Security company Sucuri recently noted a spike in WordPress infections, with a large number of sites getting injected with the same malicious scripts.
Hacked websites are often used to host spam or perform malicious redirections to exploit kits and this case is no different. What makes it interesting is the volume and singularities that tie it to the same campaign.
WordPress sites are injected with huge blurbs of rogue code that performs a silent redirection to domains appearing to be hosting ads. This is a distraction (and fraud) as the ad is stuffed with more code that sends visitors to the Nuclear Exploit Kit.
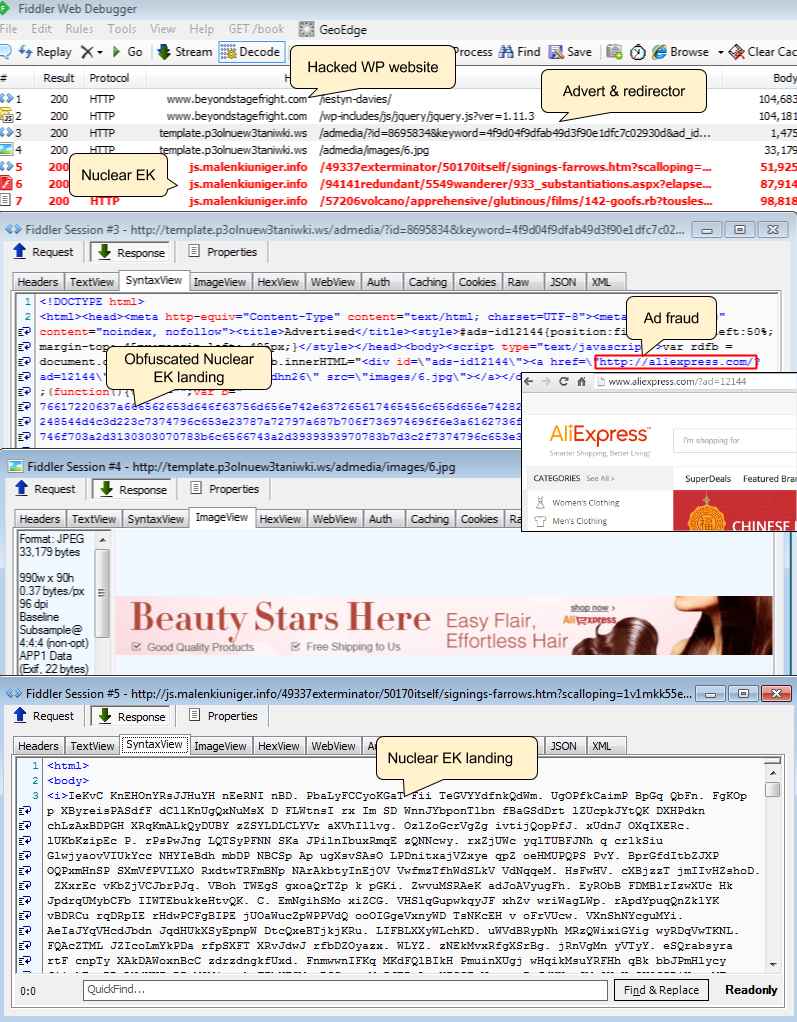
We can’t really call this attack malvertising though, since the domains used for this campaign are clearly not made to look like an advertiser. There is however an ad fraud component for every malicious redirection as we observed the following URL being loaded: aliexpress.com/?ad=12144
The payload dropped by Nuclear EK is detected as Backdoor.Andromeda by Malwarebytes Anti-Malware. Users running Malwarebytes Anti-Exploit never even got to see the malware dropped since the EK was blocked before it could even launch it.










