Botnet creators have attempted numerous tactics for hiding their presence, traffic and locations of their command and control (CnC) servers.
To this end, we have seen the development of such things as DGA or Domain Generation Algorithms, which dynamically create new CnC addresses that are pre-created by the botnet owners to have their traffic move frequently to avoid detection/blocking.
We have also seen the use of TOR, the anonymous “under-web” used to host CnC servers with little likelihood that the owners of the servers would be discovered.
Although most of these advancements in botnet technology have been made specifically for the desktop, we are seeing a huge push to employ these same tactics on mobile platforms such as Android.
Today, an article posted by Roman Unuchek of Kaspersky described the discovery of the first “TOR Trojan for Android” and how cyber criminals have taken the source code for Orbot, a TOR network client for Android, and modified it with malicious functionality, such as that a Bot would have. These features include:
- Interception and hiding of all incoming / outgoing messages
- Interception of incoming / outgoing messages only from senders point of view
- Wiretapping incoming / outgoing messages without hiding them
- Sending messages from the device
- Execution of codes remotely as well as obtaining a response from the bot
- Request GPS coordinates and display them on Google Maps
Kaspersky uses the vendor name Backdoor.AndroidOS.Torec.a, however, we think the official name of this threat is “Slempo” and is a variation or evolution of the “Stoned Cat” botnet.
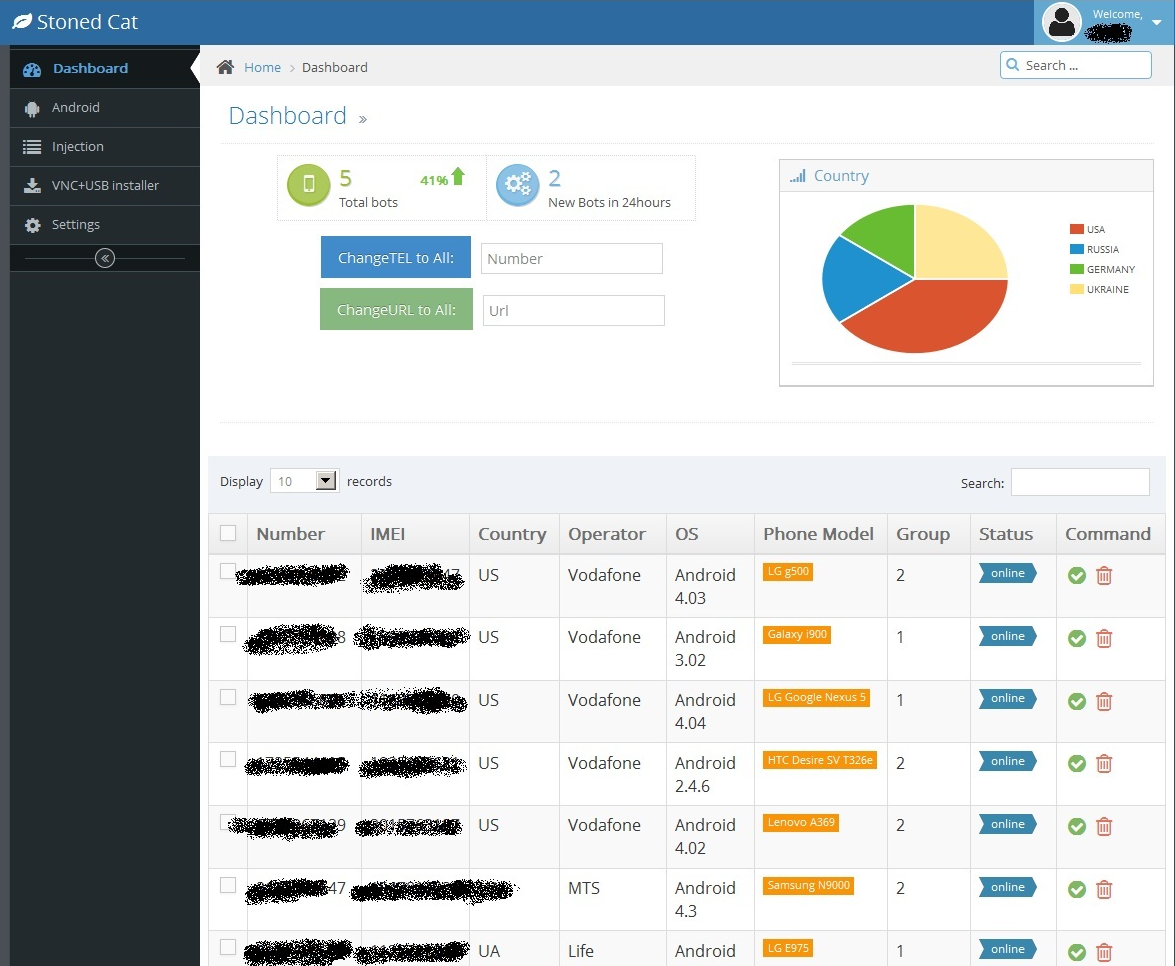
Advertisements for this new “Tor Botnet” includes all the functionality mentioned above and describes the Admin panel as being similar to the Stoned Cat interface. Here are a few screenshots to show you what that looks like:
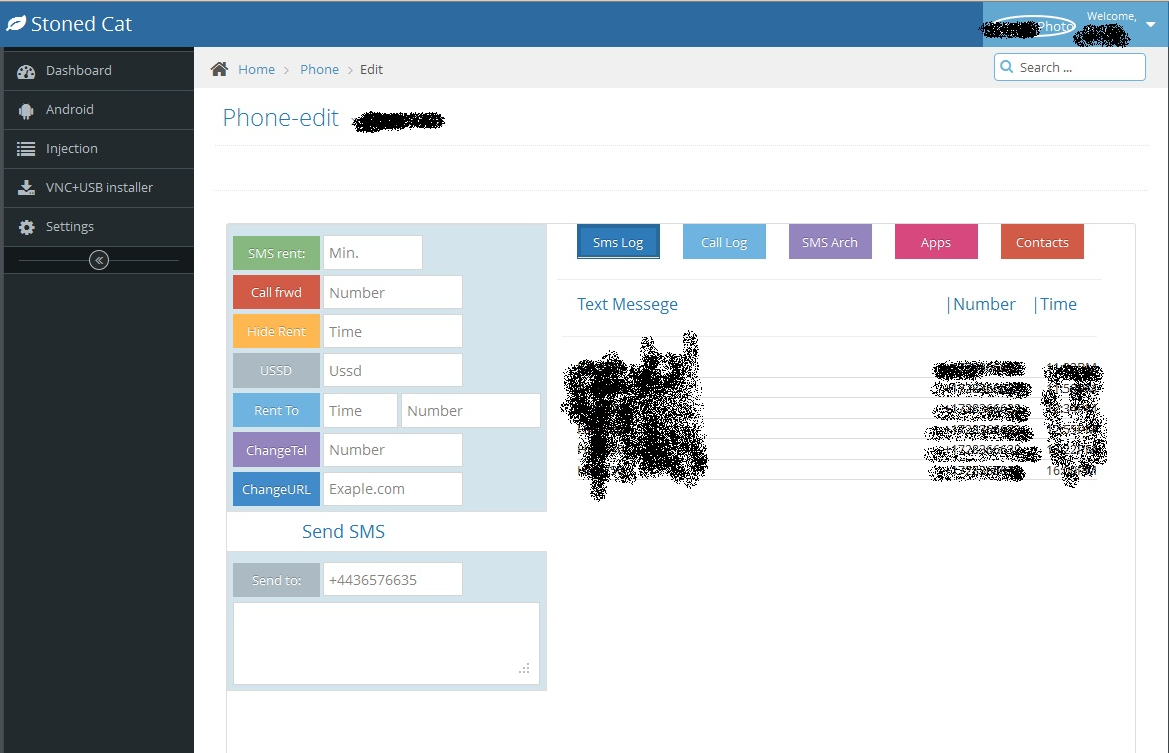
The current price for obtaining use of the Slempo botnet is $1,000 up front and $500 a month after that.
Unuchek makes some valid points concerning the use of TOR for botnets. On one side, using TOR makes it very difficult to shut down a CnC server and therefore, little concern over losing connection with the bots once they are installed on the mobile devices.
On the other hand, bundling the TOR software with the malware means it is very heavy and would be difficult to download, transfer and operate with much stealth.
I wanted to add that the use of the TOR network is never very efficient and sending data through it may or may not actually make it to the CnC as it might using normal internet methods.
We recommend keeping an eye out for any data usage increases from your mobile device, over-power consumption (running a constant TOR connection will no doubt drain your battery faster than otherwise) and any other kinds of odd behavior.
Be sure to update and run frequent scans with Malwarebytes Anti-Malware Mobile.
A special thanks to Kafeine for providing additional info on this topic.
Thanks for reading and safe surfing!