The Domain Name System (DNS) is the equivalent of the phone book for the Internet in that in translates host names (i.e. malwarebytes.org) into IP addresses (i.e. 184.173.97.192) therefore allowing systems to communicate with each other.
Without a DNS, we would have to manually type IP addresses each time we need to visit a website.
Most Internet Service Providers as well as other companies such as Google offer this functionality. On top of domain name translation, DNS services can also filter out malicious or phishing sites, provide additional security and speed improvements.
OpenDNS, a very popular DNS resolution service with over 50 million active users, experienced a malvertising (malicious ads) attack that affected a certain percentage of its user base.
The problem was first spotted by French security researcher Malekal:
Malekal was kind enough to share the traffic capture with me so we can better understand how this happened.
When a site cannot be resolved, OpenDNS provides an ad-supported page where the user can look for similar sites, etc.:
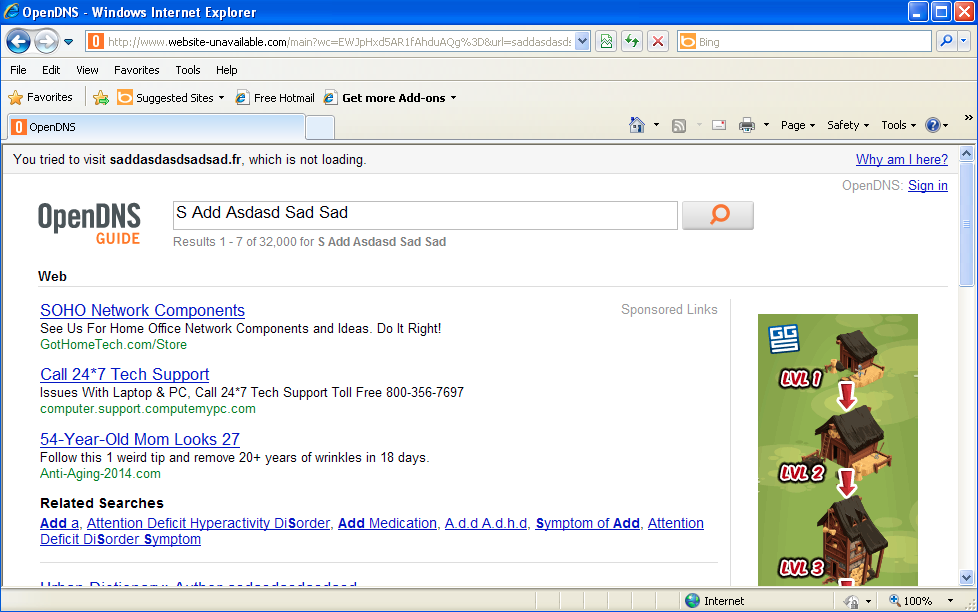
(On a side note, the second ad from the top for the Tech Support service links to computemyPC, a company involved in tech support scams.)
The malvertising attack can be summarized in the graph below:
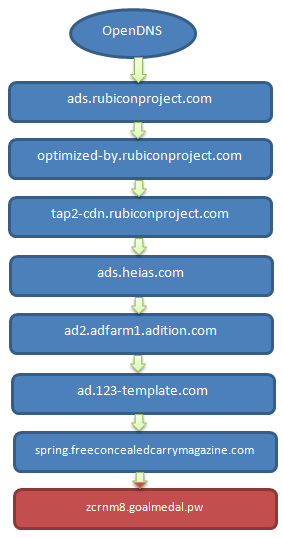
Let’s take a deeper look at each URL involved in this infection.
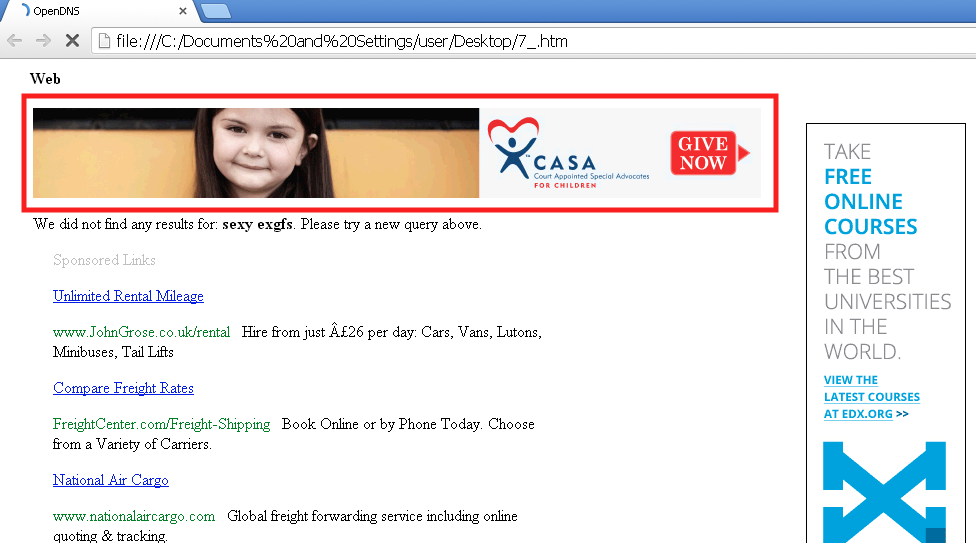
#1 http://www.website-unavailable[dot]com/main?wc=EWJvGQlmBRNEGxVwAxYBFBc%3D&url=sexy.exgfs.com%2Fpics%2Famateur-exgirlfriends%2F%3Fdiscount%3D2045028&ref=http%3A%2F%2Fsecrethomesex.com%2F&w=971&h=514&ifc=0
The code responsible for the ad circled in red shown below:
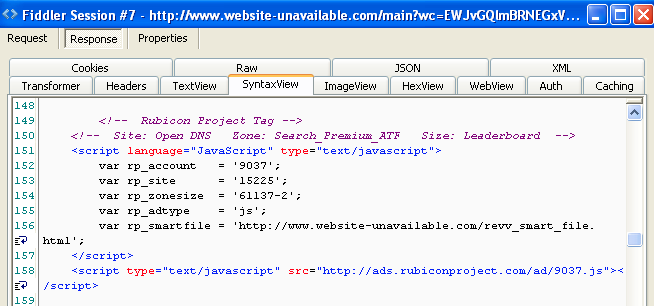
#2 http://ads[dot]rubiconproject[dot]com/ad/9037.js loads
#3 http://optimized-by[dot]rubiconproject[dot]com/a/9037/15225/61137-2.js?&cb=0.9430403284420199&tk_st=1&tk_sf=1&rp_s=c&p_exp=1&p_pos=atf&p_screen_res=1024×768
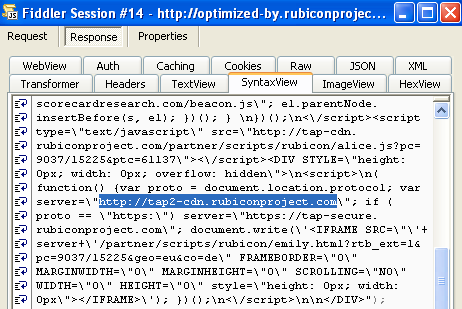
#4 http://tap2-cdn[dot]rubiconproject[dot]com/partner/scripts/rubicon/emily.html?rtb_ext=1&pc=9037/15225&geo=eu&co=de
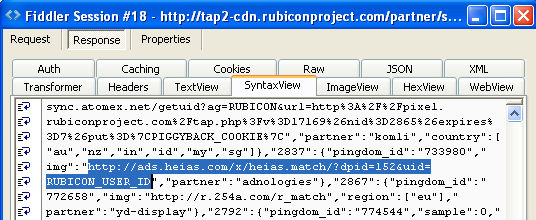
#5 http://ads[dot]heias[dot]com/x/heias.TAG.v2.0/tag.php?H_VAR=h_ref|;|http%3A%2F%2Fwww.opendns.com{redacted}
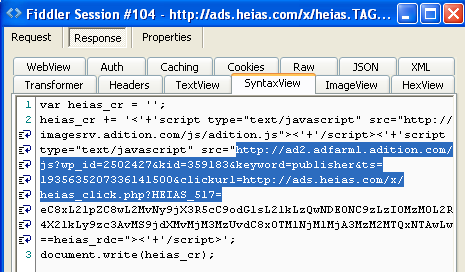
#6 http://ad2[dot]adfarm1[dot]adition[dot]com/banner?sid=2502427&adjsver=3&co=1&fvers=10&iframe=0&ref=http%3A//www.website-unavailable.com{redacted}
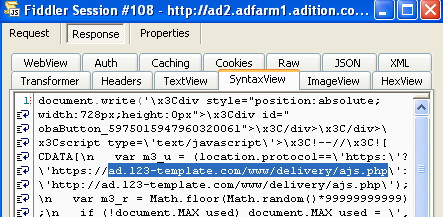
#7 http://ad[dot]123-template[dot]com/www/delivery/ajs.php?zoneid=4&cb=40468151097&charset=utf-8&loc=http%3A//www.website-unavailable.com/{redacted}
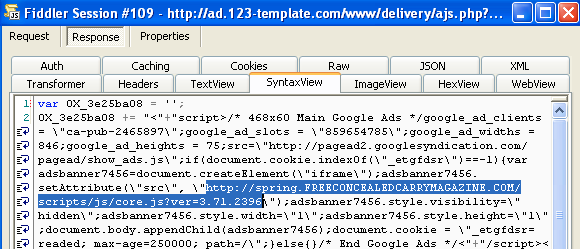
#8 http://spring[dot]freeconcealedcarrymagazine[dot]com/scripts/js/core.js?ver=3.71.2396
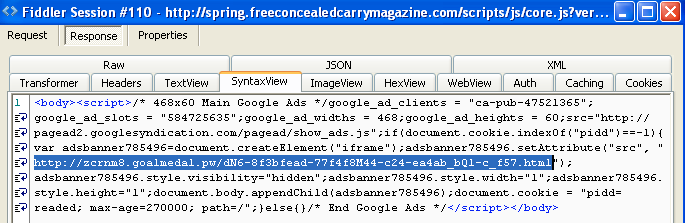
#9 Exploit Kit
Exploit landing: http://zcrnm8[dot]goalmedal[dot]pw/dN6-8f3bfead-77f4f8M44-c24-ea4ab_bQ1-c_f57.html
Java exploit http://zcrnm8[dot]goalmedal[dot]pw/4030722763/1391145360.jar
Binary 1 (VT results): http://zcrnm8[dot]goalmedal[dot]pw/f/1391145360/4030722763/2
Binary 2 (VT results): http://zcrnm8[dot]goalmedal[dot]pw/f/1391145360/4030722763/2/2
Malvertising is not always straightforward and often involves multiple intermediaries, which is why it is so hard to spot and prevent.
The more ad networks are involved, the greater the chances of a malicious ad are. It’s easy to see how the initial client (in this case OpenDNS) may be completely unaware of dubious or malicious networks that are down the stream.
In fact the first ad is powered by the Rubicon project which is known for its attention and care against malvertising. The problem is the number of successive ad networks where it only takes one to turn things sour:
- ads.heias.com
- ad2.adfarm1.adition.com
- ad.123-template.com
This attack appears to have affected only certain countries, with Germany being one of them.
Shortly after Malekal reported the malvertising issue to OpenDNS, the problem seemed to have been taken care of.
Prompt reactions are crucial and we know for a fact how hard it can be sometimes to get ad networks or even compromised sites to roll out an immediate fix.
A radical solution to malvertising would be to remove all ads from the websites we visit. However, this is not a realistic solution because it is the main source of revenues for website owners.
This is why if you use an ad-blocker utility, you may found yourself blocked by many webmasters who will refuse such visitors.
While there are some good and bad practices when it comes to ad management, the malvertising problem is here to stay.
Special thanks to Malekal for his help on this. Feel free to check out his site for more coverage on malvertising and other threats.
Jérôme Segura @jeromesegura










