Today, we would like to discuss some very persistent Tech Support Scammers with you. After installing a file – which was offered as a “free version of PC Cleaner Pro” – Tech Support Scammers will try four methods to get you to call one of their numbers or connect to them using the legitimate program TeamViewer.
We can only guess in which way they will try and rob you blind if you end up falling for one of these, but we are pretty sure they will try.
But in case you don’t fall for these tricks, they have a few more in their “business model”.
Install
In the beginning, this looks a lot like the real thing. The start screen and the EULA of PC Cleaner Pro look real enough. Unless you spot the “Adobe” part in the form name.
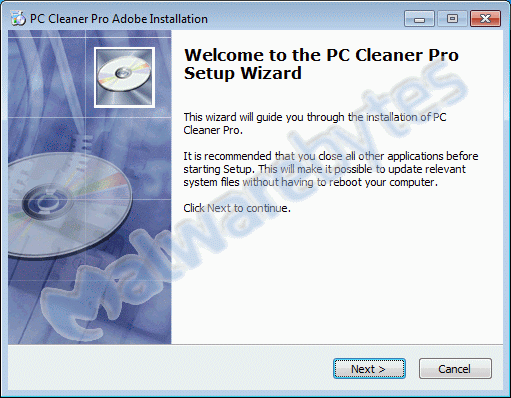
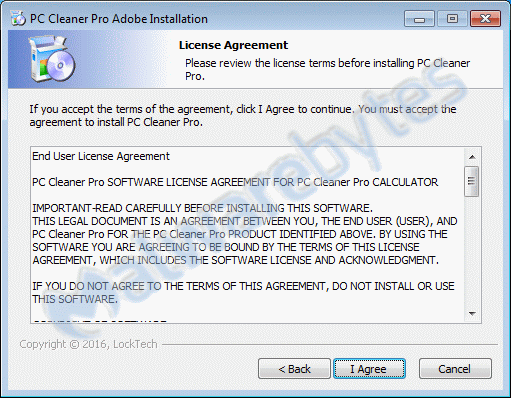
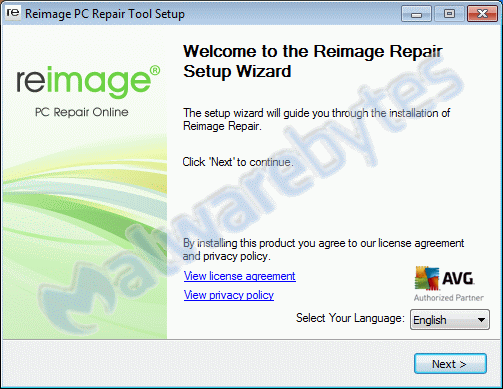
But, even before the installer itself has finished, we notice a few even less expected events:
- We are prompted that we will get an install of Reimage Repair.
- A browser window opens with a fake – BSOD resembling – screen and an alarming popup.
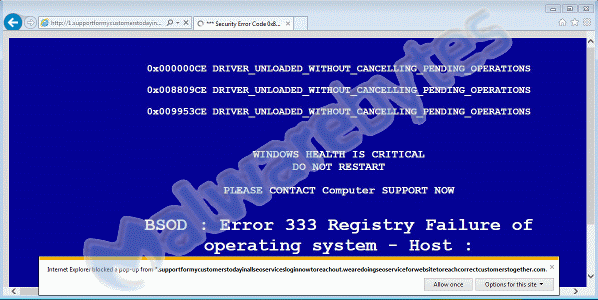

Easy enough to resolve these two by cancelling the Reimage Repair installation and killing the iexplore processes with Task Manager, but that is not the end of it. This browser window was only method #1.
Other methods
For the other methods to pop up, you will need a bit more patience. Method #2 is a Scheduled Task the installer put on the system.

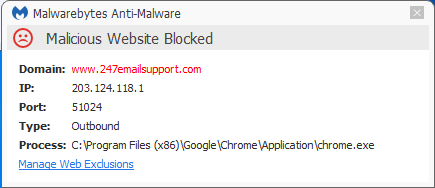
If this task is run, t.bat will try to open a Chrome browser window to www[dot]247emailsupport[dot]com, which is blocked by the “Malicious Website Protection” included in Malwarebytes Anti-Malware Premium.
Methods #3 and #4 will wait for a reboot of the system. To achieve this, the installer created two Run keys in the registry:
[HKEY_LOCAL_MACHINESOFTWAREWow6432NodeMicrosoftWindowsCurrentVersionRun] "tv"="REG_SZ", "C:Program Files (x86)PC Cleaner ProTV.exe" "WLrt1"="REG_SZ", "C:Program Files (x86)AdobeWLrt1.exe"
TV.exe is a customized version of TeamViewer, a program which is popular to provide remote support. In this case (#3 if you are still counting), it looks like this:

And last but certainly not least, WLrt1.exe is a customized version of ClearLock, an older program that was used to lock your computer in case you left it unattended for a while. The scammers have set a password – encoded and stored as such in the file ClearLock.ini – which you will need to unlock the computer.
If you want to bypass this screen, rebooting the computer into Safe Mode will not activate the screenlock, and you can remove either WLrt1.exe or ClearLock.ini (without ClearLock.ini, ClearLock assumes that the password is not set yet). This method (#4) presents itself like this:
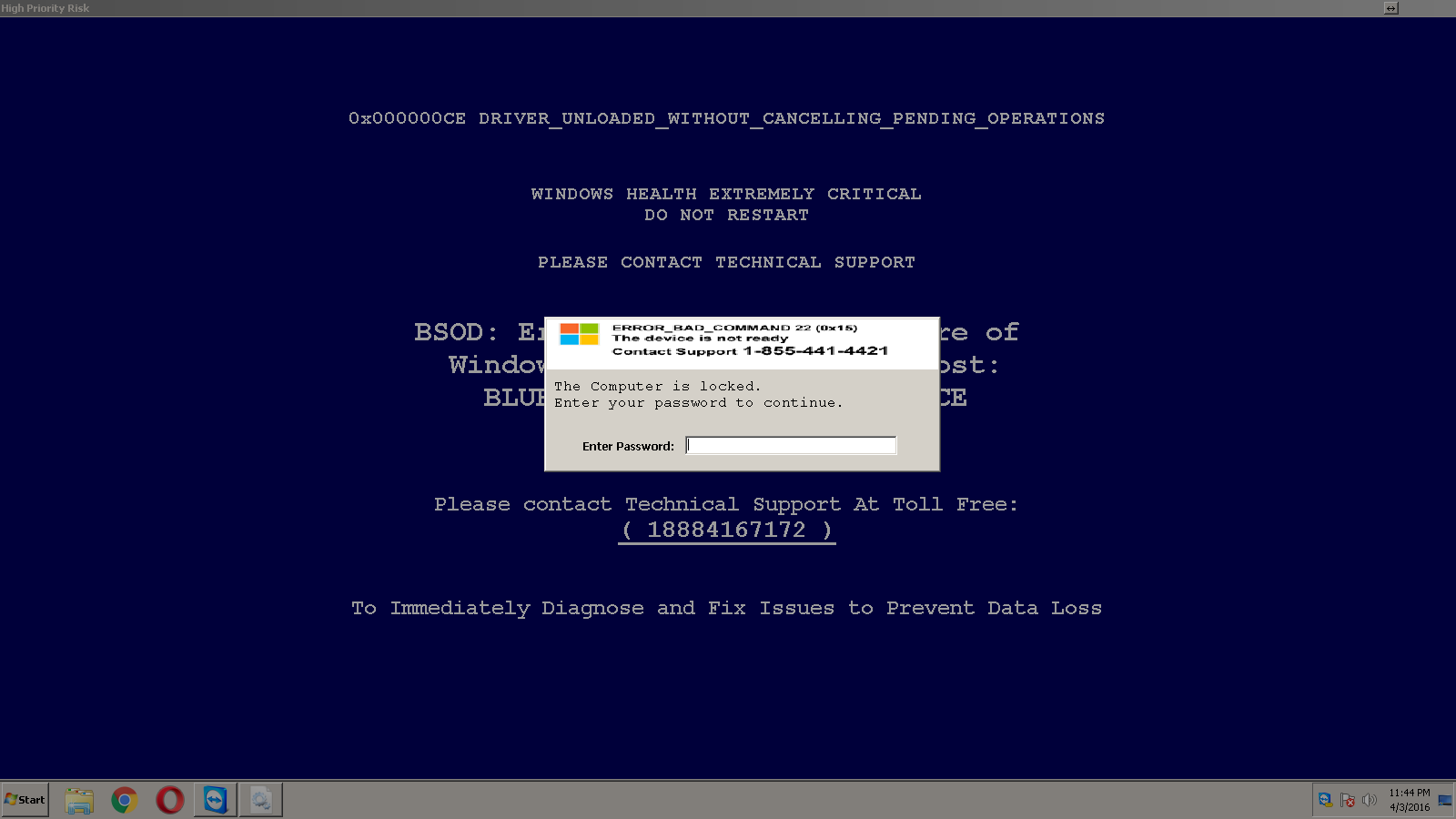
I tried to reach the publisher of ClearLock, but their website vanished somewhere around 2012. I found this archived version of the site, but that didn’t offer many clues as to who the author might be. I tried to find them, because we think the password might be the same for every install. We are now looking if we can free up some resources to reverse engineer the encoding.
Edit: The password is “microsoft” as one of our esteemed readers was able to figure out.
Extra money
The scammers would have gotten paid for every successful installation of Reimage Repair, if we hadn’t reported them and as a consequence of their methods, their account was nullified. You’re welcome.
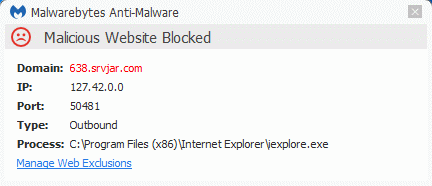
They also try and fetch some advertisements from srvjar[dot]com which is also blocked by our “Malicious Website Protection”.
File details of the installer
Md5: e17c966ec5ebfed8d7c0c171d5339487
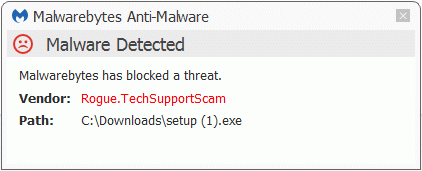
The installer is detected by Malwarebytes Anti-Malware as Rogue.TechSupportScam
Phone numbers involved: 1-855-441-4421 1-888-416-7172
The first number was previously used by microsoftofficelivesupports[dot]com who have a few other (previous) phone numbers in common with rtechnicalsupport[dot]com.
If you would like to know more about how this type of scammers cooperate, I can recommend this post by ICEBREAKR.
Summary
As tech support scammers go, this one is very persistent. Using four different methods to lure victims into their trap is something I have never seen before.
Pieter Arntz











