We are accustomed to seeing criminals take advantage of big events to push malware, so we always keep an eye out for malicious emails or websites. This one was no exception with customized spam messages and malicious links all leading to nasty infections.
The emails come with a subject line such as “Aftermath to explosion at Boston Marathon” or “Explosions at Boston Marathon” and a single link in the form of an IP address and a html document called news.html or boston.html.
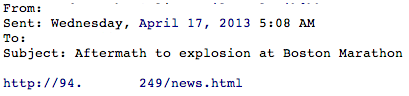
Spam #1: using news.html
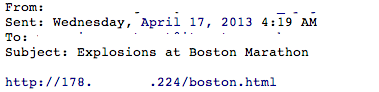
Spam #2: using boston.html
If you click on the link, it will open a page with multiple YouTube videos of the Boston bombings:
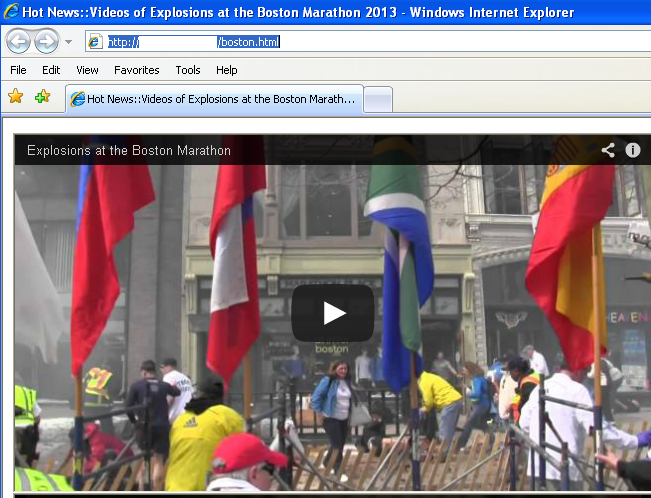
‘Bait page’ with real videos
While this appears legitimate, a malicious iframe silently loads a nasty payload:
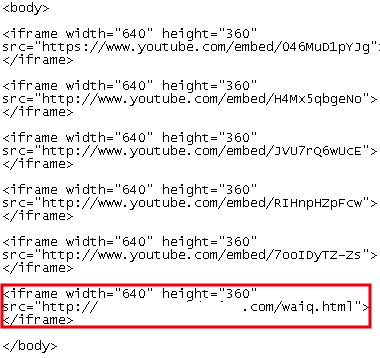
Last iframe is unlike the preceding ones…
Let’s take a look at the infection scenario with this Fiddler capture:
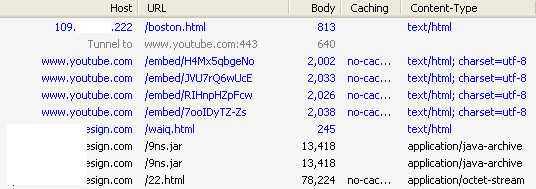
- infected link with Boston bombings videos
- several YouTube videos
- malicious iframe (waiq.html)
- Java exploit 9ns.jar
- malicious payload (22.html)
This drive-by download uses an Exploit Kit known as Redkit, and the particularity in this case is that it combines two malware payloads (read Redkit does the splits for more info on this). Two files are extracted from this exploit: alifna.exe and coppe.exe (both of them are already detected by Malwarebytes Anti-Malware).
A couple of minutes after watching the YouTube videos, a newly installed program called System Care Antivirus will take over your PC:
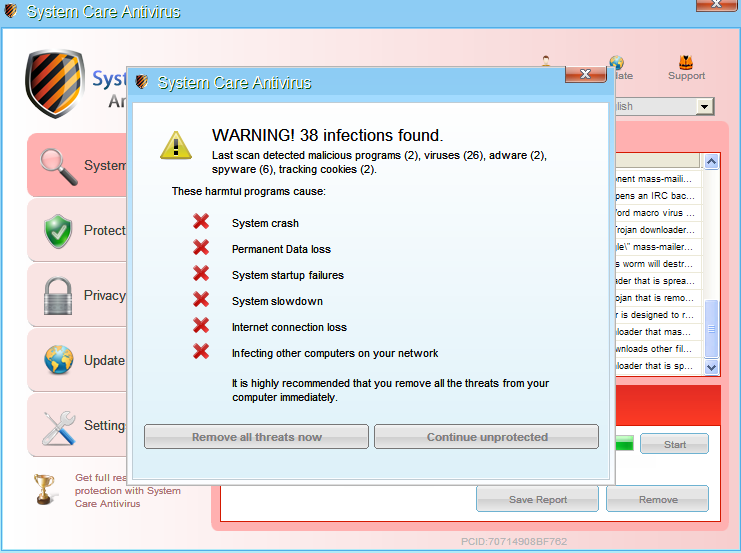
System Care Antivirus: don’t let its name fool you, it’s a scam!
This type of program is known as Fake AV and its purpose is to scare the user with messages like “Warning! Infections found”, “system crash” and get them to register and pay for the bogus software. The scare tactics go even further by disabling core applications and obstructing regular web browsing:
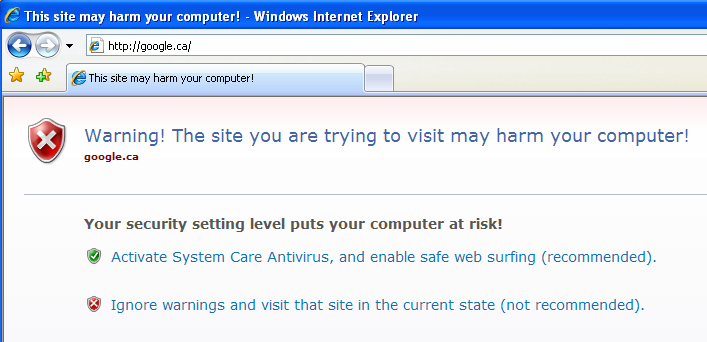
Since when is Google a malicious site?
For instructions on how to get rid of this and similar rogue antivirus programs, feel free to check out this guide.
As mentioned, we collected a lot of unique IP addresses all leading to this exploit:
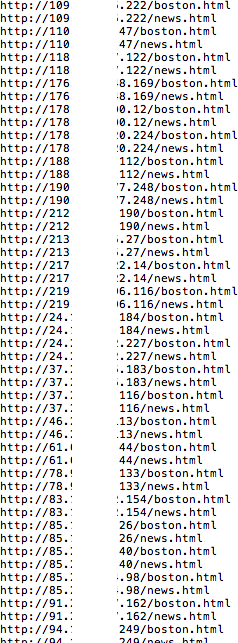
While some are hosted in places that would raise a red flag (the Ukraine, Bulgaria, China), there are also some in the US. As far as the Exploit Kit landing page itself, the one used in this particular blog post was hosted on a legitimate website running WordPress.
Another tragedy happened in Texas and the bad guys shifted their attention to it. The same email campaigns are now themed “Texas plant explosion”:
We cannot stress how important it is to be extremely cautious with links within an email. When such a tragic event occurs it’s easy to forget the basic security principles and fall for this dirty trick. The bad guys will use anything they can to spread their malicious creations to make money.









