Last week I wrote a blog post on the dangers of ads posing as fake download buttons on various download web sites. Since then I received a lot of feedback from our readers and other security researchers on different tools available to help users avoid these dangers by blocking the ads entirely. Instead of adding to an already lengthy blog post, I decided to write a sequel post that gives step-by-step instructions on how to install what I have found to be 3 of the best ad blocker applications available to you for free.
The Baseline
As with any comparison and effectiveness study, we need to establish a baseline to work from. In this case, I decided to use a case from last week concerning numerous fake download ads covering the actual download page.
From this point on, all ad blocking applications I discuss will be tested against this page to see whether or not it does the job.
AdBlock for Chrome
The first ad blocker I will discuss is “AdBlock”; it was developed for the Google Chrome browser and has been heralded as the “Most Popular Chrome Extension.” A guy named Michael developed it and he works on the development of the extension full-time. So let us get started with the installation:
- In Chrome, navigate to the very right of the Address bar and click on the button with three horizontal lines, it will bring down the Menu for the browser. From there, click on the “Extensions” option located within the “Tools” sub-menu.
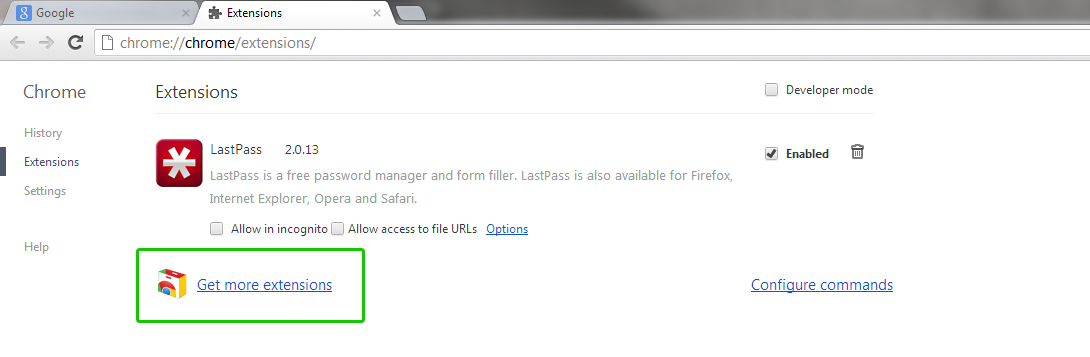
- A new browser tab will pop up which shows all of your currently installed extensions. Click on the “Get More Extensions” option, highlighted in the green box in the screenshot below.
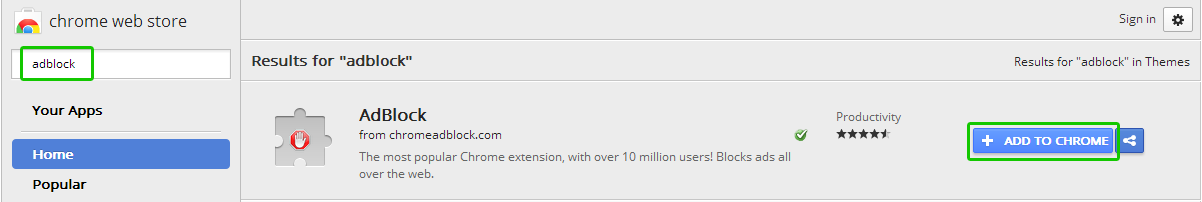
- A tab for the “Chrome Web Store” will pop up. Use the search bar on the left side of the page and type in “AdBlock” into the text box to search for the extension. Once you are presented with the different available options, identify the correct extension for “AdBlock” and click the “+Add To Chrome” button to the right.
- Chrome will ask you to confirm the installation of the new extension, click the “Add” button to start the installation.
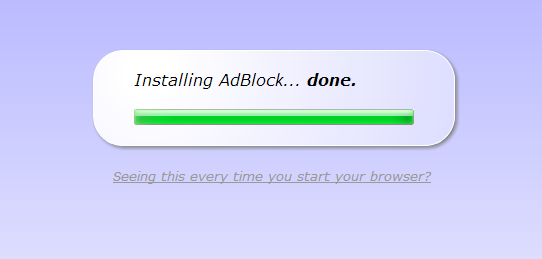
- If everything is going good, you should see a screen like the one below.
- Once installed, you should see a little stop sign with a hand on it next to the menu button to the right of the address bar. Congratulations! You just installed an ad blocker extension!
When you finish installing the extension, a page will pop up telling you a little bit about Michael and his wife and asks to “Pay what you can” for the extension. I always like to support great software which is given out free and so I encourage you (if you can) to donate something to Michael to continue working on this great tool.
As far as our test goes to see how it fares against our baseline web page, here is what the same page looks like using the AdBlock extension:
Adblocker Plus for Firefox
Next up is an ad blocker extension for Firefox that recieved rave reviews from various security experts and average users. AdBlock Plus is just as easy to install as AdBlock for Chrome and takes donations to help fund the continuing advancements made to this tool. It is a community driven open-source project and been translated into 30 languages. This is how you install it:
- In Firefox, navigate to the “Tools” menu at the top of the screen, from there select the “Add-ons” option as seen in the screenshot below.
- Next, use the search bar in the upper right part of the screen and search for “AdBlock” to return results revealing the AdBlock Plus add-on. To install, click the “Install” button to the right.
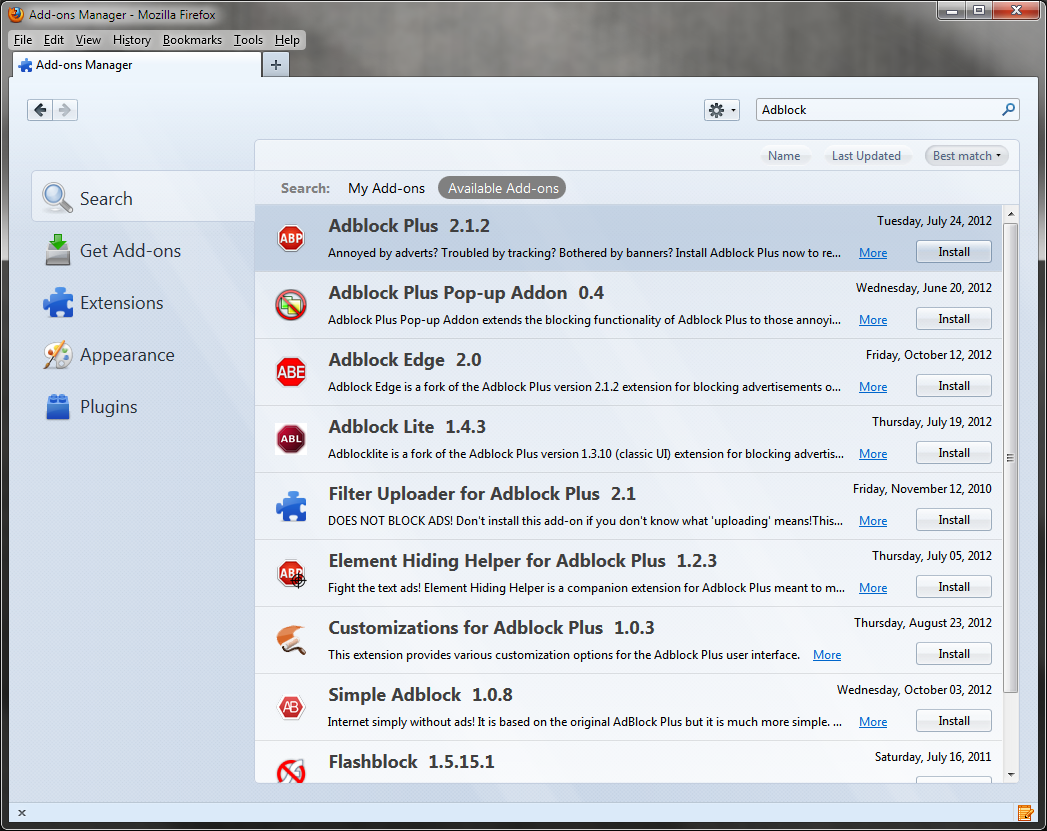
- To ensure the add-on is correctly installed, click the Extensions tab to the left of the screen and make sure that “AdBlock Plus” is listed as one of the installed extensions.

- Once installed, you should see a little ABP stop sign icon in the lower left corner of your browser window, this not only designates that the extension is running but also allows a quick menu interface for the tool.
- Finally, we can check our baseline case and see that AdBlock Plus gives us the same result as the AdBlock Chrome extension did.
HostsMan for everything
The final tool I will be discussing is different from the other two and for multiple reasons. HostsMan…
- …blocks DNS traffic, meaning it uses your systems HOSTS file to redirect any known malicious or ad-hosting domains.
- …updates your hosts file with constantly updated lists from sources like HpHosts.
- … allows you to choose which lists you want to use.
- …works outside of the browser and supports every application on your system that attempts to connect to a blacklisted domain.
HostsMan is more for advanced users who want to avoid any application reaching a blacklisted domain. It accomplishes this by modifying your HOSTS file on your system, which means that the blocking of malicious or ad related traffic originates from your system, protecting you even if your DNS configuration has been altered on your router or external routing server. Here is how you install it:
- Download the current release of this tool here: HostsMan
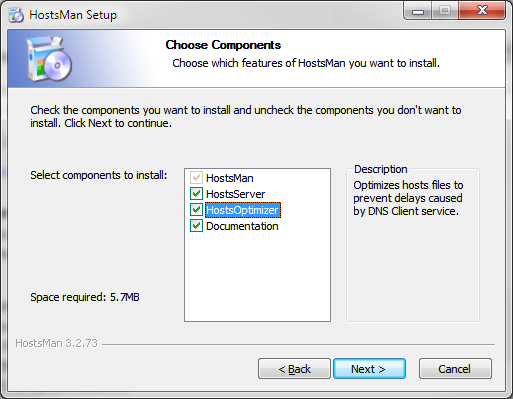
- Once you have unzipped the file, execute it to start the installation process; you should see something like the screenshot below.
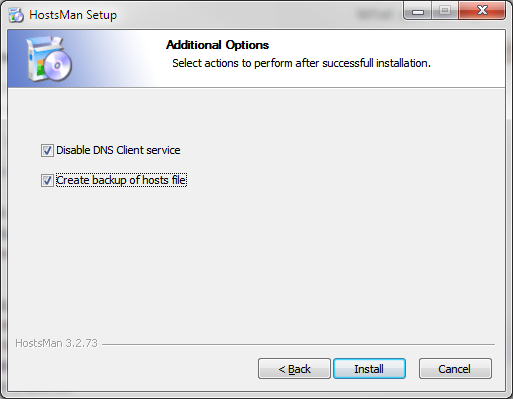
- During the installation you will be presented with a list of components you might want to install, I recommend installing all of the components by checking all the boxes.
- Before the installation application begins copying files, make sure to select “Disable DNS Client Service” and “Create Backup of Hosts File” just to be sure that the program will work correctly and you will not lose any custom HOSTS configuration.
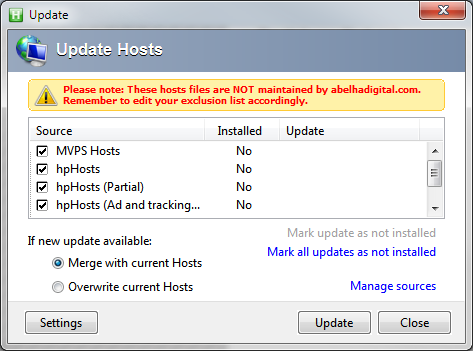
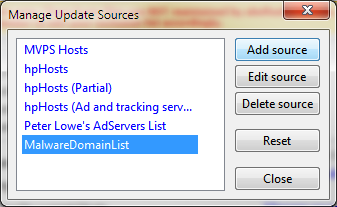
- After installation is complete and you have started HostsMan, you need to configure the blacklist sources before it is going to work correctly, to do this click on the center icon on the interface, it will open up the Update Hosts window.
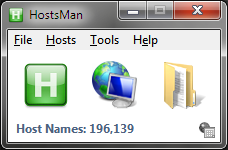
- In this window, you can select any of the pre-defined update host sources and add your own, I recommend selecting all of the ones it suggests, then adding a new one by clicking on the “Manage Sources” link.
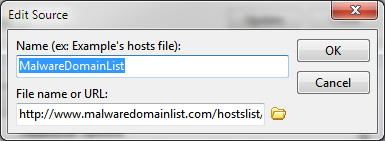
- Once the Manage Update Sources window comes up, Click “Add Source”
- Malware Domain List is a reputable malware domain-tracking site that provides up-to-date blacklists to help protect your system from drive-by malware. To add this source, use the name “Malware Domain List” and insert the following URL:
- http://www.malwaredomainlist.com/hostslist/hosts.txt
- Once you click Ok -> Close -> Update you will be all set up, if you are having issues with it, try restarting your browser or your system.
- Using HostsMan we are able to test our baseline case and see if the Ads are blocked or not, the screenshot below shows the results.
As you can see, one Ad is not entirely removed as with the browser extension ad blockers but it is nonetheless not loading and therefore you are safe. The benefits of using HostsMan over AdBlock or AdBlock Plus is that the blacklisted domains which HostsMan prevents you from visiting, also prevents you from accidentally being infected with malware from known exploit sites, the other applications only block ads.
Conclusion
My previous blogs have mentioned more than just ads being used as fake download buttons, but are also used to spread malware when malicious ads are injected into the queue for an ad server. By using an ad blocking application like the ones listed above, you protect yourself from these threats as well as free yourself from the tyranny of constant ads resulting in a much better browsing experience. If you have any questions about any of these tools and their use or installation, please either comment, post on the Malwarebytes Forums or contact the developers of the tools.
Adam Kujawa is a computer scientist with over eight years’ experience in reverse engineering and malware analysis. He has worked at a number of United States federal and defense agencies, helping these organizations reverse engineer malware and develop defense and mitigation techniques. Adam has also previously taught malware analysis and reverse engineering to personnel in both the government and private sectors. He is currently the Malware Intelligence Lead for the Malwarebytes Corporation. Follow him on Twitter @Kujman5000