These days, it is becoming harder and harder to browse the web without encountering one of these pestering pop-ups claiming your computer is infected.
In fact, they affect every device and every platform without distinction and fuel a multi-million dollar industry of tech support scams.
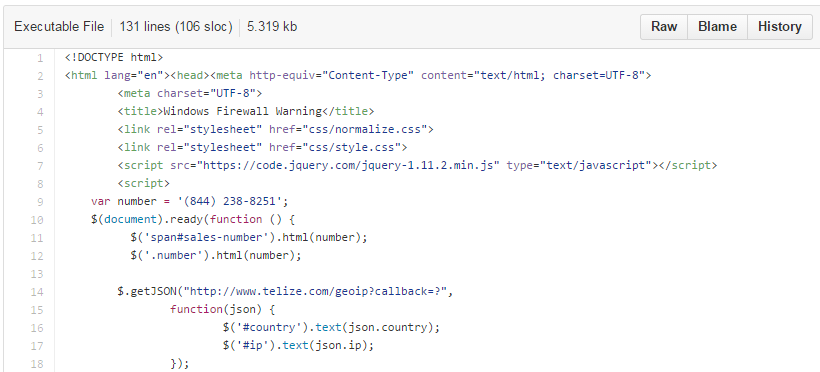
Often times, the design is made by the same people running the scam, and for the most part the coding is pretty bad. They are basic html files with a few lines of JavaScript that get the job done, but that’s about it.
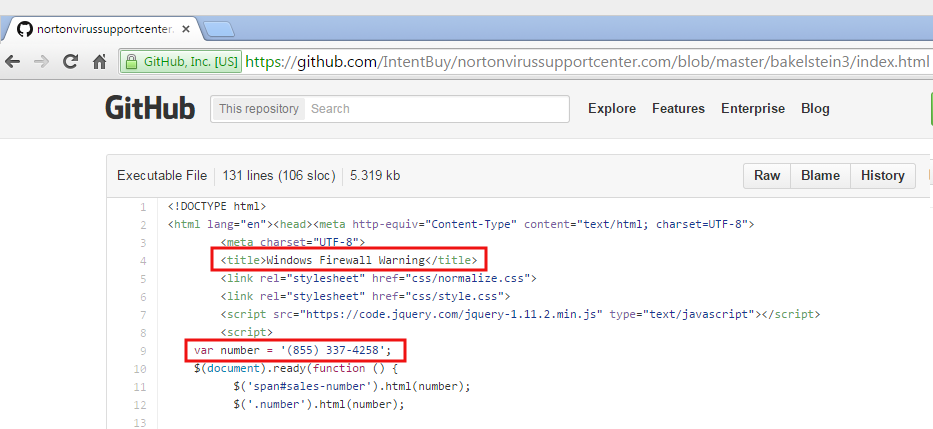
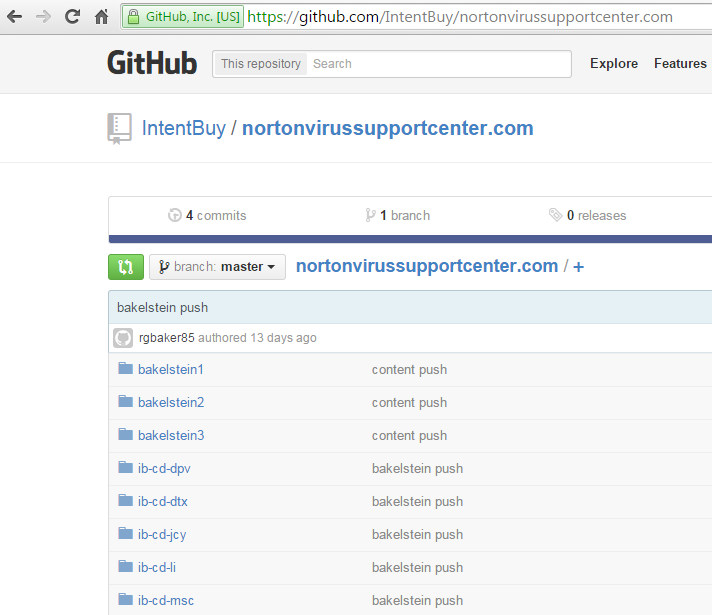
Today we are looking at a more professional approach where someone used GitHub, a web based platform for revision control and source code management, to house and work on their fake pop ups code.
Of course, this was not supposed to be publicly seen but a lack of care made it fairly easy to identify when investigating the pop ups pictured above.
Each directory has a variant of the fake pop ups for different campaigns or countries. Overall, the code is well organized and documented.
This was not a job done in a hurry, but rather someone with coding experience which was hired to build these templates and provide them to various affiliates or marketing firms.
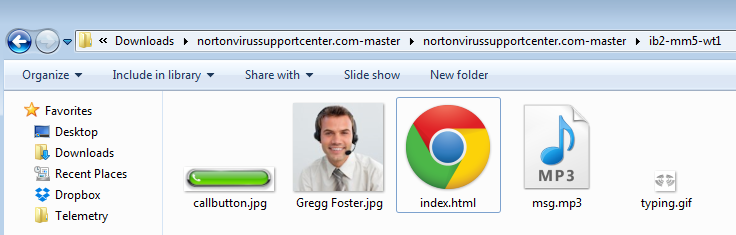
Beyond the standard html files, there are also images and audio files corresponding to the different scam pages.
How did we get there?
To better understand why this is happening we need to look at the evolution of tech support scams. The market was once dominated by companies with large boiler rooms in India, where hundreds of ‘agents’ randomly cold call people.
Pretending to work for Microsoft, the agents would trick people into purchasing computer support for several hundred dollars and would never actually deliver anything. Paid very little, these young people who often were looking for their first job, allowed a few select owners to be extremely wealthy by perpetrating these scams.
Fast forward a few years and you see the explosion of unwanted pop ups with visual and audio warnings urging you to call for assistance.
Sadly, scammers aren’t just in one specific area. It didn’t take long for US companies to jump in on the bandwagon, realizing they could make money hand over fist.
With that came a greater sophistication in the scams and a better structure to pull in more and more victims each day.
There are really two sides to the business:
- Marketing and web traffic (lead generation)
- Remote assistance and conversion (sales)
The first one is about driving leads to specific companies by leveraging affiliate marketers and scamvertising (the term malvertising could be used but these misleading ads do not generally infect computers).
In some cases the tech support businesses are also the same actors that create the fake pop ups. In other cases, they simply externalize this task and pay commissions for leads.
Scamvertising consists of tricking the user with fear or scare tactics and have them commit an action. In this context, it consists of calling a toll free number for computer assistance.
This leads us to the remote assistance part, which is handled by “tech support” companies. This is where the actual exchange of money takes place. A “computer expert” lies to innocent people and forces their hand to pay hundreds of dollars to get rid of non existent issues.
Tech supports scams are like the plague, claiming more and more victims each day. The fact that fraudsters are getting more sophisticated and still get away clean from their crime is a worrying trend.
If you would like to spread the word or need assistance, please check out the resource page we have on our blog. Better awareness as well as going after the offenders is the best solution we have to combat this problem.