued to a company called “Buster Paper Comercial Ltda”, a Brazilian company that actually does not exist and was registered with bogus data:

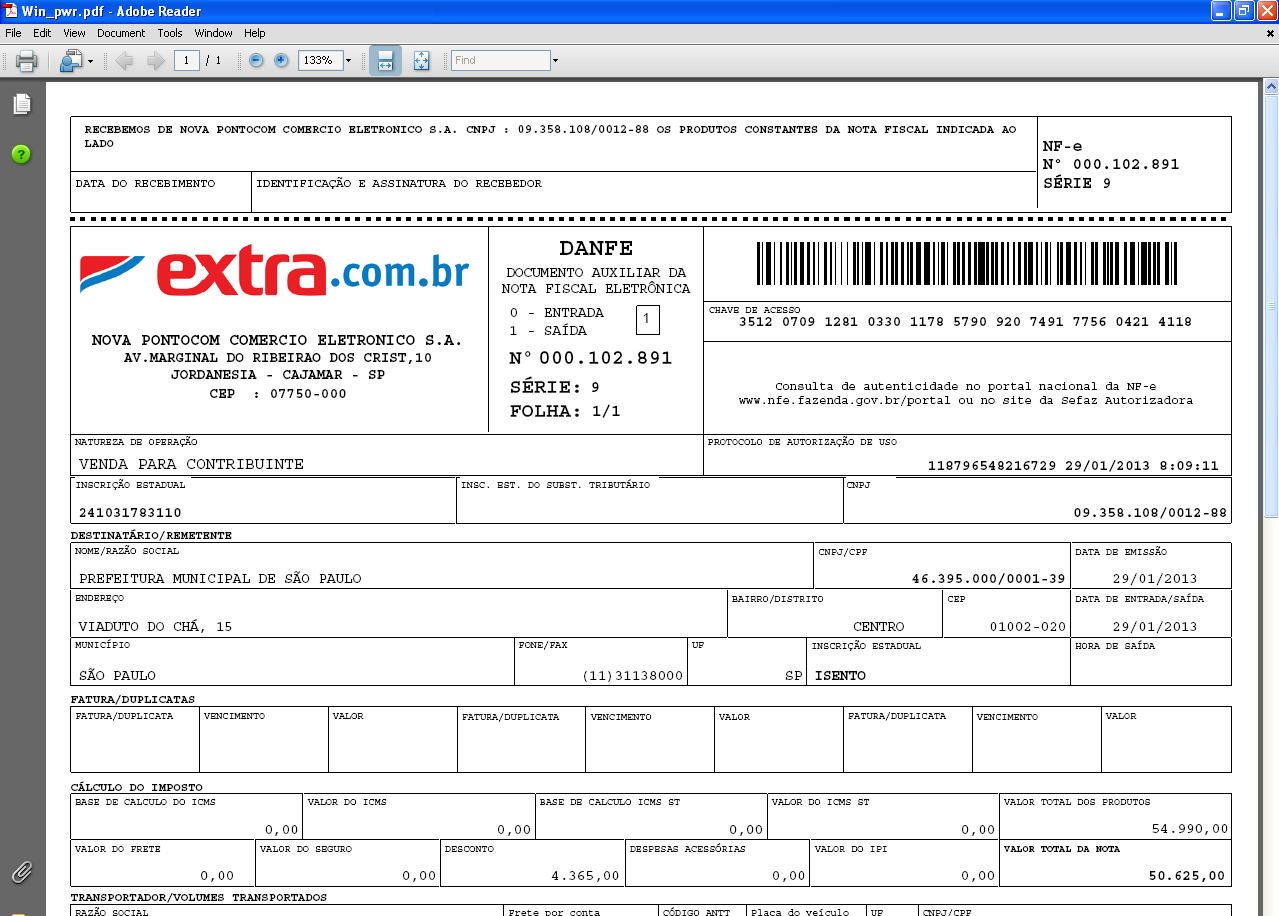
The file – disguised as a PDF document (an invoice) – actually opens up as such to really fool the victim:
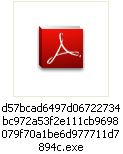
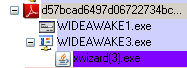
But what is really going on here? Let’s have a look, here are the new processes created:
and HTTP traffic:
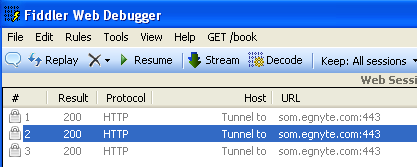
Let’s pause for a moment on where the malware connects to: som.egnyte.com
This is a sub-domain for a Cloud storage company focusing on file sharing for the Enterprise. They were unaware that their services have been used to host malware (which is against their Terms of use). The fake PDF document downloads additional payload stored on this server:
- hxxps://som.egnyte.com/h-s-internal/{redacted}/f3487f359b38436f
- hxxps://som.egnyte.com/h-s-internal/{redacted}/d3669545621045d9
These files are banking Trojans that are very large (over 10 MB unzipped):

No pun intended, but size matters as many antivirus scanners have trouble with detecting larger files.
Digging a little deeper, this is not a new case at all. In fact, last November the same kind of digitally signed Trojan was also distributed (See this ThreatExpert report for proof). Its certificate has, since then, been revoked:
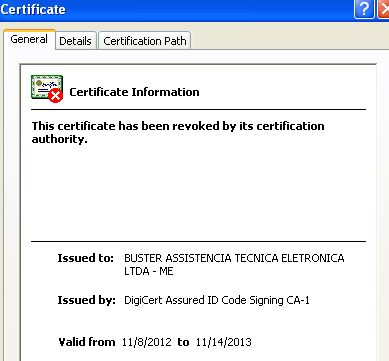
What we have here is a total abuse of hosting services, digital certificates and repeated offenses from the same people. Clearly, if digital certificates can be abused so easily, we have a big problem on our hands.
Digital certificate theft can be used in targeted attacks as a spear phishing attack for example. As we know, one of the weakest link in the security chain is the end-user (and this is especially true in the Enterprise world). An attacker can easily find out or guess what antivirus a company is running and craft a piece of malware that will not be detected by it. Because such attacks are very narrow, the sample will not be disseminated around the world, making its discovery less likely.
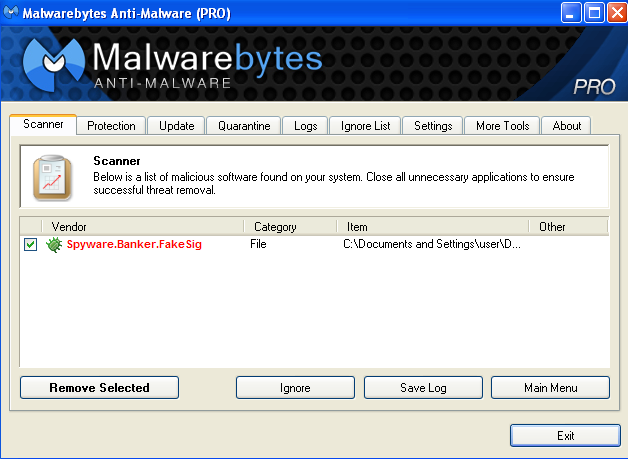
Our Consumer, Small Business and Enterprise customers all are protected from this threat which we detect as Spyware.Banker.FakeSig:
The same old tips still hold very true. Do not open an attachment, even from someone you know without first doing a thorough check on it.
Even if a file is digitally signed, it does not guarantee that it’s safe to use. A lot of potentially unwanted applications can use a digital certificate and, of course, malware can too (with a valid or revoked certificate).
Also, apply these basic and yet powerful rules:
– Check the file extension and beware of the double (or sometimes multiple) file extension trick: i.e. document.pdf.xls.exe (what matters is the last extension!).
– Never trust file icons. Just because it looks like a Word document or PDF file doesn’t mean it is, and most people don’t know that.
The Certificate Authority DigiCert and file host egnyte both have been contacted last Friday but we still have not heard back from them yet.
With that in mind, stay safe!