Exploit Kits are a serious cyber threat today, estimated to be responsible for the vast percentage of malware infections worldwide. Exploit kits distributed currently through both public and underground sources appeal to a wide range of audiences, from inexperienced hackers to seasoned “black hat” cybercriminals. Perhaps you or someone you know may have heard about some of the popular exploit kits in existence, like Blackhole, but didn’t really know what it was or an Exploit kit in general. This week on Unpacked we’re going to fill in some of the blanks for our readers and take a look at exploit kits from the past to the present.
Overview Exploit kits are a type of malicious toolkit used to exploit security holes found in software applications (Adobe Reader, etc) for the purpose of spreading malware. These kits come with pre-written exploit code and target users running insecure or outdated software applications on their computers. While the process of becoming exploited by one of these kits will vary, the procedure usually goes a bit like this:
- A victim visits a website whose server has been hacked by cybercriminals.
- The victim is redirected through various intermediary servers
- The victim lands at a rogue server hosting the exploit kit
- The exploit kit gathers information on the victim and determines the exploit to deliver
- Exploit is delivered
- If exploit succeeds, a malicious payload (custom malware program) is downloaded to the victim’s computer and executed.
The folks over at Hewlett Packard have also made a pretty good image depicting exploit kits in action.
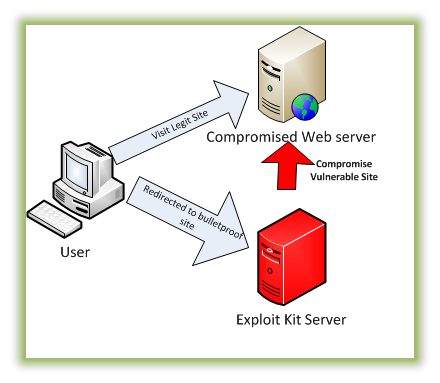
How exploit kits work (image courtesy of HP)
The last step involving the payload is classified as a drive-by download since it happens without the victim’s knowledge or consent. Drive-by attacks such as these have been used to deliver malware for many years, often in the form of an email message or popup windows—these attacks have a greater sense of predictability. Since the exploits made from these kits can be launched when visiting legitimate websites, users are less likely to see an attack coming.
Background and Origin Software exploitation is not a new concept and has been used for many years to spread malware. As this trend increased, it only made sense to start packaging these exploits and selling them to cybercriminals for profit (who in turn use the kit to exploit thousands and potentially make more profit).
Kaspersky Labs states that MPack was one of the first publicly recorded kits available, released in late 2006 by Russian programmers. Like the exploit kits of today, this kit was a collection of PHP scripts that targeted security holes in commonly used programs, like Apple Quicktime or Mozilla Firefox. The kit went viral and was spotted on more than 10,000 websites shortly after release, as reported by security researcher Brian Krebs.
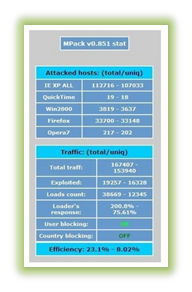
Mpack exploit kit – courtesy of Brian Krebs
Fast forwarding to the present, exploit kits have become increasingly more potent and continue to advance. Today’s modern exploit kit comes neatly packaged by the author and does not require any knowledge of how an exploit works. In addition, most exploit kits have a user-friendly web interface that allows licensed users to login and view active victims and statistics. In some instances these kits even include a support period purchased from the author and included updates, much like the average commercial software of today. Additions such as these make these kits very accessible to a wide range of users, even those with more limited computer proficiency.
Login page to view statistics.
The majority of exploit kits released today come from countries with a thriving underground cyber market, like China or Russia. According to a new study recently conducted by Solutionary’s Security Engineering Research Team (SERT), about 70 percent of exploit kits released in Q4 2012 come from Russia, with China and Brazil following a distant second and third. About another 20% have still not been attributed.
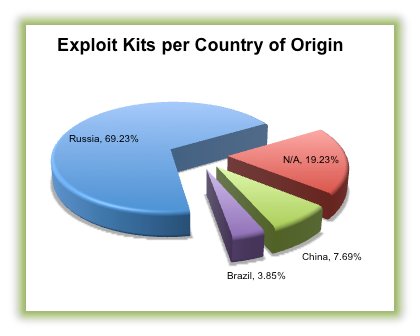
Courtesy of Solutionary’s SERT Q4 2012 report
Russia has a long cybercrime history with black hat programmers continuing to make extensive profits from writing these kits. Organizations like the Russian Business Network (RBN) based in St. Petersburg have fueled this growth by providing a cybercrime platform; for many years, the RBN has continued to offer website hosting to exploit writers, allowing hackers to collaborate and sell their exploit kits to buyers internationally. Today, the RBN does not exist as a single entity; it has since become harder to track, as they’ve since split into cells and changed names several times.
In the end it comes down to money. It is a very profitable trade for the exploit author to create a manage these kits, as licenses can be very costly to purchase—as much as $10,000 per month—and these price tags are matched by an increasing demand. Even a typical kit usually costs around $500 a month, and yet only includes a lot of the well-known exploits used for years. The most expensive kits will include exploits that are either very secret or sophisticated, sometimes targeting zero-day vulnerabilities (discovered at release). Malwarebytes forecasts that exploit kits will continue to be developed for many years to come, and criminals will continue to pay premium rates to use them for spreading malware.
Exploited software Oftentimes, exploit code authors target software with a history of numerous security flaws because it makes their job easier and achieves the same result, which is bypassing restrictions set in place by a program and achieving what’s known as “privilege escalation”. With escalated (increased) privileges, arbitrary programs can be downloaded and executed on the victim’s computer without prior consent.
Many of the kits all have overlapping exploits, some of which are still working years after discovery. In fact, it’s estimated that about 60 percent of vulnerabilities targeted in today’s exploit kits are over two years old. These exploits are still working because many users simply don’t bother with updating their software. In response to user negligence, a lot of software companies are pushing out automatic updates to their programs that occur while they’re running.
There isn’t a level playing field here—some software is exploited more than others. Oracle Java along with several Adobe products is frequently exploited, with new Common Vulnerabilities and Exposures (CVE) identifiers recorded daily for their products. Because it increases the chance of malware infection, software that’s targeted for exploitation is usually very popular and likely to be installed on the victim’s computer. For example, web browser programs like Mozilla Firefox and Opera are commonly targeted since they’re used by many to surf the internet. Other web browsers like Internet Explorer are targeted because they are part of the Operting system itself, guaranteed to be installed for Windows users.
To give our readers an idea of just how many vulnerabilities exist in some software products, Oracle addressed a whopping 50 security holes found in the Java software just this month. Due to the countless security holes, exploits for many of these programs like Java have become very popular and are most likely inside every exploit kit released. In addition, many vulnerabilities have also been discovered in Adobe products this year, no doubt with more to come.
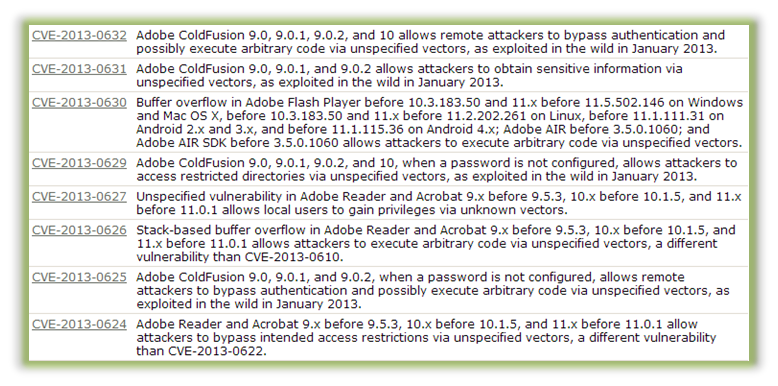
List of recent vulnerabilities found in Adobe products.
As a consumer using these products, you may be unaware of how many vulnerabilities there are on your computer; therefore, it’s important to pay very close attention to new threats discovered and decide whether it is worth the risk to use a certain program. While in some cases an alternative program can be found to reduce the chance of exploitation, the continuous risk may still be too great, and it may be better to stop using these commonly exploited programs altogether if possible.
Anatomy of an exploit kit Nearly every exploit kit has a web interface built on PHP, a popular server-side scripting language. A typical kit will have a directory for exploits, one for images, and perhaps another for configuration data. Another page is also included and acts as a statistics page, allowing the owner to view exploited computers and data about them, to include geographical location, Operating System and version, software installed, exploit delivered, and more. This data can be valuable to see which targets are most vulnerable and use that to spread more malware.
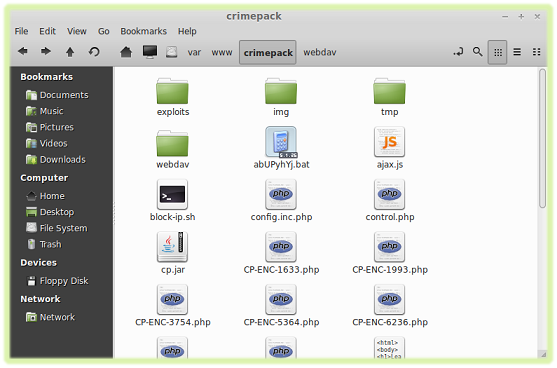
Contents of Crimepack exploit kit
One of the most crucial parts of the exploit kit is the landing page. A landing page is a specially crafted webpage and may have a generic name, like index.php. The landing page is initially requested and serves as the starting point for the exploit process. This page is designed to collect data on the victim and use this data to determine which exploit to deliver, and also interacts with other pages in the exploit kit to provide obfuscation and encoding routines, as well as various other services.
Another important component of an exploit kit is the control panel. From this page you can adjust exploits used and upload a custom malware to be executed thereafter. Some kits are configured to use only a handful of exploits, and others employ more of a “brute force” approach, launching a wide variety of exploits until one succeeds. The image below displays a control panel for the notorious Crimepack exploit kit.
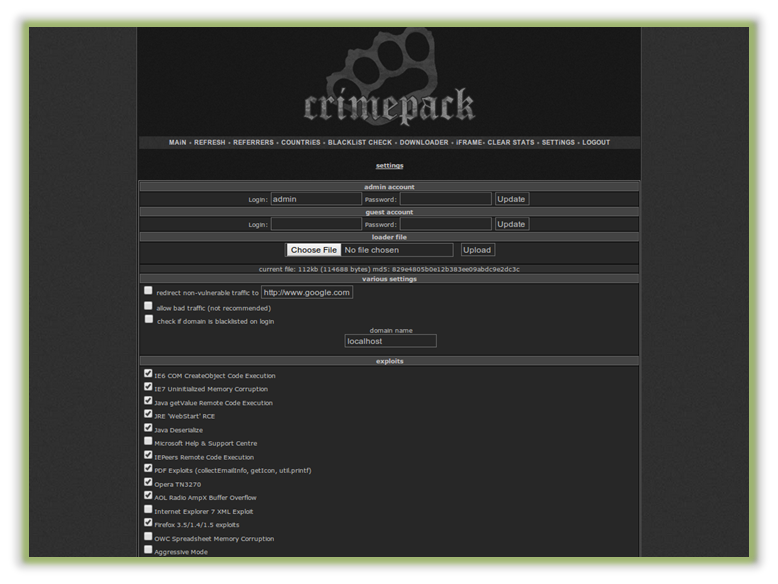
Exploits available in crimepack kit
Also, since exploit kit authors want to prevent their product from being freely distributed, the exploit kit itself is sometimes encoded to protect from being viewed or changed. A popular tool for this and for all PHP pages in general is the ionCube encoder. The images below compares a PHP page encoded with ionCube to a normal one; notice how one is readable and the other must be first translated by a loader program.
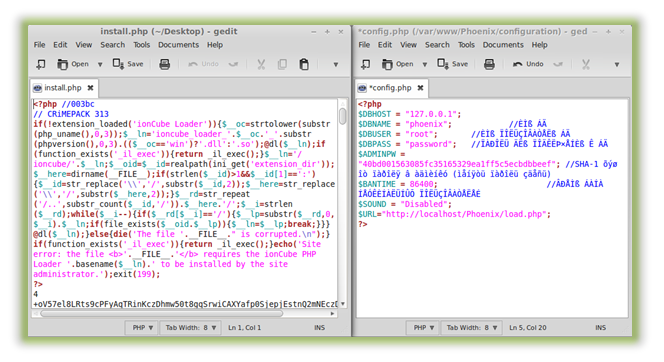
Left: PHP page encoded with ionCube encoder.
Right: Normal PHP page
Like a normal software application, an exploit kit is made up of several different parts. More advanced kits may also make use of software libraries to extend their functionality for other devious purposes. The exploit kits of the future are expected to advance and include additional protective features, like ionCube encoding, that inhibit analysis from reverse engineers.
Acquiring a kit Due to their illicit nature, acquiring exploit kits can sometimes be a difficult process. Most of these kits are only available in underground black hat forums where they’re licensed directly from the author. These forums aren’t usually indexed in popular search engines, such as Google, and therefore can be difficult to find without doing a little digging first.
However, even if you happen to stumble across one of these underground communities, it’s still not that easy. As with many organized crime groups, black hat hackers do not allow easy access into their private circles. Registration requirements for a lot of these forums are strict, usually requesting internal references as well as links to profiles proving you are in fact “one of them”. The below image shows a picture of a registration message from exploit.in (translated from Russian) and requests new applicants provide as many details as possible to speed up the process (NOTE: It is ill-advised to navigate to these type of sites unless doing so anonymously within a secure environment).
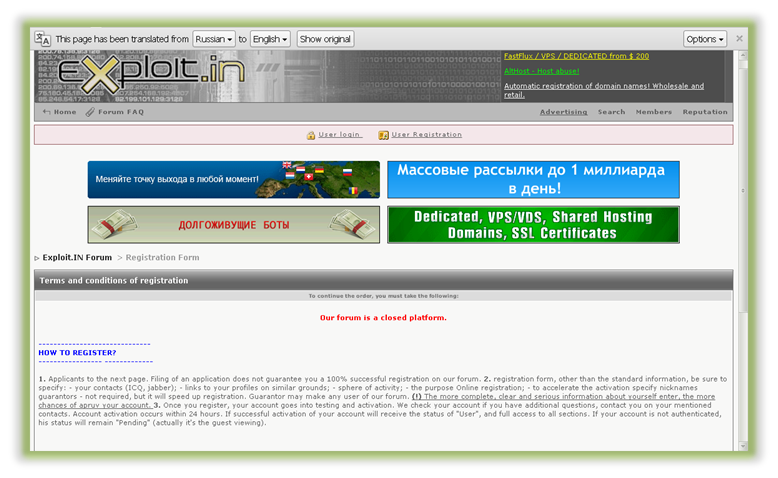
Registration requirements for exploit.in, a hacker community.
Exploit kits are not purchased from the author but usually “rented”. Like legally obtained commercial software, these exploit kits have licenses available for specified lengths of time that guarantee continuous revenue for the author. The below image depicts the Serenity exploit for sale by the author “Oakley”
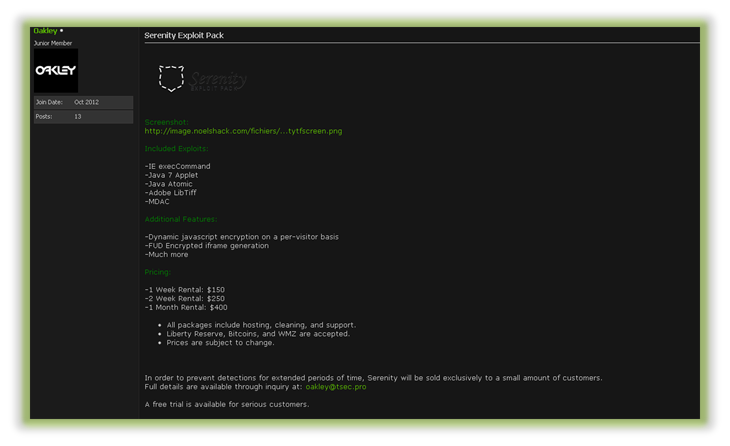
Serenity exploit kit for sale in hacker forum.
Some exploit kits have been leaked to the public and can be acquired with ease through open sources. However, these kits are typically a few years old and thus have older, less reliable exploits included. Downloading and using these kits within a test environment can give you additional insight into how the actual exploitation takes place, but please, do not use these kits to spread malware. Here at Malwarebytes, we DO NOT encourage our readers to test these kits on the internet, but only on private networks for the purpose of research and education.
Conclusion and Protection Exploit kits pose a serious threat to all computer users ranging from private users to corporate networks. Unlike the overused and annoying spam that makes its way to your email inbox, exploit kits can be more difficult to detect as they’re often triggered when visiting legitimate, yet hacked, websites. A perfect example of this was detailed on my last blog post featuring a mimic AV scanner called ‘Malwarebiter’, which blindsided visitors with a malicious Zeus Trojan upon arrival.
Regardless, most of the same general security rules apply. Using a secure browser and keeping your software updated will prevent a large majority of exploits created by these kits from succeeding. Let’s emphasize that last part: keep your software updated. Many of the older exploits in existence are still working simply because of unpatched software. Ensure you are using auto-update features for all of your computer programs and continue to check our blog as well as other security articles for the latest cyber threats.
In the unfortunate event that an exploit does succeed and malware is installed, it’s important to have reliable anti-malware protection stop the threat before it starts. There are various paid and free options available from a lot of AV companies, including our own Malwarebytes Anti-Malware. For additional information on other techniques for protecting yourself from exploit kits, take a look at a great article about Web Exploits by security researcher Jerome Segura.
Be vigilant.
References http://media.blackhat.com/bh-us-12/Briefings/Jones/BH_US_12_Jones_State_Web_Exploits_Slides.pdf http://www.zdnet.com/70-percent-of-exploit-kits-come-from-russia-says-report-7000010182/ http://blog.washingtonpost.com/securityfix/2007/06/the_mother_of_all_exploits_1.html http://blog.washingtonpost.com/securityfix/2007/10/mapping_the_russian_business_n.html http://www.securelist.com/en/analysis/204792160/Exploit_Kits_A_Different_View
_______________________________________________________________________________
Joshua Cannell is a Malware Intelligence Analyst at Malwarebytes where he performs research and in-depth analysis on current malware threats. He has over 5 years of experience working with US defense intelligence agencies where he analyzed malware and developed defense strategies through reverse engineering techniques. His articles on the Unpacked blog feature the latest news in malware as well as full-length technical analysis. Follow him on Twitter @joshcannell










