Rich Matteo, a researcher here at Malwarebytes, came across an interesting sample that erases files and leaves a not-so-friendly message to its victims.
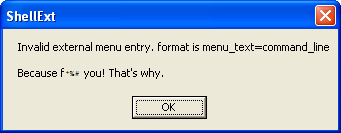
Once a host PC is infected, the malware enumerates the victim and looks for files of a certain type, replacing their contents with “Because f*** you! That’s why.”
Naturally, this can cause many programs to cease functioning, one of which was my Malcode Analyst Pack. This one produced some rather comical errors post infection.
Some quick static analysis of the file shows it’s a .NET Assembly that’s been obfuscated with SmartAssembly v6, a commercial obfuscator sold by Redgate. As mentioned before in my blogs, sometimes these products intended to be used by software developers to protect their Intellectual Property can also be used by malware authors to hide their evil deeds.
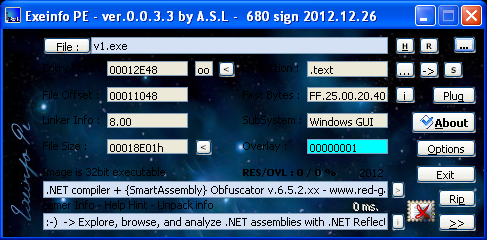
To unpack .NET assemblies we can use de4dot—a .NET assembly de-obfuscator—on the packed file.
De4dot is a command line tool and has a lot of options, so take time to read up on it to learn its full potential. To unpack this file I used the “-f” and “-o” options. The program will detect the obfuscator used during this process.
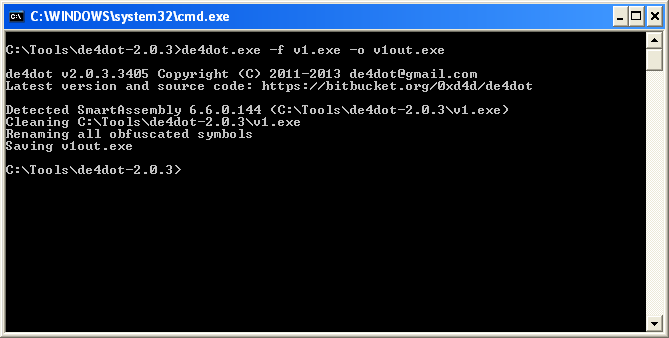
Once we get the output file we can see that the strings have been de-obfuscated. Looks like it will install a service for persistence. The malware author also takes the time to write out a Service description to make it sound somewhat believable.
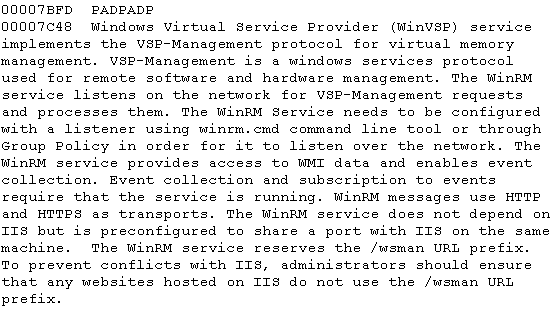
The Unicode strings also reveal a lot of pertinent information, including the file types targeted by the malware.
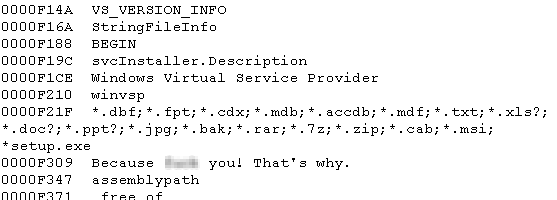
It’s not as common to see malware that operates in this fashion, almost seeming to play pranks on the user. Most of today’s modern malware tries to remain stealthy in order to avoid detection, unlike in this case where it starts trashing your computer, visibly disrupting your files and just causing headaches. This sort of malware is usually not the byproduct of a professional cyber-criminal, but rather people with too much time on their hands.
If you’re a Malwarebytes Anti-Malware PRO user, you are protected from this threat. This malware is detected as Trojan.MSIL.ST.
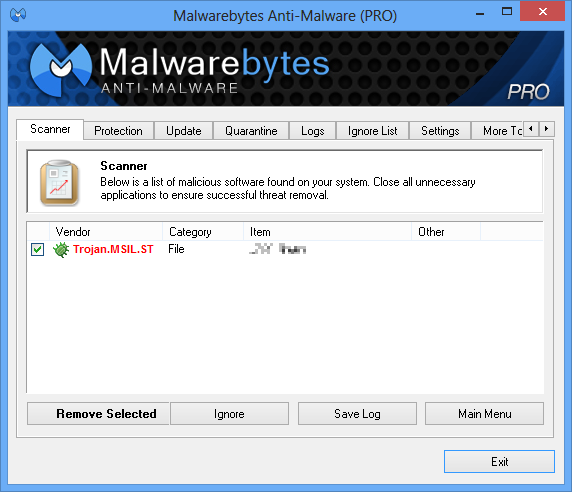
However, if the malware is detected post infection, the damage may have already been done to your files. The only way to reverse this process is to recover them from some sort of backup.
Backups are a great thing to have in case something goes wrong, like an equipment failure or in this case, a malware infection. There are several commercial options available for this: at Malwarebytes, we have our own solution known as Malwarebytes Secure Backup.
You can also try recovery options available in Windows. If you’re a Windows 8 user and you have File History enabled, that should do the trick (click here to learn more about this neat feature). If you’re not a Windows 8 user or you’re not using File History, you can always try the traditional approach using System Restore after the malware has been removed.
_______________________________________________________________________________
Joshua Cannell is a Malware Intelligence Analyst at Malwarebytes where he performs research and in-depth analysis on current malware threats. He has over 5 years of experience working with US defense intelligence agencies where he analyzed malware and developed defense strategies through reverse engineering techniques. His articles on the Unpacked blog feature the latest news in malware as well as full-length technical analysis. Follow him on Twitter @joshcannell









