A few weeks ago, we wrote about an Android master key flaw discovered by Bluebox Labs that allowed modification of APK code, thereby affecting some 99 percent of all Android devices.
Many security researchers released proof-of-concept code that provided missing technical details from the report.
Google was quick to fix the vulnerability, but Android’s fragmented update model across several OEMs is leaving most users unprotected.
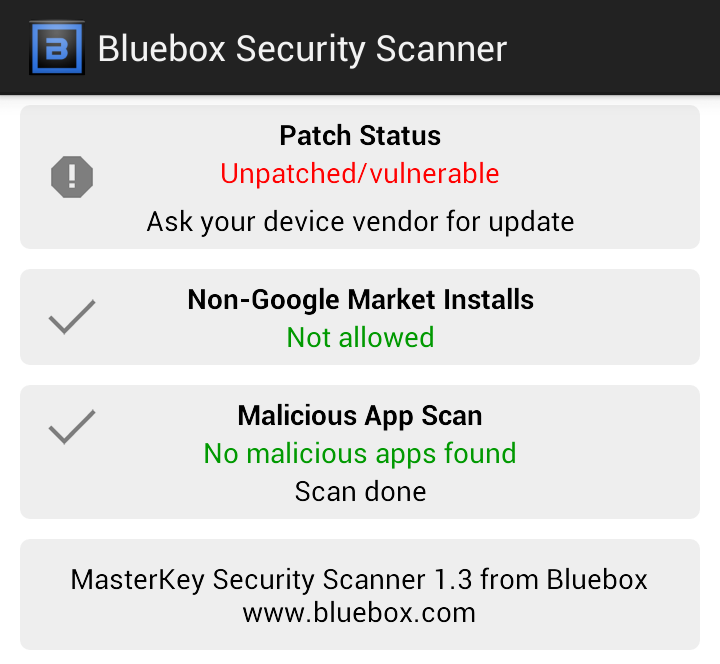
Bluebox released its own app on the Google Play store which tests to see if your device is vulnerable, and if any apps have been tampered with.
But the app from Bluebox still won’t adequately protect unpatched users.
While the app can detect the presence of the flaw (known as Android bug #8219321), it doesn’t patch the vulnerability or disinfect any malicious apps if found.
What’s more, only the most recent devices with the latest version of Android (like the Samsung Galaxy S4) seem to be unaffected by the vulnerability.
I tested my Samsung Galaxy S3 running the latest released by my carrier (4.1.1), and I was still vulnerable, making the 99 percent figure seem all too real.
So what can you do to protect yourself while you’re waiting for an update? Unfortunately, not much outside of modifying your phone.
One app called Rekey may be one possible solution. Released yesterday to the Google Play store, Rekey claims to patch the master key vulnerability specified by Bluebox, but not without a rooted phone first. If you recall, rooting your phone is the process of raising user privileges to allow greater control of the device.
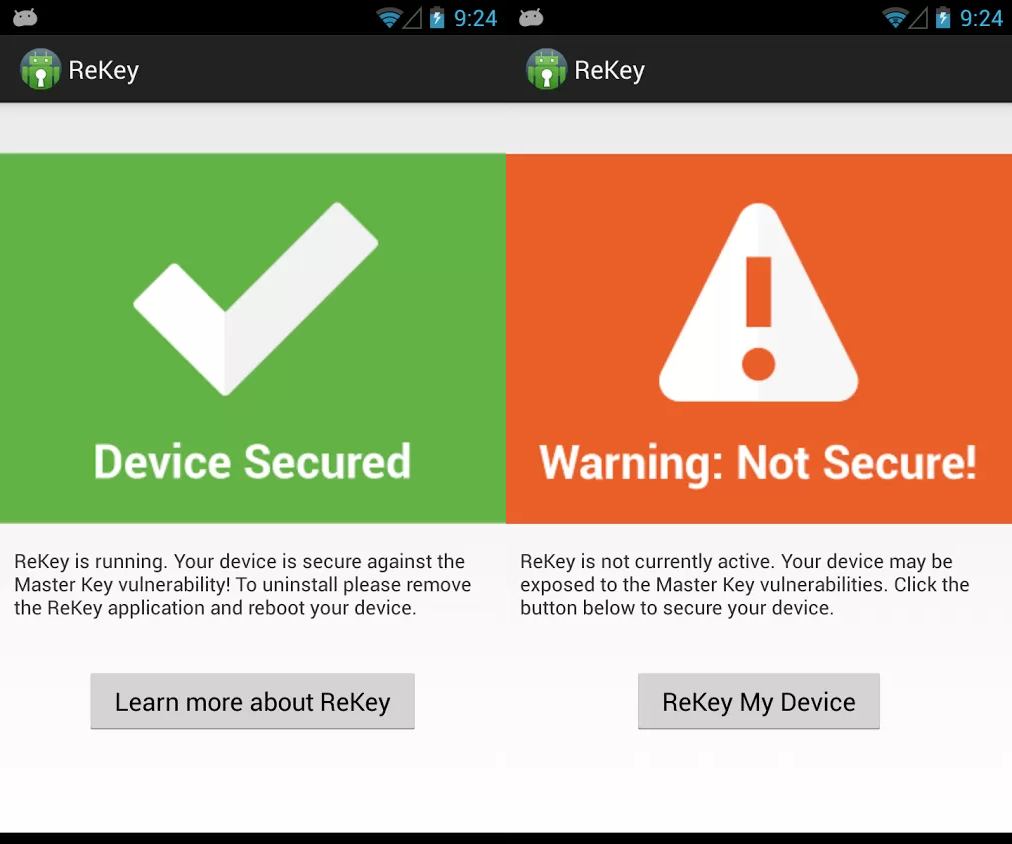
The Rekey project is headed by the Systems Security Lab at Northeastern University and Duo Security. According to the app developers, the app works by injecting “a small piece of code into the running Android framework. The code dynamically patches the ZipEntry and ZipFile classes to interpose on the vulnerable routines and thereby fix the root cause of the bugs.”
The app seems legitimate, but rooting your phone may very well put you at an even greater risk than the master key vulnerability itself. This is because root-level access can potentially give a malicious app more access to your phone than a traditional user-level approach.
Although an official patch may not be available to many users, following some common sense rules (like verifying downloaded apps from the Google Play store) should keep you protected from most threats on Android.
Nevertheless, the inability to receive timely updates on Android devices when major vulnerabilities are discovered is unacceptable from a security standpoint. If the OEMs and mobile carriers don’t do a better job at protecting consumers, it may be time I drank the Apple Kool-Aid.
_______________________________________________________________________________
Joshua Cannell is a Malware Intelligence Analyst at Malwarebytes where he performs research and in-depth analysis on current malware threats. He has over 5 years of experience working with US defense intelligence agencies where he analyzed malware and developed defense strategies through reverse engineering techniques. His articles on the Unpacked blog feature the latest news in malware as well as full-length technical analysis. Follow him on Twitter @joshcannell









