We recently saw a .gov.vn URL which was redirecting to a phishing expedition for Apple IDs. First up, let’s take a look at the email which sported a particularly French flavour:
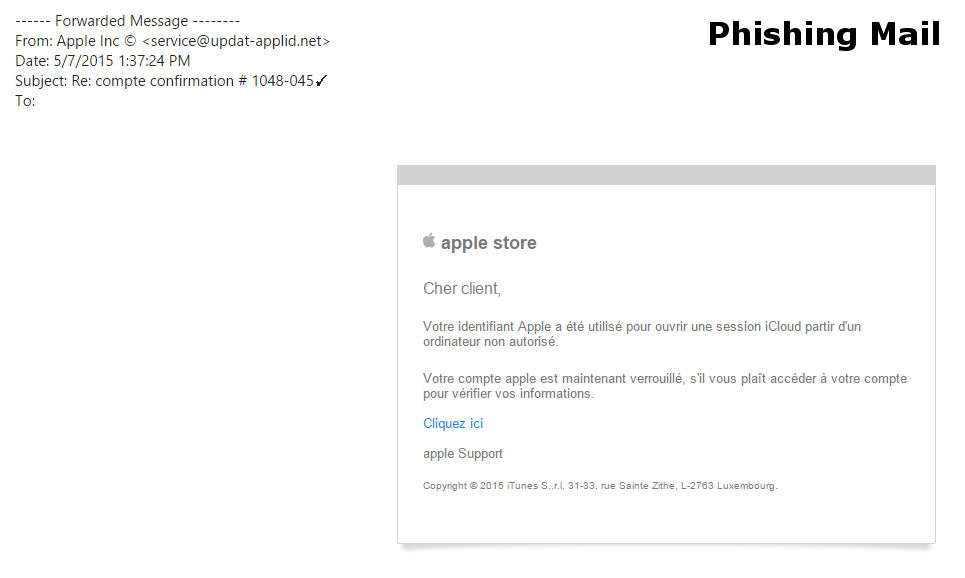
It reads as follows:
Dear Customer, Your Apple ID was used to log into iCloud from an unauthorized computer. Your account is now locked, please log into your account to check your information.Click here Apple Support
The link leads to
anphutamky(dot)gov(dot)vn/cu/install/css/
which contained little other than code to redirect the visitor:
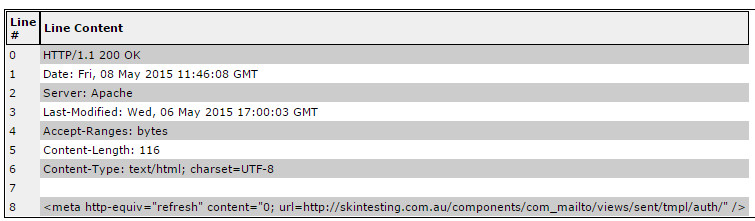
The potential victim was sent to
skintesting(dot)com(dot)au/components/com_mailto/views/sent/tmpl/auth/
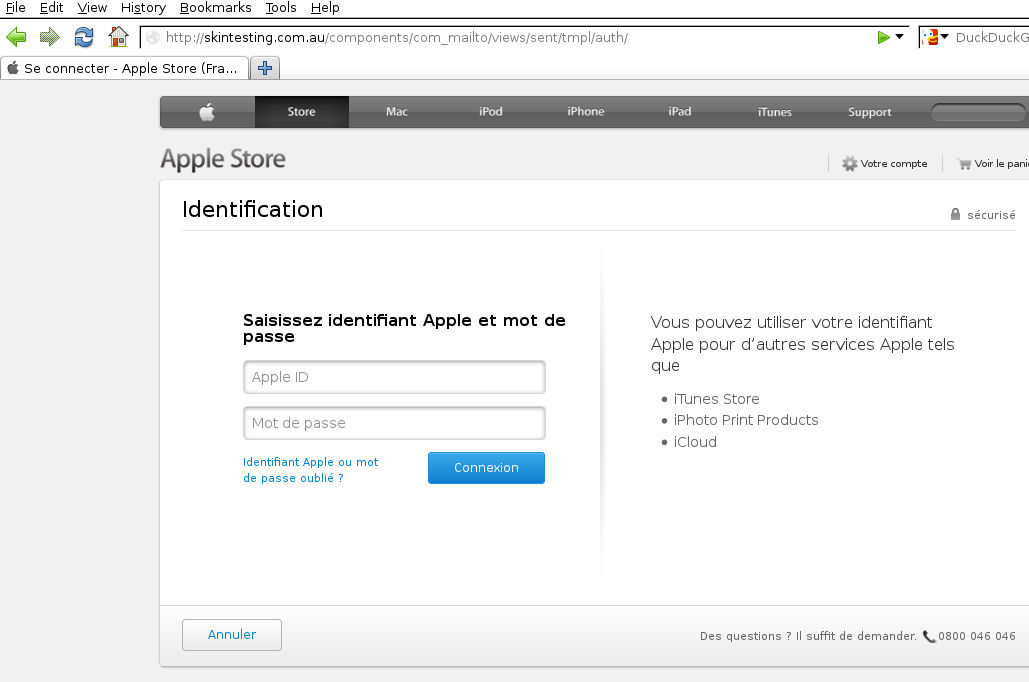
which looked like yet another compromised domain, asking for Apple login credentials.
Both rogue pages have now been taken offline. A .gov site is always going to be a juicy target for scammers so it’s crucial Admins keep everything patched and up to date – tracking back to where and how an attacker got in can be a long, arduous process. As for Apple ID owners, always verify you’re on the correct page before entering login details. Unless you specifically asked Apple to send you a link for some reason (a password reset, for example) then you should avoid random URLs sent your way. Here’s some Apple ID security information which will likely assist with keeping your account secure.
Christopher Boyd (Thanks to Cecile for sending over)










