Update 06/02/2014: Today the US Department of Justice (DOJ) announced an effort to disrupt the Gameover Zeus Botnet. In addition to this effort, the DOJ announced an another joint-effort that involved seizing computer servers used by the Cryptolocker ransomware.
“We succeeded in disabling Gameover Zeus and Cryptolocker only because we blended innovative legal and technical tactics with traditional law enforcement tools…”, said Deputy Attorney General James Cole in today’s announcement.
Evgeniy Bogachev was identified as a leader of cyber criminals based in Russia and Ukraine responsible for the development and operation of both the Gameover Zeus and Cryptolocker schemes. He is currently wanted by the FBI.
While the C2 infrastructure is currently under the control of Law Enforcement, this is likely to only be a temporary disability of the malware until new servers are online.
It’s worth stating that users still need to protect themselves from Cryptolocker despite its recent interference. Continue to maintain a strong security posture, to include updating Antivirus/Anti-malware definitions, and avoiding unknown or unforeseen email attachments, even if you know the sender.
For more information, read the full announcement from the DOJ here.
Update 12/20/2013: A new version of Cryptolocker—dubbed Cryptolocker 2.0—has been discovered by ESET, although researchers believe it to be a copycat of the original Cryptolocker after noting large differences in the program’s code and operation. You can read the full blog comparing the two here.
Original story:
Just last month, antivirus companies discovered a new ransomware known as Cryptolocker.
This ransomware is particularly nasty because infected users are in danger of losing their personal files forever.
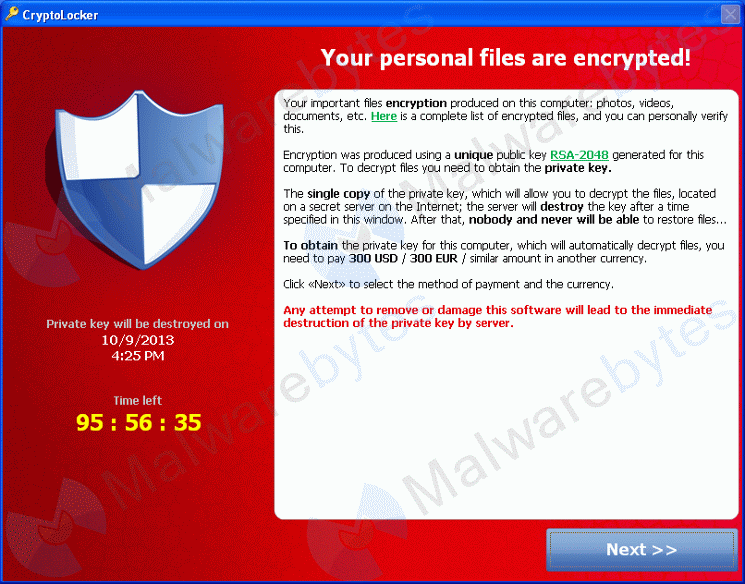
Spread through email attachments, this ransomware has been seen targeting companies through phishing attacks.
Cryptolocker will encrypt users’ files using asymmetric encryption, which requires both a public and private key.
The public key is used to encrypt and verify data, while private key is used for decryption, each the inverse of the other.
Below is an image from Microsoft depicting the process of asymmetric encryption.
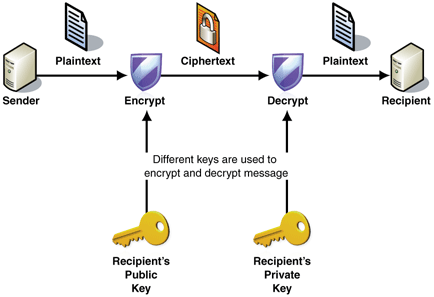
The bad news is decryption is impossible unless a user has the private key stored on the cybercriminals’ server.
Currently, infected users are instructed to pay $300 USD to receive this private key.
Infected users also have a time limit to send the payment. If this time elapses, the private key is destroyed, and your files may be lost forever.
Files targeted are those commonly found on most PCs today; a list of file extensions for targeted files include: 3fr, accdb, ai, arw, bay, cdr, cer, cr2, crt, crw, dbf, dcr, der, dng, doc, docm, docx, dwg, dxf, dxg, eps, erf, indd, jpe, jpg, kdc, mdb, mdf, mef, mrw, nef, nrw, odb, odm, odp, ods, odt, orf, p12, p7b, p7c, pdd, pef, pem, pfx, ppt, pptm, pptx, psd, pst, ptx, r3d, raf, raw, rtf, rw2, rwl, srf, srw, wb2, wpd, wps, xlk, xls, xlsb, xlsm, xlsx
In some cases, it may be possible to recover previous versions of the encrypted files using System Restore or other recovery software used to obtain “shadow copies” of files. The folks at BleepingComputer have some additional insight on this found here.
Removal:
Malwarebytes Anti-Malware detects Cryptolocker infections using multiple names, to include Trojan.Ransom and Trojan.CriLock.XL, but it cannot recover your encrypted files due to the nature of asymmetric encryption, which requires a private key to decrypt files encrypted with the public key.
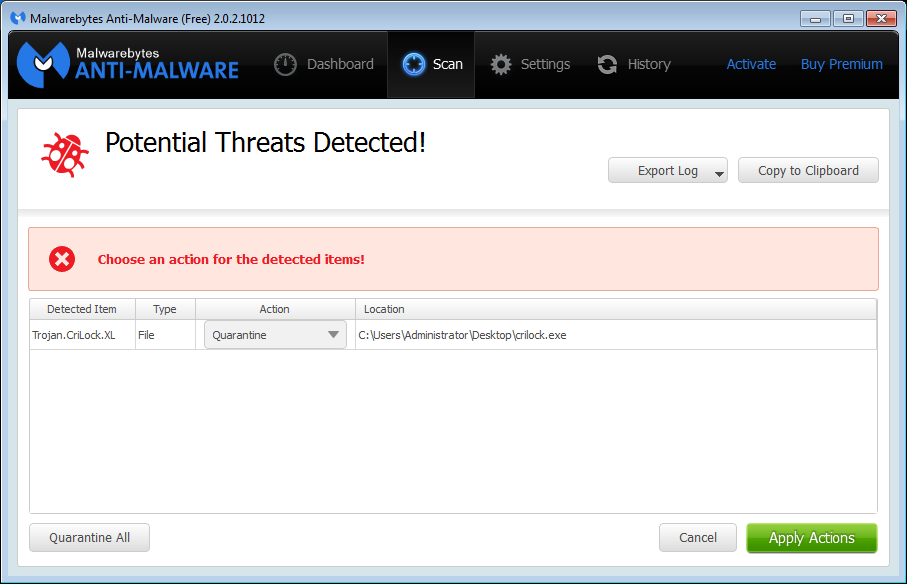
In order to make removal even easier, a video was also created to guide users through the process (courtesy of Pieter Arntz).
While Malwarebytes cannot recover your encrypted files post-infection, we do have options to prevent infections before they start.
Users of Malwarebytes Anti-Malware Premium are protected by malware execution prevention and blocking of malware sites and servers.
To learn more on how Malwarebytes stops malware at its source, check out this blog.
Free users will still be able to detect the malware if present on a PC, but will need to upgrade to Pro in order to access these additional protection options.
Backup:
Also, the existence of malware such as Cryptolocker reinforces the need to back up your personal files.
However, a local backup may not be enough in some instances, as Cryptolocker may even go after backups located on a network drive connected to an infected PC.
Cloud-based backup solutions are advisable for business professionals and consumers alike. Malwarebytes offers Malwarebytes Secure Backup, which offers an added layer of protection by scanning every file before it is stored within the cloud in an encrypted format (don’t worry, you can decrypt these).
To find out more on remove Cryptolocker, check out the official removal guide from Malwarebytes.
Update: Adam Kujawa from Malwarebytes gives further insight about Cryptolocker in an interview with Category 5
_________________________________________________________________
Joshua Cannell is a Malware Intelligence Analyst at Malwarebytes where he performs research and in-depth analysis on current malware threats. He has over 5 years of experience working with US defense intelligence agencies where he analyzed malware and developed defense strategies through reverse engineering techniques. His articles on the Unpacked blog feature the latest news in malware as well as full-length technical analysis. Follow him on Twitter @joshcannell










