With news of Instagram finally beating Twitter in terms of overall usage, it’s high time that we stop, look back, and remind ourselves of the potential dangers lurking on the net specifically crafted to target Instagram users and lurkers alike.
In late March, the digital marketing research and analysis company eMarketers published data pointing out that Instagram surpassed Twitter in terms of active mobile users in the US by 2.7 million.
They expect numbers to steadily grow until at least 2016. For details on how eMarketers came up with and put together their data, we suggest you read their article entitled “Instagram Usage in the US Surges 35% in 2013, Rivals Twitter for Smartphone Audience“.
With reports such as this popping up every now and then, I, for one, can’t help but check for new, possible threats—files and sites alike—that take advantage of a software’s popularity and could spell bad news for users.
In the case of Instagram, what we’ve seen out there could pose greater risk than, say, your average phishing site.
Doing a Google search surely yields sites where one can download several programs involving Instagram. Some of which can either be classed as “image viewers” or “image and video downloaders” publicly-accessible accounts. Most of the files I sampled below belong to the latter:
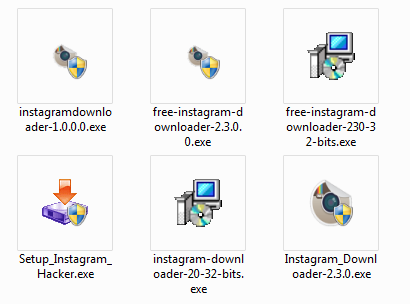
Mostly bundled files
Since Instagram can be visited via Web browsers, we can easily say that these downloads target any Windows computer user who just want to keep copies of photos and videos that are likely not their own.
We ran these potentially unwanted programs (PUPs) on VirusTotal and got the following information:
- File name: instagramdownloader-1.0.0.0.exe
- SHA256: d6495ffb6a0c388ae4d5b81c16ef4bdaee4604491b21d857d0955378336d4c84
- Detected as: PUP.Optional.OpenCandy (13/51)
- File name: instagramdownloader-1.0.0.0.exe
- SHA256: d6495ffb6a0c388ae4d5b81c16ef4bdaee4604491b21d857d0955378336d4c84
- Detected as: PUP.Optional.OpenCandy (9/51)
- File name: free-instagram-downloader-230-32-bits.exe
- SHA256: d65fd9b672bfc1093df20f0b9a7c6f812426c7b45085d04137d07b4a794830ba
- Detected as: PUP.Optional.InstallCore.A (12/52)
- File name: Setup_Instagram_Hacker.exe
- SHA256: ba2211beec48e3ea3e56b2e6374901133829c9451edb17a013cf0e3dadc4b37b
- Detected as: Trojan.Hacktool.Agent (7/52)
- File name: instagram-downloader-20-32-bits.exe
- SHA256: 7a855afccb23dedbb722b322d960b70ff63aa1c4dcdacf7c8c65a6f60748c829
- Detected as: PUP.Optional.InstallCore (12/51)
- File name: Instagram_Downloader-2.3.0.exe
- SHA256: 31538a48a02049d75facecec8d0ba028cbbe0e8e6918dab61346e7cdf926f62f
- Detected as: PUP.Optional.OpenCandy (13/51)
Of course, users of Malwarebytes Anti-Malware are protected from all these files.
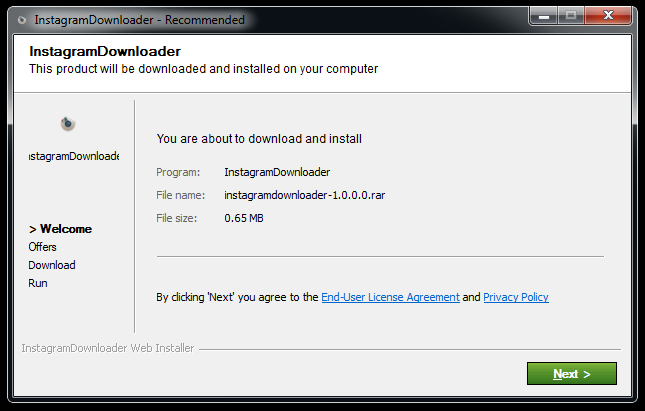
Sample download GUI of one of the files
Internet slowdown, unwanted redirection to sites and possible installation of other programs without the user’s consent are just some of the obvious signs users may experience once these programs are installed.
Like what we always advise our blog readers, please avoid downloading such programs onto your system as doing so will increase its security risks.
Jovi Umawing










