Not so long ago, I went up a mountain. A mountain which, you may be interested to know, sits roughly 5,000 ft above sea level and requires a bus ride that lasts between five and six hours to reach the top.

The road is a long, steep and very twisty hike up, often with little other than a few bricks and / or a somewhat flimsy looking metal barrier a couple of feet away to prevent you from going over the edge. In pouring rain with low visibility and moving at high speed, it’s even more
exciting.
To alleviate the boredom (and perhaps to distract you from the awful movies on the built-in TV), the attendant will give you an Android tablet to play with and make use of the in-bus Wi-Fi (it’s all very hi-tech, sometimes the bus has two routers to choose from and everything).
However, it seems everybody and their Uncle failed to follow some basic security precautions, because oh boy did I ever find a whole bunch of still logged-in accounts on these tablets (across multiple devices – I kept pretending I couldn’t connect to the Wi-Fi so the attendant gave me another one to look at in horror).
Email, Facebook, Twitter, you name it – I saw it, and could potentially access it. DMs, private messages, emails – nothing would have been safe, but for the fact that I’m not Dr. Evil and so spent the whole time logging everything out (hey, it was a six-hour trip).
Here’s a logged in Twitter account, which was set to private and not viewable to the outside world:
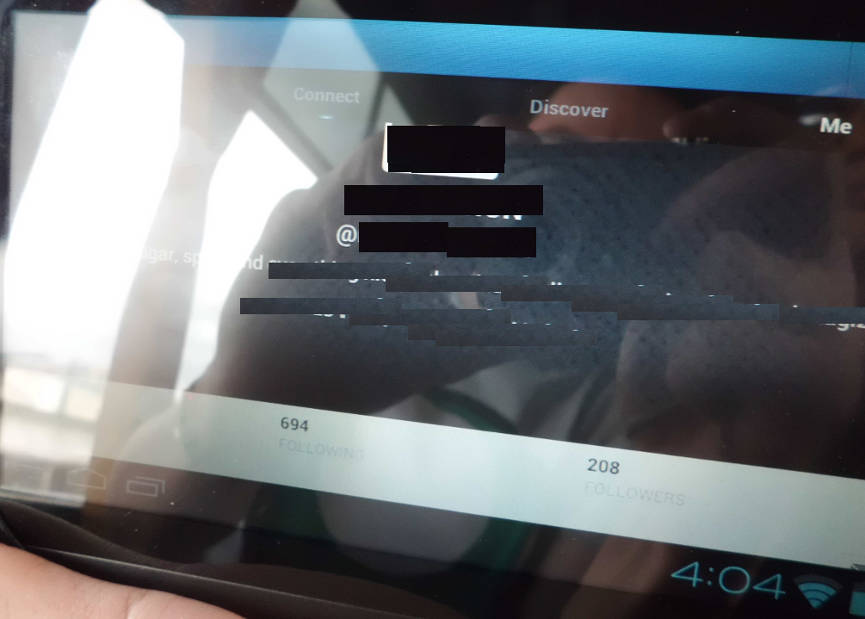
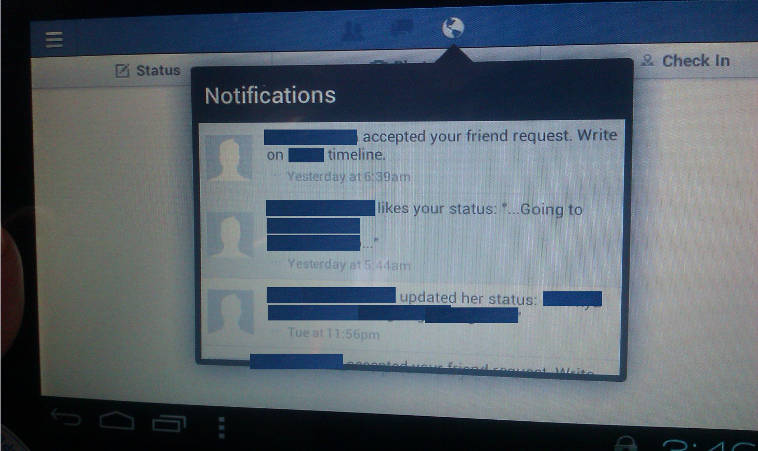
Everything in their DM box could have been mine for the taking. It’s a similar story with the following Facebook account, where private messages, notifications and other content were all up for grabs. If somebody had been in the mood for a “Send me money, I’m stuck up a mountain” scam this would have been their lucky day.
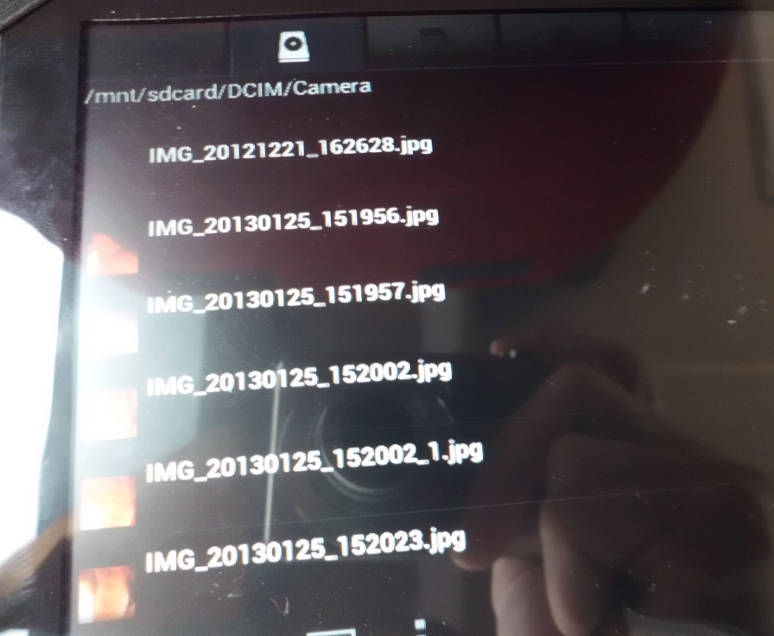
I even had a collection of selfies taken with the tablets and other images apparently downloaded from the various sites users were logged in on still left on the device.
Getting your hands on some free tech to fend off boredom is great, but if you can take the time to post up a bunch of cat pics and “Where I’m hanging out” messages on Facebook you can also surely take the time to scroll up and hit “Log out” at the end of your session.
Don’t rely on someone else to do it for you, whether you’re in a web cafe, library or an incredibly fast piece of mountain transportation. While it may surprise some to know that there are actually tutorials on not forgetting to log out of websites, I can see why so many people could potentially leave themselves logged in on an unfamiliar tablet.
The user experience can be vastly different between brands, and especially when using a non-branded device you only have access to for a few hours.
Handy Hints For Using an Unfamiliar Device
1) Which one is the Any Key?
This may sound silly, but when presented with a tablet so obscure it temporarily turns me into one of those chimpanzees wondering what that Monolith thing is all about I fire up the device browser (once I’ve found it) and simply Google “How to log out from [device x]”. You’ll usually find what you’re looking for, and you can be as vague or as app specific as you like.
2) Apps, and what to be wary of
These can be a nightmare to untangle yourself from safely, given the wide variety of ways they’ll let you login to them. Some can be tied to an account on the system itself, some have a more standard username / password which will also work on the web (but may not make it entirely clear how to log out) and many more variations besides.
Then there’s third-party apps alongside the “official” ones, whose log-out procedure may differ completely from (say) the official Twitter / Facebook / everyone else products. Worst case scenario, you’ll be forced to use whatever peculiar third-party app is pre-installed on the device and whose options all appear to be written in an ancient language waiting to be discovered by Indiana Jones.
Something else to keep in mind: you don’t know if the apps on that random tablet you’ve been given were pre-installed, or the person using it before you put it there. It might be legit, but it could be a scam app too just waiting to hit you with dubious permissions, stolen data and more besides.
Sometimes, end-users will think that just closing the app will log them out. This isn’t the case – many apps will remain logged in to enable you to switch between multiple apps on the go. Going into the device equivalent of Task Manager and “killing” the app probably won’t help either. If you’re at a complete loss, then locate the settings / applications menu and locate your app and hit the clear data / clear cache buttons (with clear data being the most important of the two options available).
3) Privacy is underrated
It seems that any number of features that could potentially reduce privacy in certain apps were enabled by default – various forms of “anonymous” data sharing, location services and so on. Some of the accounts we saw were protected, non-public accounts so it’s really rather amazing that they didn’t bother to log out. Then again, maybe they expected the bus stewardess to go around wiping all the devices clean at the end of the trip (good luck with that).
If the people using those devices weren’t too bothered (or didn’t notice) that they were still logged in, they probably may have missed that they were suddenly beaming their location info or other bits of data they’d rather hide from the world at large.
On any Android device you’re not familiar with, you should spend a little time digging out Privacy, Security and Location from the menu then ensure anything you’re not comfortable with is disabled.
As a final note of caution, remember you’re in a public space (yes, even in your mountain bus) and you should take note of whether you need a WiFi key to get online or if there’s no password – it’s often impossible for someone using a tablet to tell if an app is being as secure as it should be, and this is a problem that can affect even the biggest of social networks. Always be careful where public access is concerned, and – most importantly of all – don’t leave logging out in someone else’s hands.
You might end up leaving a lot more with them than you bargained for…
Christopher Boyd










