The Ransomware family ‘Reveton’ has been a thorn in the sides of many for over two years. It has employed a dynamic approach by tailoring the malware to specific countries and frequently changing infection methods.
Nevertheless, one thing that remains constant in Reveton is its ability to instill fear in users by accusing them of various illegal activities, and demanding payment for absolution. To this end, Reveton has once again reinvented itself, this time with a contingency plan just in case the user doesn’t pay up.

Now, while Reveton has been on a roller coaster as far as how much they demand from users, they seem to try and maximize on their potential target, rather than how much they think their target will pay.
Sometimes you would see Ransomware that asks for thousands of dollars from small businesses, and other times you will see only $100, a low number that some people might consider paying.
This new version of Reveton takes it a step further and regardless of how much users are willing to pay, or not pay, the bad guys are still getting a profit.
We have talked before about malware that employs the use of Bitcoin mining software, installed without the users knowledge. Bitcoin harvesting is completely fine when users want to make some extra virtual cash by letting the BitCoin service use their personal system to crunch numbers.
The situation changes when something like Ransomware locks out your system and then runs the Bitcoin Miner, making cash for the attacker, regardless if the user pays to unlock their system.

The Reveton sample that I got my hands on tried some pretty sneaky methods of obfuscation and separation of powers, almost like it was written by different people, and it probably was. In the end though, this is what the malware does upon execution:
- Duplicates itself and creates multiple files in the %temp% directory
- Modifies registry keys
- Creates an entry in the Start-up folder (for persistence purposes) for RunDll32.exe, the copied malware in the %temp% folder and the parameter, ‘GL300’
- Restarts the Computer
- Executes the Start-Up entry after booting, downloads the Ransomware screen
- Executes rundll32.exe again with another copied binary (random file name) and the parameter ‘GL301’
- Locks the system with the Ransomware functionality
- Downloads and executes the bitcoin miner on the system: coinme.exe -o stratum+tcp:xxxx.eu:9000 -u username -p xxxx
After the installation, the malware will beacon back to its command and control (C2) server to give updates on BitCoin operations. The following chart was obtained from the statistics gathering functionality of one particular C2:
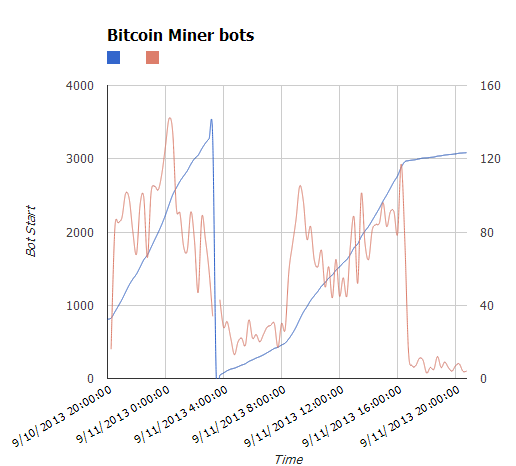
The chart shows the check in trends of the miner bots or when the system is reset, it resets every 24 hours and increases throughout the day. You can see a huge increase in the late evening and a slow rise into the early evening. The red shows check-in activity while the blue shows the actual running numbers.
The best way to avoid coming into contact with Reveton Ransomware, or any Ransomware for that matter, is to keep the definitions for your Anti-Malware/antivirus product up to date so they can effectively defeat the binary before it ever gets a chance to execute.
Ransomware is most commonly spread via drive-by downloads and Reveton especially has been seen working with some of the most notorious exploit kits available today. Disabling Java Script and keeping all of your plugins and browser as up to date as possible will help deter any attempts for Ransomware to steal your system and maybe even your money.
To end this post, I want to show different screenshots obtained from the same Ransomware version but different locations, never before seen in use by any other Ransomware, I also want to attribute the finding of this variant to @Horgh_rce and leave you a list with good sources for more information about Ransomware and BitCoin Miners. Thanks for reading and safe surfing!
- Hijackers Pose as NSA
- FBI Ransomware Now Targeting Apple’s Mac OS X Users
- BotCoin: Bitcoin Mining by Botnet




UPDATE:
Here is a list of hashes for this Ransomware in case anyone wants to take a look:
b6741ae18c3907624abf314e5f052e4 309c1a5c7ac96a4bb36099f6b0413146 3c7ff37a431d2824bed10f3344c77bf4 62576e297ef2afa665c3077e4a09b0a1 99ad4397562ef4c1372302710ca0f257 64973220d202a2c053c219f2d60ef1f0 92a4f4694dcc4af86026685d19bd35e3 2aa316142102a541fb3ebacb43fa3c98 f5ff762cdc7e55d9755f7eb3141045f5 13623dce474790f0b32c01278786ab5e 70896e207968ae6f750ce2ca1039d5fe 58dd481e99284d40aa460117b0c55727 86458a604fb0265e0d35702a0223259d f27c0ec06030b278173ea1197a560225Enjoy!
—————————————————————————————————————————–
Adam Kujawa is a computer scientist with over eight years’ experience in reverse engineering and malware analysis. He has worked at a number of United States federal and defense agencies, helping these organizations reverse engineer malware and develop defense and mitigation techniques. Adam has also previously taught malware analysis and reverse engineering to personnel in both the government and private sectors. He is currently the Malware Intelligence Lead for the Malwarebytes Corporation. Follow him on Twitter @Kujman5000










