Did you know the term ‘malware’ refers to more than just viruses and worms? Did you know that there are types of malware that infect your system at so deep a level that the operating system doesn’t even realize they are there? Did you know that some malware could make the files, services and running processes associated with its operations invisible? This kind of malware is known as a rootkit and it is a serious problem in today’s computer security world. Many antivirus solutions have a hard time even detecting rootkit activity, let alone removing it. To answer the call in the fight against rootkits, Malwarebytes has taken up arms and introduced a new soldier in the cyber-war. Meet Malwarebytes Anti-Rootkit.
Disclaimer
Malwarebytes Anti-Rootkit, as you will find out in this blog post, is a very useful and powerful tool. However, it is currently in a BETA status, meaning that we are still testing it out and making sure that it works across all operating systems and with all users, it also means that we cannot guarantee that the software will perform error free. In saying that, there might be a chance that using this software could damage your system and you should use it AT YOUR OWN RISK. If you do decide to use this tool in its current state, you are agreeing to the terms of our license agreement, included with the software as “License.rtf”.
Please be sure to backup any valued data you have before you proceed to use this tool, just as a precaution. Finally, Malwarebytes bears no responsibility for issues that may arise during use of this tool, however all reasonable efforts will be made by Malwarebytes to assist in recovery should the need arise. Thanks!
What is a Rootkit?
A rootkit is a special type of malware that embeds itself deep into the operating system at a level that allows it to manipulate the information the operating system sends back to the user as well as applications. This means that rootkits can completely control the operating system as well as hide any presence of its existence.
Rootkits have been around for about 20 years and were originally developed for non-malicious purposes and not even for the Windows operating system. As the years progressed, it became apparent to cyber-criminals that the employment of rootkits was the way to go, and therefore, we have rootkit malware like ZeroAccess and Rustock.
The biggest issue with rootkits, beyond their intended operations, is how to get rid of them. See, rootkits embed themselves into the operating system in such a way that allows many legitimate and important function calls and data to be passed through their oversight. Think of it like a hard-water filter installed on your water pipe system right outside of the point where the water enters your house. If you tried to remove that filter, you would then have a problem with your water correctly getting into your house. In the same regard, if you removed a rootkit, you might inadvertently break some vital functionality of the operating system; in the worst case, it might even make your system un-bootable.
To put our foot down and fight back against stubborn rootkit malware, Malwarebytes has developed a new product designed specifically for the detection and removal of rootkits: Malwarebytes Anti-Rootkit.
What can it do?
At a high level, this is what Malwarebytes Anti-Rootkit, or ”MBAR”, can do for you:
- Kills what other tools cannot. Those nasty rootkits, MBR infectors and the nastiest of nasty Trojans and blended threats like ZeroAccess
- Goes well beyond other malware removal tools and repairs broken services and system files often damaged by many infections.
- The same incredible heuristics used by Malwarebytes Anti-Malware for detecting the latest 0-hour threats is applied to the anti-rootkit definitions used by MBAR to find and kill the latest rootkits
- It uses our Chameleon self-protection to keep it running even when threats try to shut it down
Malwarebytes Anti-Rootkit scans your systems drivers, hard drive sectors, and system files to seek out rootkit activity and remove it from your system. This means that MBAR will delve into the dark crevices of your system where rootkits like to hide and disrupt their ability to link into the operating system and modify data, disrupt system calls, etc.
Once it removes the links, it will use the Malwarebytes Anti-Rootkit engine to detect all additional rootkit files and set them for removal. After this, the system will require a restart that allows Malwarebytes Anti-Rootkit to remove the malware before it has a chance to embed itself into the system again.
Why is it necessary?
In the distant past, malware consisted of a few viruses that destroy data and worms that try to spread malware as far as they could. In those days, a simple antivirus/anti-malware solution would be the answer for nearly all computer security issues. However, currently we deal with much more advanced, targeted and nefarious types of malicious software such as rootkits. Therefore, it is necessary to be able to protect your system against these threats that conventional antivirus/anti-malware solutions cannot.
In addition, think back to the water filter analogy, where breaking the connection between the water filter and the pipes could cause serious damage to the water system. Malwarebytes Anti-Rootkit not only removes the rootkits or evil water filter but also repairs the damage it made to the system by reestablishing links and fixing vital services that had been modified by the rootkit, in essence it ensures that your water is flowing. It does this with a tool known as fixdamage.exe that is included with the Malwarebytes Anti-Rootkit ZIP file.
Where can I download it?
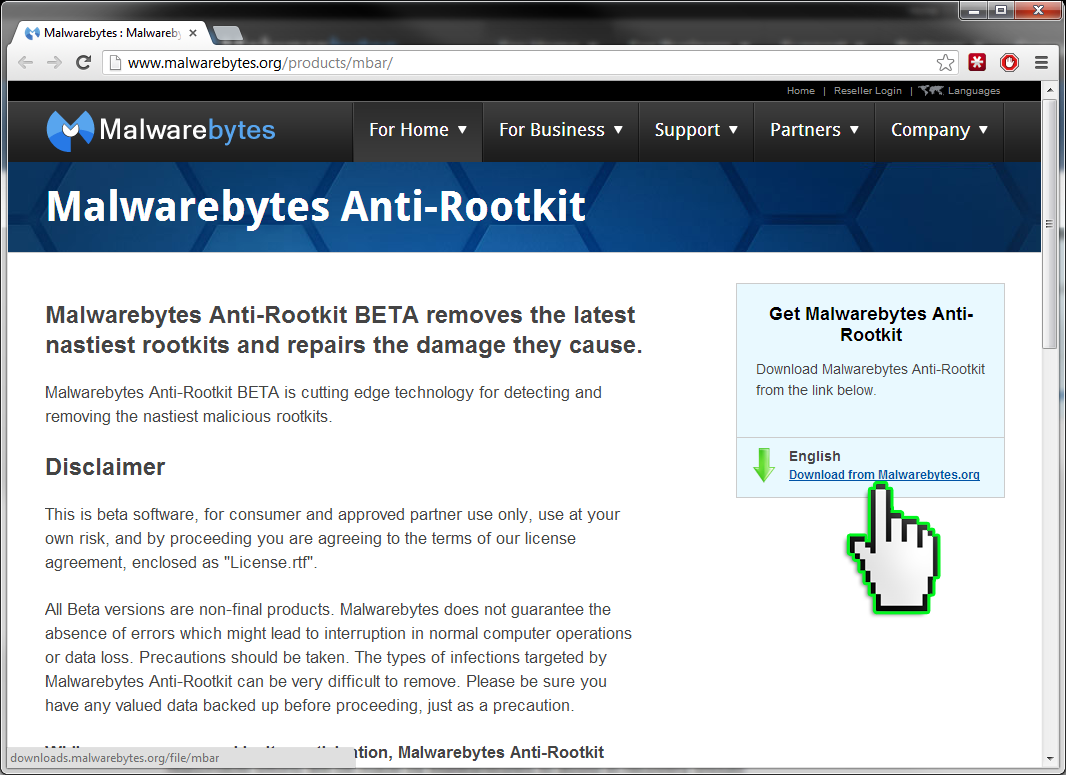
So now that you know what a rootkit is, what Malwarebytes Anti-Rootkit can do about them and how it does it, naturally want to try it out for yourself. To do this, just click the link below and download the ZIP file containing Malwarebytes Anti-Rootkit and read on to find out how to use it.
Download Malwarebytes Anti-Rootkit
How do I use it?
Here is a step-by-step breakdown on how to use Malwarebytes Anti-Rootkit.
- Download the ZIP file containing the MBAR files from the link above.
- Save the ZIP file and double click it to open it.
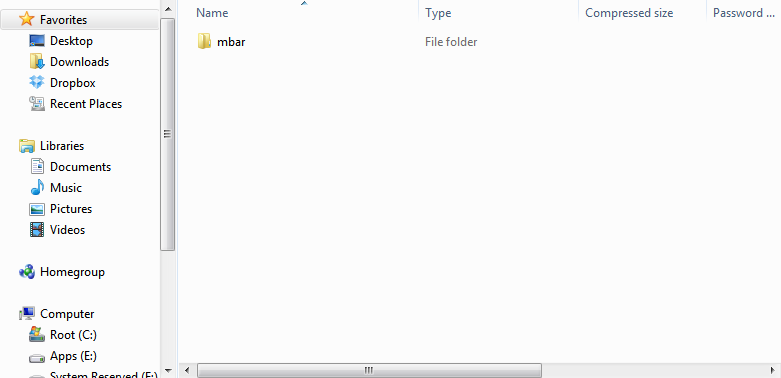
- Extract/Copy the “mbar” to your hard drive; you could put it on the Desktop or just in your root drive like “C:” it does not really matter. Once done, open the folder in your Windows Explorer.
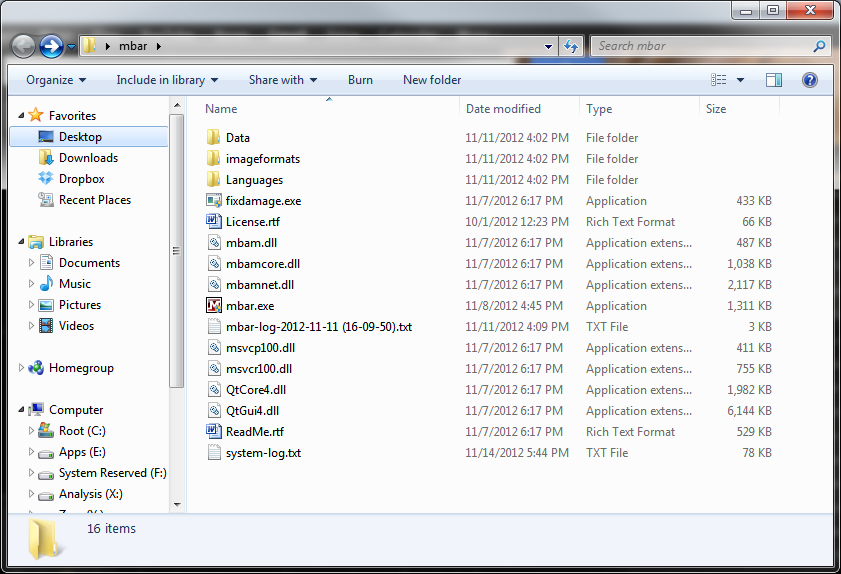
- We recommend you check out the “ReadMe.rtf” file for information on usage instructions and advanced command line parameters available for the tool in addition to the End-user License Agreement (EULA). It is a very useful resource for using this tool or if you want to learn even more about what it is capable of.
- To use Malwarebytes Anti-Rootkit simply click on the “mbar.exe” icon. MBAR does not require installation like Malwarebytes Anti-Malware does and can be used as soon as the files are extracted. If you are using Windows 7 or above, make sure to allow mbar.exe to use administrative privileges when prompted.

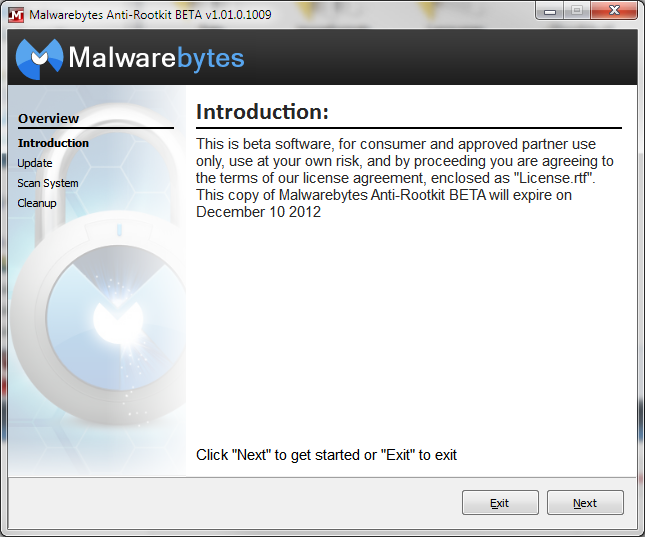
- Once executed, MBAR will present you with a graphic interface and an introduction about the product and informs you about the licensing of the tool. To continue, press “Next”.
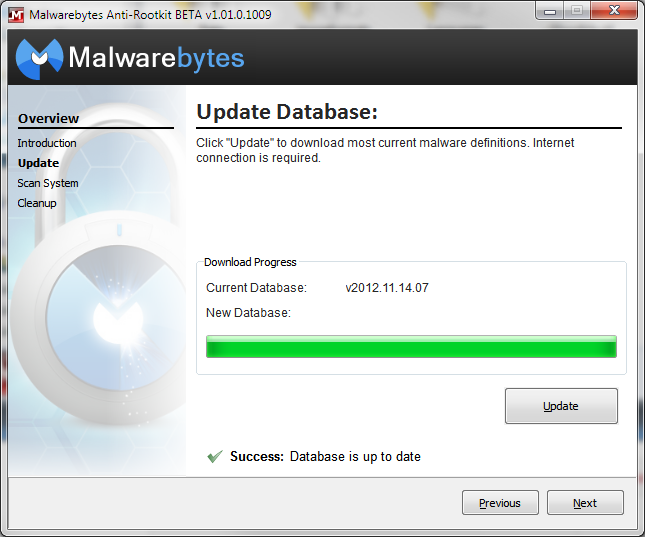
- Next, you are presented with the “Update” interface, which allows you to download the most current definitions from our Anti-Malware servers to be used to scan the system for rootkits. Click “Update” to download the newest database then click “Next” once it completes the update.
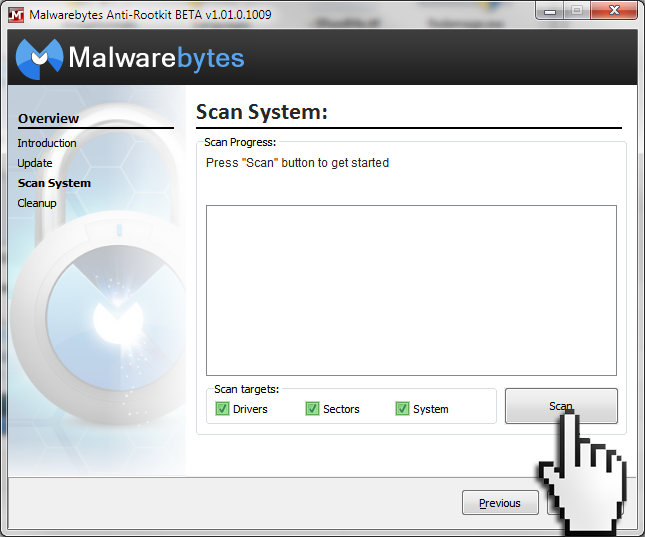
- You should now be at the “Scan System” interface; this is where you will allow MBAR to search your system for rootkit activity. To perform the most complete scan, make sure that the “Scan Targets” are set to all possible options (Drivers/Sectors/System). Then click “Scan” when you are ready.
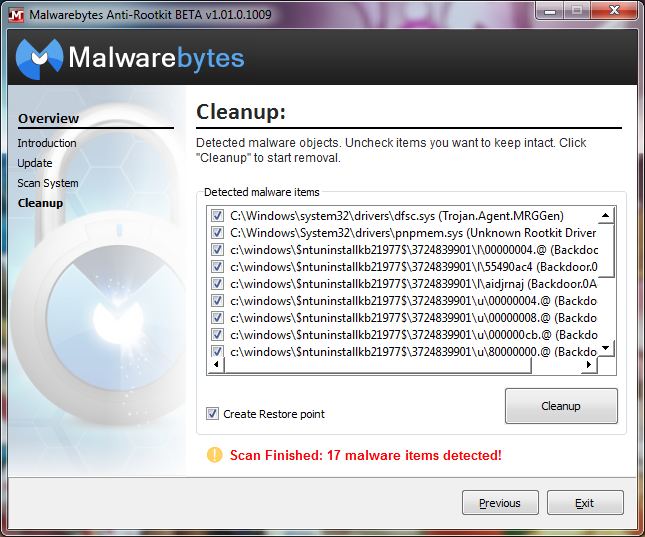
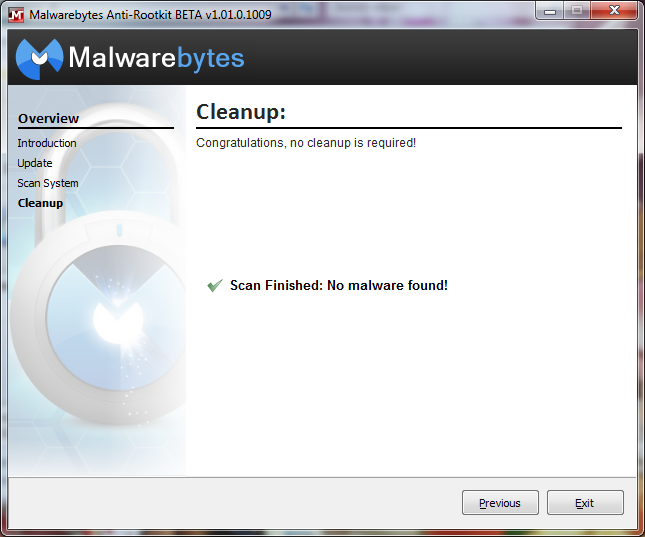
- Once the scan is complete, MBAR will inform you if it has detected any malware and will advise to you to clean your system. It also has a “Create Restore Point” option that we highly recommend you select in case something goes wrong with the removal of the rootkits.
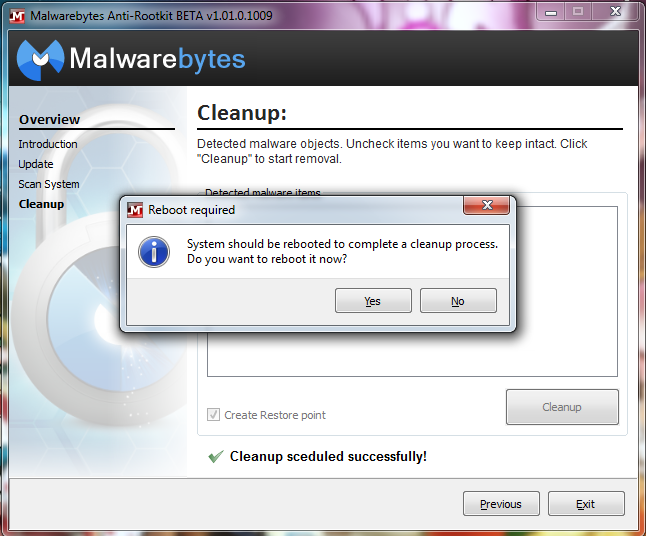
- After the restore point is created and the rootkit cleanup is scheduled, you will receive a prompt asking for a reboot of your system. Select “yes” to reboot your system and clean the rootkits.
11. After your reboot, you should run MBAR again to ensure that all infections have been removed from the system.
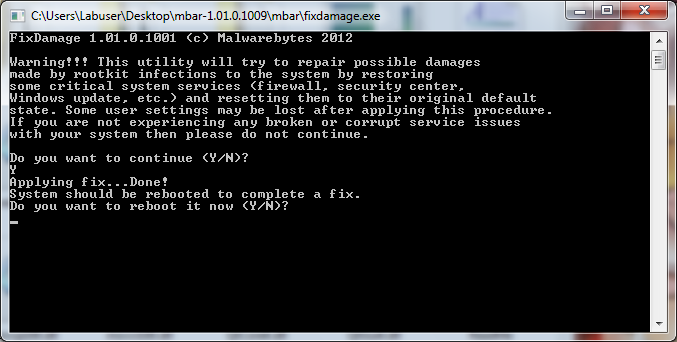
- Once you are rootkit free, in order to ensure that any damage done by removing the rootkit is repaired, you should run the “fixdamage.exe” application, located in the same MBAR directory as “mbar.exe”
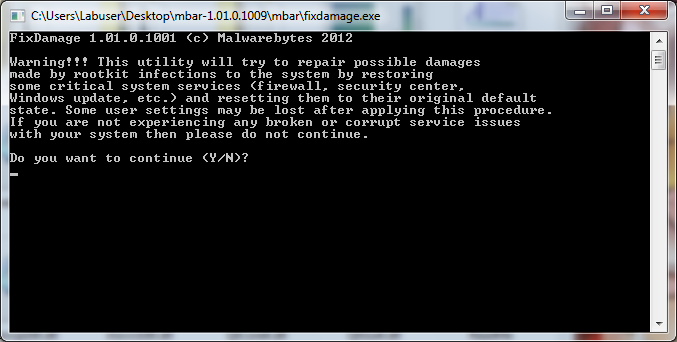
- Clicking on “fixdamage.exe” will open the console application and request confirmation to apply any fixes to the operating system. Input “Y” to being the fix.
- After the fix is complete, it will request you to restart the system again.
Keep in mind that Malwarebytes Anti-Rootkit does not require an installation of Malwarebytes Anti-Malware and makes it a great tool for quickly disinfecting the systems of your friends and family on the fly if they can’t install Anti-Malware because of the rootkit blocking them. Put it on a USB stick with an up to date definition file or onto a CD with other valuable tools.
This product will always be updated and upgraded in order to have the best chance of taking out the bad guys and defeating rootkits as they come out. If you want to help in this fight, please do, by letting us know on our forums what kind of experiences you have had with MBAR and even how you think it might be better. Thanks for reading and stay safe!