It is very likely that you or someone you know has had one or multiple of their online accounts hacked into. It happens to everybody: individuals, small and big companies alike, can have disastrous consequences and makes you feel extremely vulnerable. In this post we will talk about some tips to give cyber-criminals a hard(er) time in their inevitable quest for easy money or their five minutes of glory.
While no security solution will ever be perfect and cyber-crime will always exist, each individual plays an important part in “facilitating” or not the act of cyber-theft. We will take a look at the most common and efficient ways to safeguard your information and identity. If you want to share some of your own tips, please feel free to leave a comment.
Keep a malware-free system
One of the easiest ways to get your credentials stolen is by typing them from an infected machine. There are countless banking trojans and other key-loggers whose main goal is to capture logins and passwords and send them back to cyber-criminals.
The best defense against malware is a defense that consists of multiple layers rather than one that relies on a single solution. Keep in mind that having the same type of product multiple times (for example having several antivirus products) may result in your computer freezing or behaving poorly. Rather, you want to make sure each product covers a different area (i.e. virus/firewall/browser protection). By the way, our Malwarebytes’ Anti-Malware can be installed along side typical antivirus products and provide an additional layer of coverage.
An extreme solution to having a malware-free system is to use a Live CD where nothing is stored permanently and can be booted off the same every time. It is obviously a very inconvenient solution but some people do use it when banking online.
Use a secure Internet connection
It goes without saying that logging into your account should be done through a secure connection. While most (if not all) providers support HTTPS which encrypts your connection, hackers love to setup rogue WiFi access points where all your computer’s traffic will be sent through them. It is trivial to redirect you to a fake login page that looks like it is encrypted but really isn’t. You type in your password and it is sent in the clear right to them.
To increase the security of your connection when you’re on the go or even at home, you can use inexpensive VPN services that essentially encrypt your data and also guarantee your anonymity.
If, like most people, you have your own WiFi at home please take a few minutes to ensure it is not wide open to intruders. If your are using an old router, it is quite possible the technology it came with is now completely outdated. For example, the WEP encryption still in effect on many models is so weak that any script kiddie can break into your network with ease. Your WiFi network must be locked with a strong password and have a good encryption standard such as WPA/WPA2. To access those settings, look on the actual router for the default link and password (there’s usually a sticker with this information).
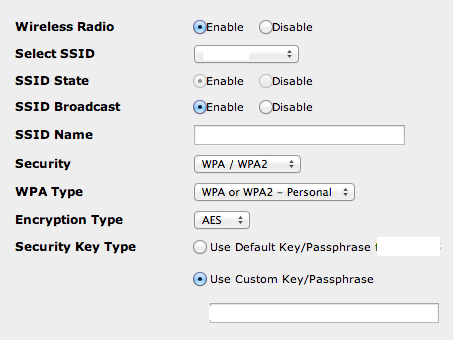
Authenticate by following best practices
Password
The traditional password remains the most used method to prove our identity. It is simple and quick for most of our needs. However there are many factors that make the password a security problem:
- we choose weak passwords
- we reuse the same passwords
- we never change our passwords
- we store or share our passwords in clear text
Following the hack on the Associated Press’s Twitter account, the Syrian Electronic Army hacktivist group published a tweet with what they say was the AP’s password:
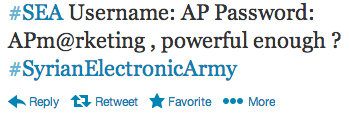
It that happens to be true, well, it’s a very weak password. If you are looking for tips on how to make and manage great passwords, I recommend you read this article from fellow Malwarebytes blogger Joshua Cannell.
Two-factor authentication – a feature not currently available for Twitter – provides an extra layer of security by requiring an extra piece of information to validate your identity. Typically, it consists of an SMS message containing a temporary access code. Since it still requires the user to type in a code or PIN within their browser, it is susceptible to man-in-the-middle attacks. Put it simply, active malware will be able to intercept both the password and the code either through keyboard input or directly from the browser.
Another method called Out of Band Authentication requires two different channels to login the user. For example that SMS code must be sent back using the phone (second channel) rather than the computer. At the end of the day, it is still irrelevant to keyloggers and phishing pages which are simply waiting for the user to enter their information. We already addressed the malware issue earlier, let’s now look at phishing threats.
Recognize a phishing attempt
Criminals love to social engineer their victims because as humans we tend to believe what we hear or see and we most often follow what we are told. The other advantage is that social engineering goes above all traditional security measures which usually require more work to break through.
Phishing is one type of social engineering where the victim is tricked into giving out personal information on a fraudulent webpage. It doesn’t matter how strong our password is if we are going to spell it out to the bad guys. Phishing scams can be targeted to a particular individual or company, in which case they are called spear phishing scams, or simply spammed out to millions of people with the hope that a small percentage of them will be tricked.
There are usually two components to a phishing attack:
- an email that acts as the social engineering piece
- a webpage that collects the information and sends it out to the bad guys
Both are usually very well crafted and look like the real thing. Various techniques are used to confuse people (legitimate looking links, replicas of the actual websites, etc.)
Tips like looking at the address bar are a good starter but not enough, especially when more and more people use mobile phones where the address bar is too small to fit an entire URL. One technique that works well is to think for one second before entering any type of data online and ask yourself: “Did someone or something asked me to log into my bank/email/Twitter/Facebook?” If the answer is yes, you really need to think twice before going ahead.
Set up a strong primary email account
Email is one of those things we have been using for so long that we almost take it for granted. It is also often a central point where many of our other online accounts report to. For this reason it can be a real pain or nightmare if we lose access to our email or if it gets compromised.
Many people don’t trust that their personal information will be kept secure and therefore often use fake data to register an account. While in itself it is not a bad idea for your own privacy’s sake, it can lead you into some troubles if one day you need to recover your account and one of the questions is for instance, your birthday… something that way back then you filled in completely randomly.
Additional information (phone, second email)
Don’t forget to update your alternate email when it changes! Because it is one of these settings that gets buried deep, we often forget to check it is still current. A classic scenario is when you’re locked out of your account and it wants to send a recovery link to your other email address at the company you no longer work for, oops…
The (in)famous security questions
This is perhaps one of those security measures that can make you less protected than you were to begin with. While a lot of emphasis is put on the password and how it must be long, contain numbers, special characters, etc… nobody really seems to care that the same logic is not applied to your security questions and answers:
In other words these security questions are just too basic and a little bit of googling about you might just reveal all these answers.
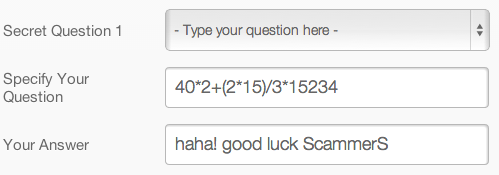
Instead I suggest that you create your own question which can actually demand multiple answers (and why not use special characters in there too?). Or you can just try to be a little more creative.
Important emails, documents
We often use our emails to store financial documents, other important data and, heaven forbid, passwords! And with pretty much unlimited storage we don’t really think about ever deleting anything. It is much safer to encrypt these documents and store them somewhere safe out of your inbox, or if they are no longer needed, to delete them.
Remember that the service provider can fail you too
Despite all the added precautions you may have taken, your account could still get hacked. Yahoo! has been in the spotlight for having several security flaws in its webmail client that lead to thousands of accounts getting compromised. Some reports say that the user had to click on a link in order to get hacked, through a cross-site scripting (XSS) attack, while others suggest that accounts were hacked with no user interaction required. I had an old account which I had no logged into for several years and that started sending out spam about a month ago.
When I logged in, I saw several messages in my Sent folder, all with the same format: a single link in the message’s body.
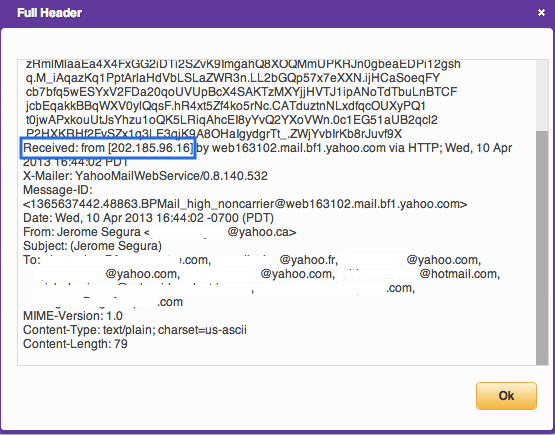
Looking at the email headers I could confirm I never sent those messages because they came out from an IP address located in Malaysia:
The hackers sent out spam to all my contacts and that is in fact how I found out about this. One thing I learned is “if you don’t use it, get rid of it”, in other words a dormant email account can still represent a threat if it has your contact information as well as some of your personal data.
Something you can do (so that at least your friends are not the first to tell you your account has been hacked) is to add yourself to your own contact list. The spammer might just blindly email everybody on there and receiving emails from yourself should tip you off.
Another feature you can check every now and again is your account activity in Gmail, Yahoo! Mail. All logins shown in there should be from your own computer and IP address. Anything else would be suspicious.
Do damage control
If your account has been hacked, you need to act promptly before more damage is done. One of the things to do is lock out the bad guys before they get a chance to do the same to you. Change your password and security questions immediately from a clean computer or device you trust (an active malware infection could just capture the new password again and again). Find out if your contacts have received email from you that appeared suspicious and let them know you were hacked. If they did click on links or open attachments from you recently, there is a chance they got hacked too.
Don’t stop here as most likely the bad guys didn’t either. Check all your other accounts and update them accordingly. If you are using online banking or do other transactions you will want to keep a watchful eye on those as well.
Share your experience. There is no need to be ashamed and keep that to yourself. Do the right thing by admitting to the facts if you did indeed make some mistakes and draw your own conclusions. The more people know about these things the better we all are. While security practices and technologies aren’t perfect there is no excuse for shooting yourself in the foot by not applying them.









