If you’re a heavy user of Tumblr, you may well have run into their daily posting limit which based on the numerous posts I’ve seen appears to be 250 posts a day and up to 1,000 likes (you can use this tool to see how many posts you have left until the daily timer resets).
Trying to get around the post limit is a frequent subject of discussion, and I happened to notice the following warning appearing on a number of blogs I follow:
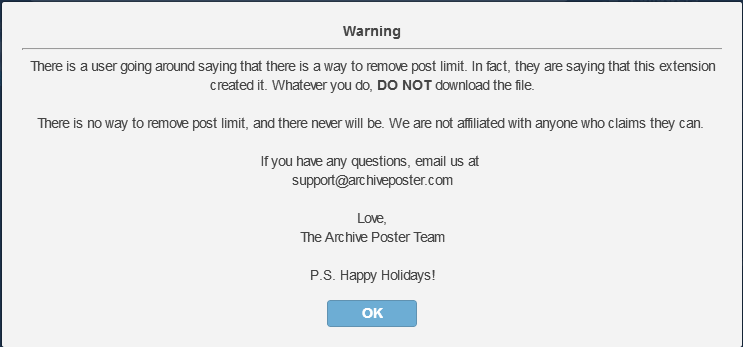
“Warning
There is a user going around saying that there is a way to remove post limit. In fact, they are saying that this extension created it. Whatever you do, DO NOT download the file.
There is no way to remove the post limit, and there never will be. We are not affiliated with anyone who claims they can.
If you have any questions, email us at
[removed]ATarchiveposter
The Archive Poster Team”
So, the scene is set: malware authors riding on the coat-tails of a well-known Tumblr extension called “Archive Poster”, hoping to fool those familiar with said extension into running their files.
Archive Poster is a Chrome extension which apparently lets Tumblr users “Quickly Reblog and Queue right from a blog’s archive”. I emailed the above address for more information, and they sent me back a copy of the rogue file and the HTML of the now deleted promo post encouraging end-users to download some malware. So hey, thanks for that!
The promo post for the rogue file reads as follows, and I’ve set the most dubious lines in bold:
“Tumblr Unlimited Posts Extension:
In honor and gratitude to my fellow promotional gainers, I present you with the following:
As we are all aware, there has been a recent extension released publicly to Tumblr known as the Archive Poster, or queue+. The administrators of Archive Poster and myself have worked together to create an additional extension for Unlimited Posts on Tumblr.
With the Unlimited Posts feature, this extension rids the annoying post limit that is set for each individual account, although this does not include the Ask Limit!
Extension may be found [download link removed]here!
Included in the link: Unlimited Posts Extension exe. file, instructions on how to use the extension.
Note: The Tumblr Unlimited Posts Extension is still in BETA and is downloaded as an .exe file because it is currently only supported by a Windows Operating System.
Enjoy, and if you have ANY questions, please message me back!”
We already know claims of having worked with the creators of the Chrome app are false given the “Nothing to do with us” warnings bouncing across Tumblr, but claiming the new so-called “extension” has to be an executable file should hopefully have set some alarm bells ringing.
Victims were directed to a .rar sitting on free file hosting, containing a text file and the executable. However, the people who made this don’t get off to a great start because after extracting the files you’d only see the text file unless the executable was in a folder set to “view hidden files”.
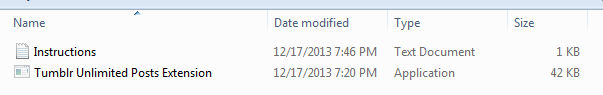
I can’t help but feel this would be an impediment to spreading malware, but I’m not complaining (and it would take anybody who actually wanted to use this about five seconds of Googling to unhide the file). Here’s the instructions, which tell the end-user to log out of Tumblr, run the executable (“open the extension”) and then log back in:
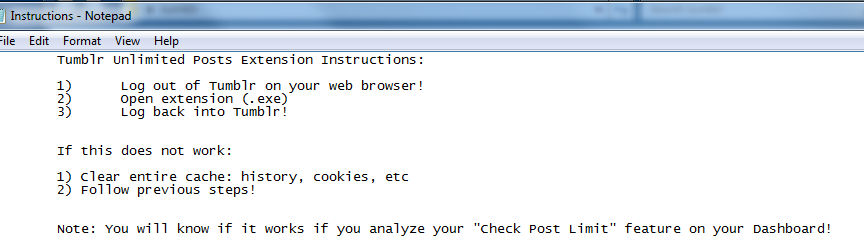
If you’re thinking “this sounds like a very specific attempt to harvest Tumblr logins on a compromised machine” you’d most certainly be right. Running the executable places
iexplorer
into the following folder:
[username]/AppData/Roaming
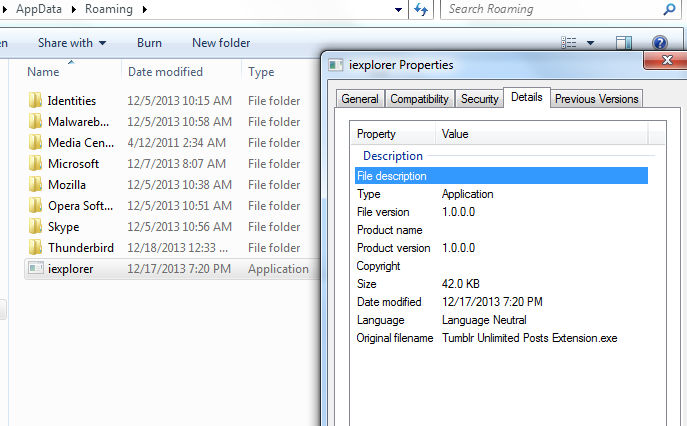
What could you possibly be doing in there, “Tumblr Unlimited Posts Extension. exe”?
The answer is, of course, attempting to keylog any Tumblr credentials entered into the computer after running the malware.
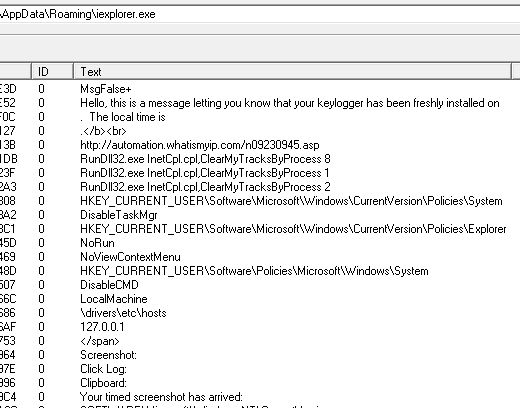
“Hello, this is a message letting you know that your keylogger has been freshly installed on…”
Notice also “Disable CMD” and “Disable TaskMgr”.
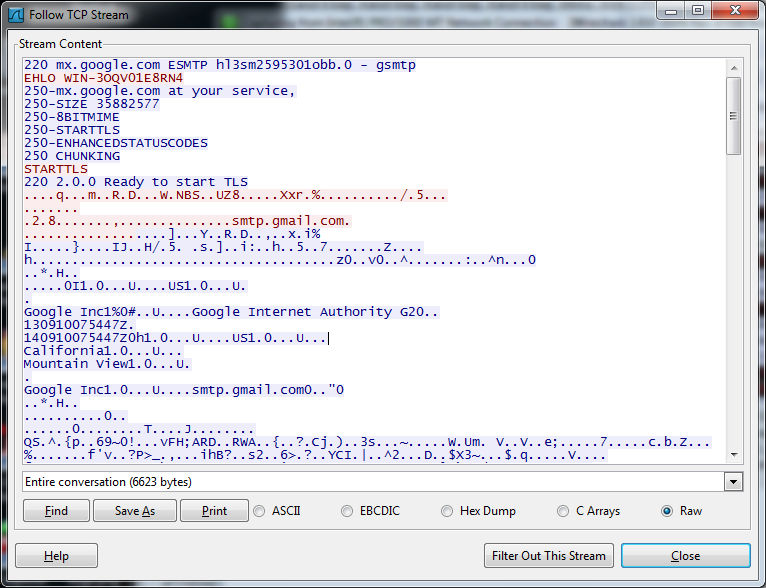
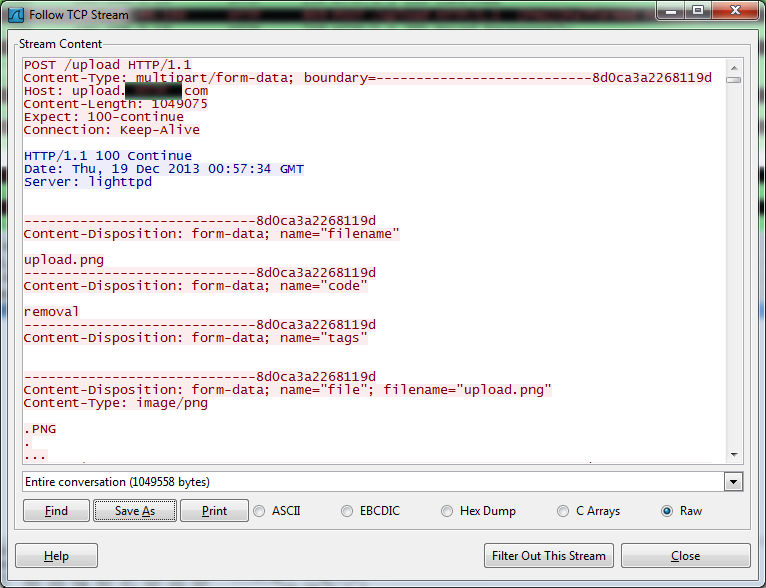
The infected machine will periodically try to send encrypted data back to the creator via email, and also upload random desktop screenshots to an image host. At this point, the harvested Tumblr credentials are likely the least of the increasingly large sack of “massive headaches” belonging to the victim.
Here’s some email traffic:
Here’s the attempt to upload a screenshot:
This is really rather nasty stuff. It seems whoever made this left lots of references in the strings to something called “Neptune”:
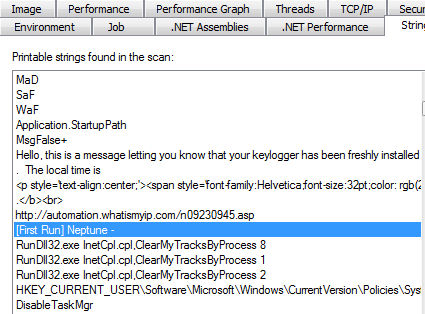
There’s Project Neptune, which is a “Windows OS monitoring tool” and subject of all the Youtube keylogging tutorials you can handle. Users of Malwarebytes Anti-Malware will find that we detect this as Trojan.Keylogger.MSIL, and the VirusTotal scores pegged at 28 / 49.
Tumblr users have been targeted by every kind of phish, scam, fake competition and free giraffe giveaway you could imagine but this one is particularly insidious – Tumblr logins are only the starting point, and it’s impossible to imagine what other forms of personal information could be harvested from unsuspecting users wanting their “more than 250 posts a day” fix.
“If it’s too good to be true, it probably is” might be one of the most overused sayings around but in this case it is most definitely one of the more sensible ones. Don’t be duped by claims of being able to get around Tumblr post limits or you could have more on your hands than a Tumble fumble.
Christopher Boyd (Thanks to Adam, Joshua and JP for additional research. Thanks to the Archive Poster team for the files).










