Recently, we discovered that a relatively popular “anti-malware” product known as “Yet Another Cleaner” or YAC for short, has been claiming to be an affiliate of Malwarebytes in addition to using a lot of our detection names as their own. We looked deeper into their operation and found some pretty amazing and ugly things.
The Good
“Yet Another Cleaner” is owned by Elex do Brasil Participações Ltda Technology Inc. They are located in Brazil and have a wide array of products including a speed test, alarm clock, IP lookup and of course, YAC.
YAC itself is a fairly sleek-looking program and very quick as well. It seems to have the ability to protect users from malicious web sites, cleanup junk files on their system, uninstall applications and even to block advertisements!
The Bad
The reality is while they might claim YAC can do all the things mentioned above, how the product actually performs is an open question. Anyway, we got a tip-off as to Elex do Brasil Participações Ltda Technology Inc. being an affiliate company to Malwarebytes, since they suggest an affiliation in their terms of use policy.

To be clear, Malwarebytes is in no way affiliated with Elex. Do you think Kaspersky, BitDefender, Avast, PCTools, iS3, Enigma Software, SUPERAntiSpyware and SurfRight are also affiliates?
So, after discovering that little bit of interesting information, we decided to look into the Anti-Malware software they were pushing.
The Ugly
We looked into YAC and noticed first off the similarities between their user interface and our own, and possibly even other security vendor tools.
Of course, this isn’t necessarily a bad thing, sometimes developers get inspired by other products, though it did prompt us to look deeper. We decided to check their detection names.
At this point we began to see more similarities, a bit more than normal. We scanned the same grouping of files between Malwarebytes Anti-Malware (MBAM) and YAC to see which popped and what names were used.
Off the bat, we knew that since YAC only detected a portion of the files that MBAM did that there were some significant differences. We decided to look at individual detections instead.
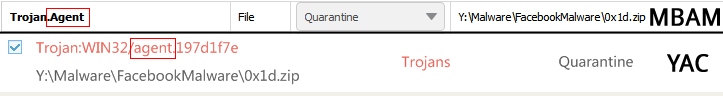
So the first one we spotted was the use of “Agent” as in “Trojan.Agent.” This isn’t a big deal because it’s a very common name to use in place of the actual malware name, for when you know the file is malicious but not sure the exact family it belongs to at that time.
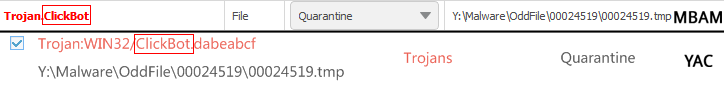
Next is “ClickBot” another name that isn’t used by everyone but it’s used by enough vendors to make it stand out a little more in our book.
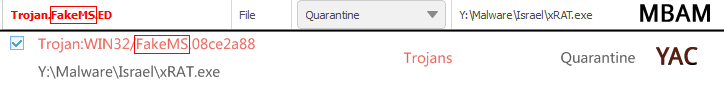
Finally, “FakeMS” was spotted and we got really suspicious. The term doesn’t belong to Malwarebytes but rarely does any other product use that designation other than Malwarebytes. Obviously, this isn’t any kind of conclusive proof as to theft going on but we had some ideas on how to look deeper.
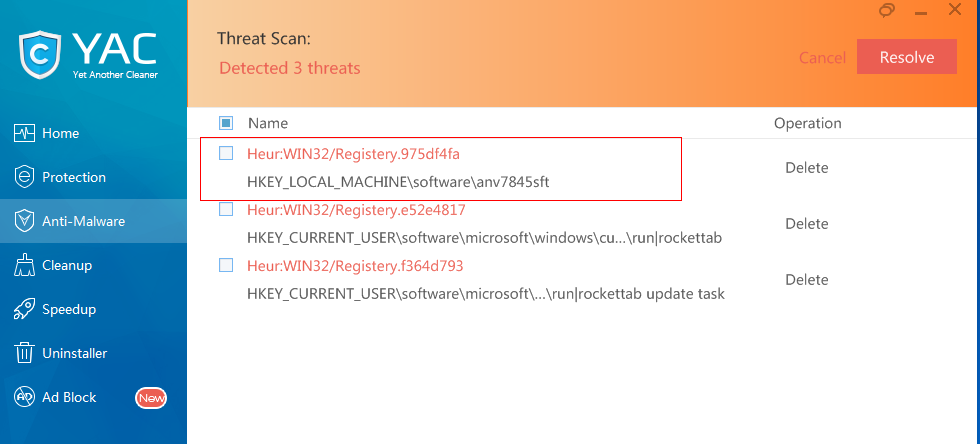
The first check was through a hidden detection method that we use to find applications who steal our definition database and use it as their own. We created a special registry key that is not affiliated with any process, malicious or otherwise and when it flags, we know our property has been stolen. The key is:
HKLMSoftwareANV7845SFT
NOTE: We have many other ways to identify our database in use by another product so rest assured we didn’t just give away our only way to do this.
We set up the trap key and ran a scan and found the special registry key.
To give these guys the benefit of the doubt, we will look deeper by creating a completely new fake malware detection. We built a custom program that does nothing more than show a message box. It looks like this:
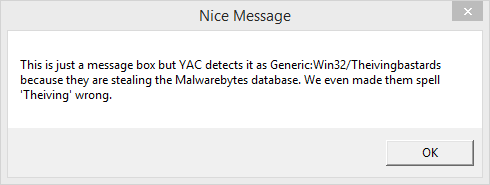
We then made a detection for this fake file, we named it something unique and even misspelled the words: “Spywera” & “Theiving.” You can check out the file for yourself, we uploaded it to VirusTotal.
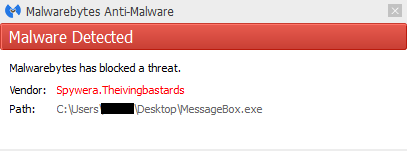
We pushed out this new detection as of 4 p.m. on March 1, 2015. About two hours later, YAC had an update available.
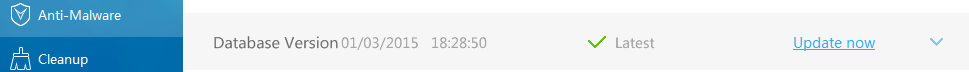
Using their latest definition database update, we ran a scan against our fake message box malware to discover that not only do they detect our fake malware but also use the same, unprofessional and misspelled detection name.
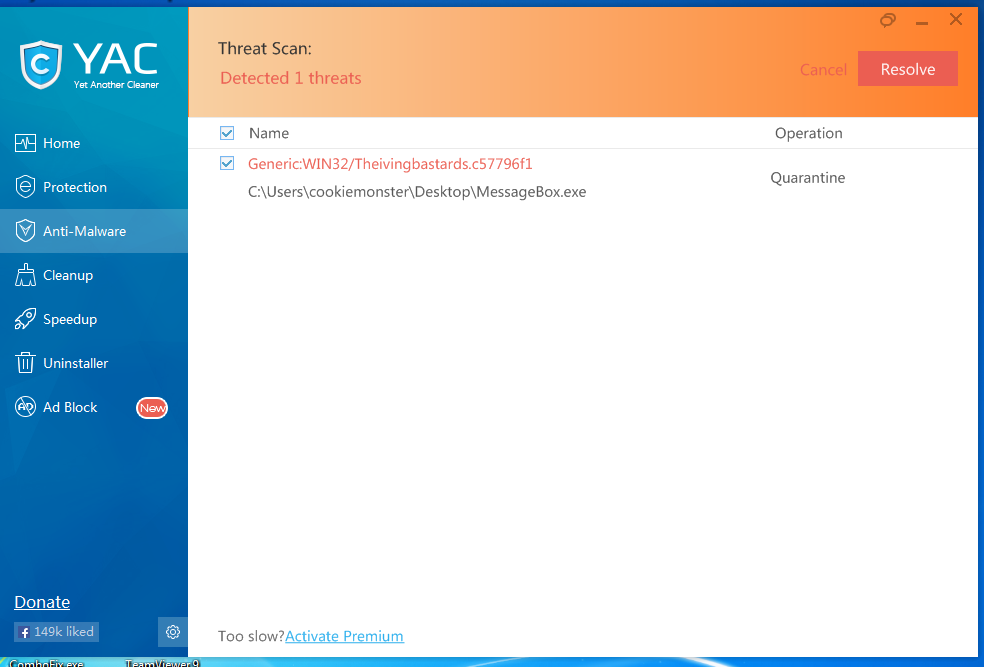
Alright, so it looks like Yet Another Cleaner is straight up stealing our detection database and modifying it for their own means. Based on the fact that they only detected a very small portion of the tons of malware we had both YAC and MBAM scan, their scanner apparently uses a slimmed down version of the one utilized by Malwarebytes Anti-Malware. We also know this because we actually analyzed a memory snapshot of their software in action. Tsk Tsk.
The reason this is such a big deal is because along with our engine, our interface, our brand name and our individual efforts, our definition database was created in-house and we already offer it for free to the world in the form of Malwarebytes Anti-Malware Free & Premium. It’s an insult not only to Malwarebytes but also to customers to steal the work of someone else and charge folks for a poor imitation of a product that is already free.
With proof in hand, we have sent Elex do Brasil Participações Ltda Technology Inc. a letter from our legal department to shut down their use of stolen property. We will keep you updated on any new developments.
UPDATE:
After this post went live, the technology certification company OPSWAT began investigating our claim against YAC for themselves and came to the same conclusion that we did.
OPSWAT provides certifications to security developers, assuring consumers that said products have been tested for interoperability and manageability with third party software, in layman’s that means they check to see if the application is going to break or crash your system because of not being compatible with other applications.
Today, OPSWAT posted a blog post that describes their interest in investigating our claims of YAC stealing our definition database and have decided, after their own investigation, to pull their certification from YAC.
After obtaining the data from Malwarebytes, and doing some internal analysis, our R&D team was able to validate Malwarebytes’ claim. Therefore, we’ve made a decision to remove the existing OPSWAT Certification for YAC from the program. Yet Another Cleaner 4.x will no longer be Bronze Certified under Windows Antispyware.
They have also asked Elex do Brasil Participações Ltda Technology Inc. to discontinue their use of the OPSWAT certification badge on their website and products. In addition:
We have discontinued our partnership with Elex Technologies and plan to continue our policy going forward that such business practices will not be tolerated.
Nice job OPSWAT! Thanks for the faith!
Thanks for reading!
![[UPDATED] Yet Another Cleaner, Yet Another Stealer](https://www.malwarebytes.com/wp-content/uploads/sites/2/2015/03/photodune-3595462-identity-theft-l.jpg?w=1240)









