The trade in stolen nude celebrity shots may have died down somewhat since The Fappening was once a-happening, but that doesn’t mean the subject has gone away completely. Indeed, a popular forum devoted to leaked nudes has apparently been compromised:
Whoops.
Double whoops.
Curiously, the forum itself doesn’t seem to have posted any “RUN FOR THE HILLS” type messages since news of the breach went live, but having said that forum activity in general seems to have died down for the most part as the mass leak serving as its genesis fades into memory.
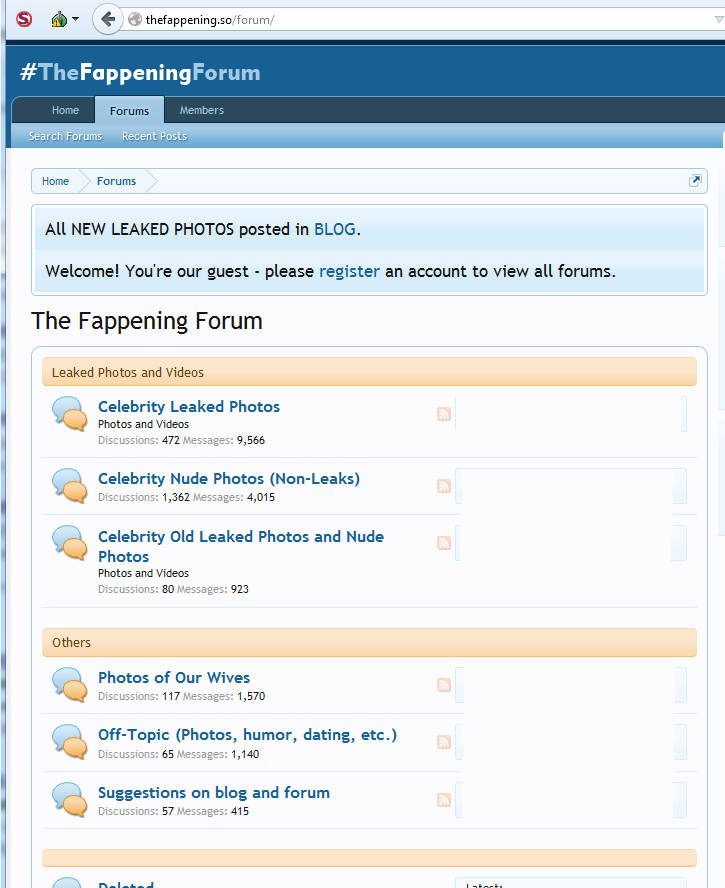
All the same, this one has the potential to cause all sorts of Ashley Madison style problems as the data is pored over, alongside a planet sized dollop of irony. If you did register on the forum at some point way back when, you may be in line for an unpleasant surprise in the near future.
However, we’re not here to talk about the hack, fascinating as it may be. No, we’re here to take a look at some of the adverts being served up by the site on mobile. We didn’t see anything like the below taking place when on a desktop, but with a handheld device things quickly went South. What we have here is a perfect storm of compromised forum accounts, dubiously worded advertisements, Malvertisements (Malverts for short), rogue mobile programs and more besides.
Shall we take a look?
Let’s begin with a pornographic popup complete with a download you really don’t want to be running on your mobile:
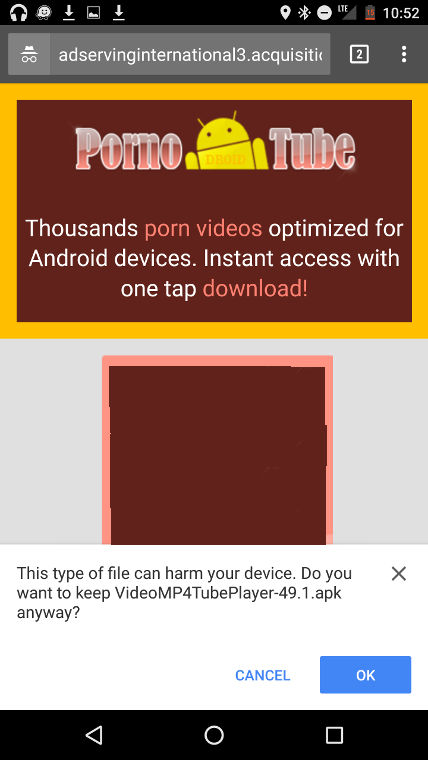
The file name is VideoMP4TubePlayer-49.1.apk, and Malwarebytes Anti-Malware Mobile detects this as SLocker (here’s the Virustotal page). The file isn’t being downloaded from the Google Play store, so you’d need to have specifically allowed non play apps to be installed beforehand, but this isn’t particularly uncommon. Even so, most people don’t tend to disable this safety feature so hopefully not too many would be caught by this.
That isn’t our only slice of Ransomware on display here, though it is the only download. We also encountered a number of different redirects to various website based versions of Ransomware (ie websites which “lock” you onto the page using various scripts, popups, and other diversionary tactics to keep you on the site at all costs). We’ve combined screens from a few of these sites to give you an idea of how they operate.
The first thing to appear on one of our sample sites is a UN Logo splash, because they really want the victim to think they’re looking at something official.

It isn’t long before the frankly scary warning messages start popping up:
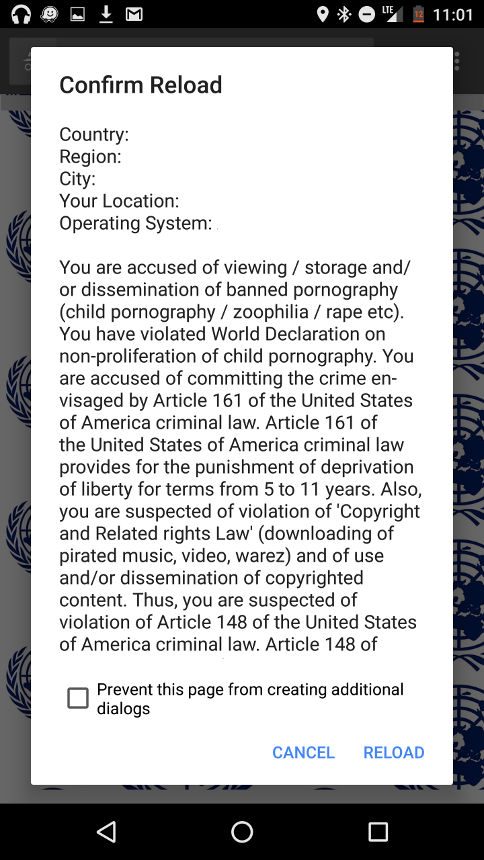
Country: Region: City: Your location: Operating system:
Keep in mind, this isn’t a piece of software which will, quite literally, hijack the device. It’s “just” a website, albeit a persistent one which wants the visitor to click something / enter information to make the barrage of popup messages stop. What are they going to ask for? Well, as we’ll see from one of the other URLs…

ATTENTION! Your mobile device has been blocked up for safety reasons. AUDIO AND VIDEO RECORDING IN PROGRESS. Amount of fine is 100$. You can settle the fine with iTunes Gift Cards. TYPE YOUR CODE (100$ iTunes Gift Card). AND PRESS 'OK'
That’s right – the UN, after telling the site visitor all about the terrible things they’ve been doing on their device, will let them off with it if they send them some iTunes gift codes. They also list pretty much every store in existence just in case the victim isn’t entirely sure where to buy some from.
Behold, the final link in the chain should the victim enter a code:
THE PASS YOU ENTERED IS BEING PROCESSED. REPEATED ENTERING WILL NOT MAKE PROCESS FASTER. DO NOT TRY TO CANCEL THE VOUCHER ENTERED, OR YOUR MOBILE DEVICE WILL BE BLOCKED UP UNTIL LEGAL RESOLUTION. VOUCHER PASS PROCESSING CAN TAKE AS LONG AS 48 HOURS.
While this all sounds faintly comical, it’s worth keeping in mind that Ransomware scare messages along the lines of the ones above can have terrible consequences for those unfortunate enough to witness them [1], [2]. Whether asking for money, Bitcoins, gift cards or something else entirely, the initial trauma of receiving these phony blackmail demands can be extremely severe.
We’ve even seen some other types of ad in rotation, such as the below “You have a Virus” splash screen with a Google theme and red font countdown timer:
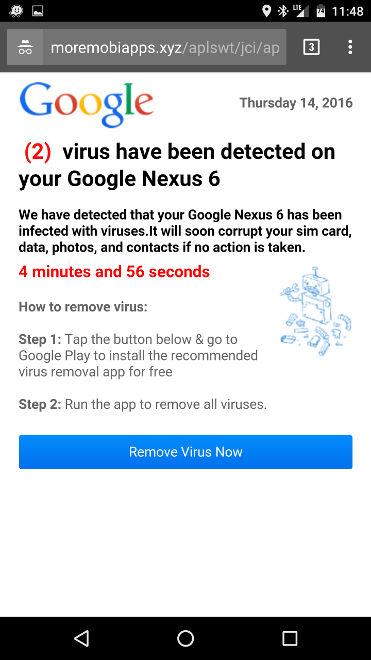
(2) virus have been detected on your Google Nexus 6
The advert leads to the below Google Play download:

People leaving reviews on the App are apparently not too pleased about the adverts which are bringing them to the download page:
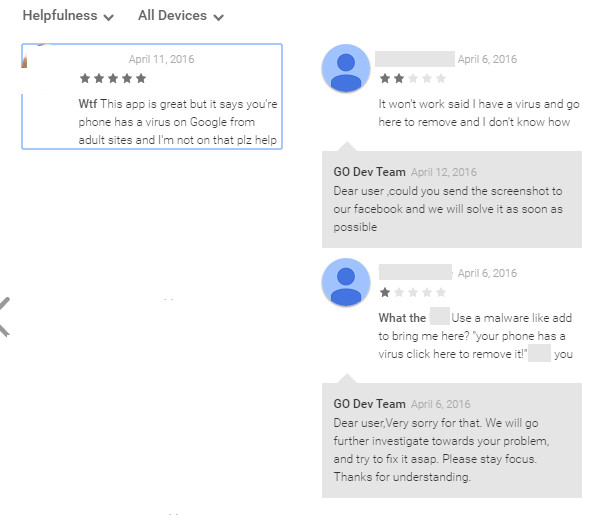
This app is great but it says you're [sic] phone has a virus on Google from adult sites and I'm not on that plz help
Like we said: a perfect storm.
We advise everyone reading this to be extremely careful where their mobiles are concerned – Ransomware and ransom fakeouts aren’t just exclusively reserved for the desktop, and a site serving up rotating adverts like the above can quickly lead to chaos for a device owner. As for the forum, it’s a foregone conclusion at this point that registering on such portals can only ever end in disaster. While the fallout likely won’t be anything close to the Ashley Madison hack, it’ll no doubt still be a slow burn of problems and headaches for anyone involved…
Christopher Boyd (Thanks to Adam T and William Tsing for additional information)










