After my post about extensions, I received some requests to deal with another method of pretending to be a different type of file. If you have not read that article yet, it will prove helpful to do that first in order to better understand this post.
What is RTLO (aka RLO)?
The method called RTLO, or RLO, uses the method built into Windows to deal with languages that are written from right to left, the “Right to left override”.
Let’s say you want to use a right-to-left written language, like Hebrew or Arabic, on a site combined with a left-to-right written language like English or French. In this case, you would want bidirectional script support.
Bidirectional script support is the capability of a computer system to correctly display bi-directional text. In HTML we can use Unicode right-to-left marks and left-to-right marks to override the HTML bidirectional algorithm when it produces undesirable results:
left-to-right mark: ‎ or (U+200E)
right-to-left mark: ‏ or (U+200F)
How is RTLO being abused by malware writers?
On systems that support Unicode filenames, RTLO can be used to spoof fake extensions. To do this we need a hidden Unicode character in the file name, that will reverse the order of the characters that follow it.
Look for example at this file, a copy of HijackThis.exe, that I renamed using RTLO:
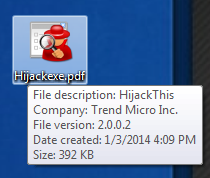
The last seven characters in the file name are displayed backwards because I inserted the RTLO character before those seven characters.
As discussed in the previous article, assigning a matching icon to a file is a triviality for a programmer. So here we have an executable file that seems to have the PDF extension.
Ironically, you will see straight through this deception if you are still running XP, since it does not support these file names:

The square symbol shows us where the Unicode RTLO character is placed.
One way to catch these fakes on more modern versions of Windows is to set the “Change your view” ruler to “Content”.
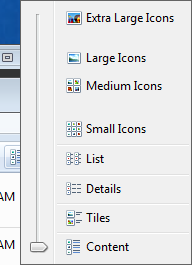
Set this way, you can see that the files are applications and not a PDF or jpg.
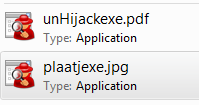
This may be a good idea for your “Download” folder(s), so you can check if you have downloaded what you expected to get.
Is the RTLO method actively being used?
The technique has been know for quite a while and is starting to re-surface. It is not only being used for filenames by the way.
A malware known as Sirefef (which Malwarebytes Anti-Malware detects as Trojan.Agent.EC ) uses the RTLO method to trick users into thinking that the entries it puts into the infected machine’s registry are legitimate ones, belonging to Google update.
Does this have any effect on the detection of these files?
No. Detection of malicious file is never done by a filename alone. So your AV and Malwarebytes Anti-Malware will still recognize these files if they were added to their detection, no matter what they are called or how they are written.
Summary: RTLO is used to fake extensions by writing part of the filename or other descriptions back to front. Although the detection by your AV or Malwarebytes Anti-Malware is not altered in any way this trick can be deceiving users at first glance.
Sources : http://www.ipa.go.jp/security/english/virus/press/201110/E_PR201110.html
http://threatpost.com/sirefef-malware-found-using-unicode-right-to-left-override-technique/102033