DISCLAIMER: THIS POST INCLUDES SOME LANGUAGE AND TOPICS THAT MIGHT NOT BE SUITABLE FOR ALL READERS, PLEASE BE ADVISED AND PROCEED WITH CAUTION.
Update 2/18/15:
RedTube has confirmed the incident and said they addressed the hack:
The continuing proliferation of malware attacks have made them a concern for any organization. This past Sunday, leading provider of adult content RedTube was exposed to an attack for a brief period of time. Our security systems immediately detected the breach and we took direct action to rectify the situation in order to protect RedTube users. The situation was fully resolved by Sunday evening and there is no longer any risk to visiting RedTube. Redtube pursues stringent privacy requirements and maintains the highest industry standards of privacy protection to secure not only their assets and properties, but to provide comprehensive protection of their customers’ data when visiting a Redtube owned site. Redtube is committed to providing their customers with an optimal online experience and the peace of mind when they are accessing a RedTube site.
As always we urge people to still use caution and keep their computers protected.
Original Story:
We’ve documented adult sites leading to malware before on this blog, but this one is a little bit different.
This time around, the source of the problem is not malvertising, but rather a malicious iframe placed directly in the source code of redtube[dot]com, a pornographic site that boasts over 300 million visits a month.
Overview
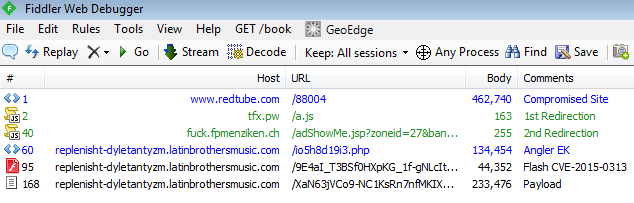
iframes
The attack doesn’t come from a malicious advertisement being loaded on the webpage, like was the case with xHamster, but rather the source code of RedTubes main page was modified to include a hidden piece of redirection code.
The code is executed inside of an iFrame, which is basically like a browser window inside of your browser window that can point to any website the attacker wants. In this case the iFrame is set to be completely invisible to the user and navigates to the following malicious URLs:
hxxp://tfx.pw/a.js hxxp://fuck.fpmenziken.ch/adShowMe.jsp?zoneid=27&bannerid=2&chid=341aa8fca26bcff7830499c1c5f8e359
The existence of the iFrame in the main page source code is evidence enough to say that RedTube servers were likely hacked by malicious actors who had access to the main page source code, adding the malicious code and then setting it loose on RedTube users.
Exploit Kit (Angler EK)
The Angler Exploit Kit has been one of the more prominent exploit kits on the cyber black market for the last year, being used in zero day attacks against applications like Flash and Silverlight. It’s instance in this case doesn’t use a zero day exploit, however it’s ability to quickly and effectively infect a user with malware is what makes it so popular among cybercriminals. The pages directly involved with the exploit kit are as follows:
hxxp://replenisht-dyletantyzm.latinbrothersmusic.com/io5h8d19i3.php hxxp://replenisht-dyletantyzm.latinbrothersmusic.com/9E4aI_T3BSf0HXpKG_1f-gNLcItlXc8fnVsgRFGib8jC_hw-ySQKzEHvsQP08slM hxxp://replenisht-dyletantyzm.latinbrothersmusic.com/XaN63jVCo9-NC1KsRn7nfMKIXpGreKpqo8UDRna5HHoBKjrIcRWibrIW1Av8mk4K
Angler EK uses the more recently discovered Flash Exploit CVE-2015-0313 (Zero-Day) and once it exploits the user’s browser, will attempt to drop malware detected by Malwarebytes Anti-Malware as Trojan.FakeMS.Ed. Other security vendors detect the malware as belonging to the Kazy Trojan family.
This family is known for stealing personal information from users as well as installing browser helper objects that spread pop-up ads, some redirecting to additional exploit pages and therefore more malware infections.
Anti-Exploit protection
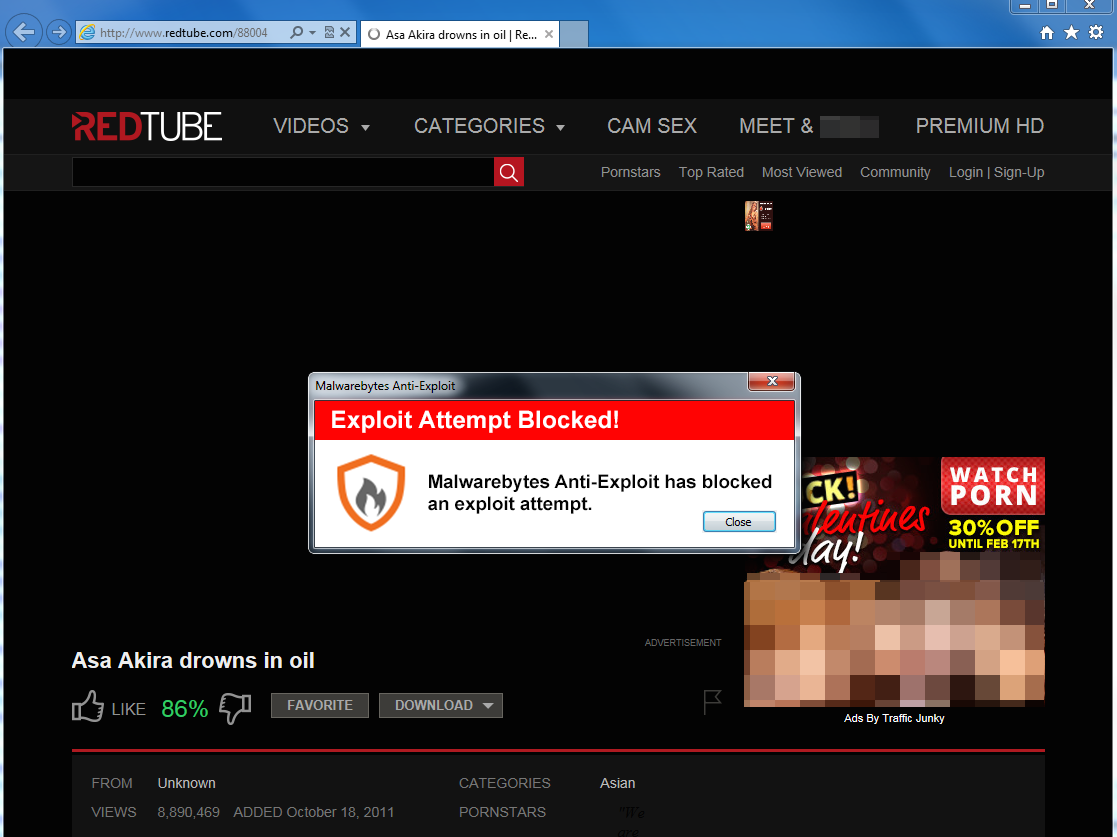
Malwarebytes Anti-Exploit proactively detects and blocks the exploit before it gets the chance to download and run malware.
Exploit infections, either through drive-by methods, malvertisement or malicious iFrame injections have been a problem for users and organizations alike for years and rather than it slowing down, new discoveries in attach technology has only increased the amount of attacks happening every month.
It is then highly advised that looking into anti-exploit, malicious webpage blocking and advertisement blocking solutions is in the best interest of all users.










