Author’s Note: We at Malwarebytes continue to do our part in educating our product users and constant blog readers about day-to-day online threats and how they can avoid falling prey to them. “PUP Friday”, our latest attempt at getting users acquainted with files they may need to watch out for in the Wild Web, offers an in-depth look at some interesting and quite notable potentially unwanted programs (PUPs). Expect to see this type of content pushed out twice a month at the end of a work week.
After we wrote about the eFast browser a few weeks ago, we found another Chromium based browser that installs itself as the default browser and delivers advertisements.
CrossBrowse is a member of the Crossrider family of browser hijackers and adware, and we have seen it before when it just hijacked existing browsers. It still does that, but now it also removes the shortcuts to your default browser from the desktop, the start-menu and the taskbar while adding shortcuts to itself in these same places.

CrossBrowse grabs the file-associations for:
- htm
- html
- shtml
- webp
- xht
- xhtml
And the URL-assiociations (protocols):
- ftp
- http
- https
- irc
- mailto
- mms
- news
- nntp
- sms
- smsto
- tel
- urn
- webcal
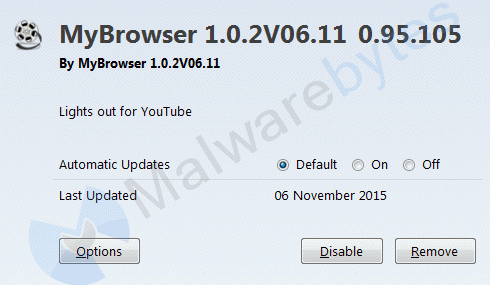
The Firefox extension is called MyBrowser
To ensure that your newly “installed” browser gets “runtime” it also creates two startup entries. One by dropping a link in the Startup folder and one by creating a Registry Run-key for the current user.
O4 - HKCU..Run: [GoogleChromeAutoLaunch_CF2B7C6F9D79411F351BC515B29E4ACE] "C:Program Files (x86)CrossbrowseCrossbrowseApplicationcrossbrowse.exe" --no-startup-windowO4 - Startup: crossbrowse.lnk = C:Program Files (x86)CrossbrowseCrossbrowseApplicationcrossbrowse.exe
Note the “GoogleChromeAutoLaunch” in the name of the Run-key which probably aims to mislead the user. And the use of the “–no-startup-window” switch which, according to their website:
does not automatically open a browser window on startup (used when launching Chrome (Chromium) for the purpose of hosting background apps).
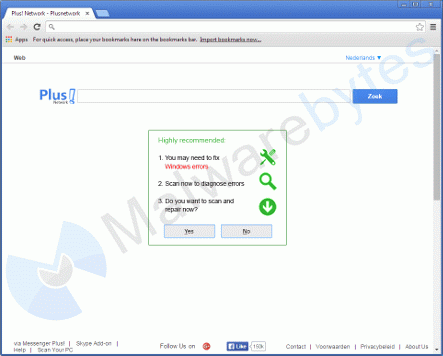
The first site it opens is plusnetwork[dot]com, which is notorious for the active hijacks to that domain.
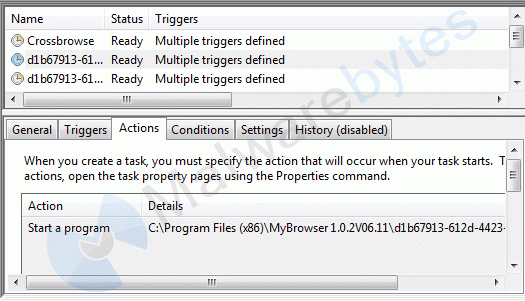
As a bonus there will be three Scheduled Tasks, one typical for CrossBrowse and two that are similar to the ones we see in most Crossrider installs.
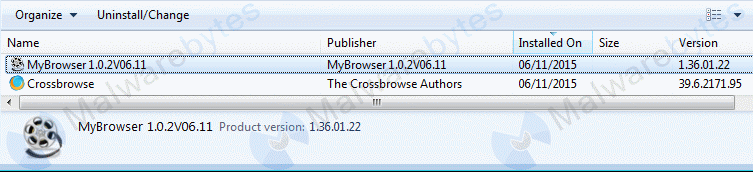
If you want to remove it using the Uninstall in “Control PanelProgramsPrograms and Features” be aware that there are two entries created by this install.
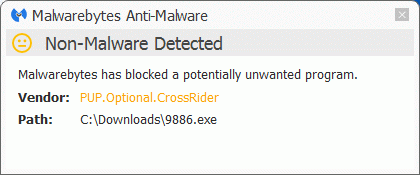
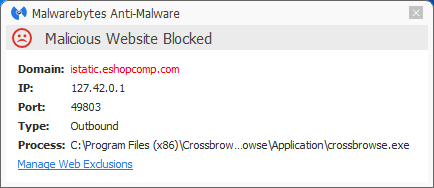
This family of browser hijackers will typically come from a bundle installer. The install and some of the connections the CrossBrowse browser tries to make are blocked by Malwarebytes Anti-Malware Premium. The installers are detected as PUP.Optional.CrossRider.
As always: “Save yourself the hassle and get protected.”
Resources
Pieter Arntz











