During the past few weeks, malvertising activity was a little bit on the decline, at least within our own telemetry. We were mainly seeing the usual suspects pushing a lot of Magnitude EK related infections and the occasional tech support scam.
However, out of the blue on the weekend we witnessed a huge spike in malicious activity emanating out of two suspicious domains. Not only were there a lot of events, but they also included some very high profile publishers, which is something we haven’t seen in a while:
| Publisher | Traffic (monthly)* |
| msn.com | 1.3B |
| nytimes.com | 313.1M |
| bbc.com | 290.6M |
| aol.com | 218.6M |
| my.xfinity.com | 102.8M |
| nfl.com | 60.7M |
| realtor.com | 51.1M |
| theweathernetwork.com | 43M |
| thehill.com | 31.4M |
| newsweek.com | 9.9M |
* Numbers pulled from SimilarWeb.com.
Rogue domains:
Domain Name: TRACKMYTRAFFIC.BIZ Creation Date: 2016-02-27 Sponsoring Registrar: PDR Ltd. d/b/a PublicDomainRegistry.com Registrant Organization: PrivacyProtect.org IP address: 104.28.18.116 (CloudFlare)
Domain Name: TALK915.PW Creation Date: 2016-02-25 Sponsoring Registrar: PDR Ltd. d/b/a PublicDomainRegistry.com Registrant Name: Rocko Mantas Registrant Organization: Best Media ltd IP address: 104.27.190.84 (CloudFlare)
Ad networks/platforms:
Google:
- www.trackmytraffic.biz/imp_track?zone=975
- talk915.pw/track/k.track?wd=48&fid=2&rds=b1714032cd63652bc95fadf5dc81dadd88cafec4&aff=0.470974263806 -> Referer: http://tpc.googlesyndication.com/safeframe/1-0-2/html/container.html
AppNexus
:
- www.trackmytraffic.biz/tracker?zone=145&camp=Tapika
- talk915.pw/track/k.track?wd=48&fid=2&rds=b1714032cd63652bc95fadf5dc81dadd88cafec4&aff=0.0458697036987 -> Referer: http://lax1.ib.adnxs.com/{redacted}&referrer=http%3A%2F%2Fwww.nytimes.com{redacted}
:
- www.trackmytraffic.biz/imp_track?zone=6899&camp=Vemeo
- talk915.pw/track/k.track?wd=48&fid=2&rds=b1714032cd63652bc95fadf5dc81dadd88cafec4&aff=0.22486335239 -> Referer: http://www.aol.com/_uac/adpage.html
:
- www.trackmytraffic.biz/imp_track?zone=6899&camp=Vemeo
- talk915.pw/track/k.track?wd=48&fid=2&rds=b1714032cd63652bc95fadf5dc81dadd88cafec4&aff=0.515004501486 -> Referer: http://optimized-by.rubiconproject.com/a/11648/36322/150620-15.html?&cb=0.49251904142839664&tk_st=1&rf=http%3A//my.xfinity.com{redacted}
Payload:
The first couple of days before this campaign went big, we observed a few hits on smaller publishers that were pushing the RIG exploit kit:
fg.lazarus-designs.com/?xXmNd7GZKxbIA4A=l3SKfPrfJxzFGMSUb-nJDa9BMEXCRQLPh4SGhKrXCJ-ofSih17OIFxzsmTu2KV_OpqxveN0SZFSOzQfZPVQlyZAdChoB_Oqki0vHjUnH1cmQ9laHYghP7cfAEOBo3lukyLNHeJ5yw0SH6jcGmr8dV1xC5VkRlPjPBKqE -> Referer: http://www.quoka.de/tiermarkt/fische-aquaristik/c5120a160897102p105457703/aussenfilter-tetra-ex600.html
On Sunday, when the attack really expanded, the Angler exploit kit was then used:
noblitt.petalsandpaintdrops.com/topic/80972-degrease-arranging-micturition-stupidly-toast-visible-roadworthy-monotonicity/ -> Referer: http://lax1.ib.adnxs.com/{redacted}&referrer=http%3A%2F%2Fwww.nytimes.com%2F2016%2F03%2F13%2Fus%2Fpolitics%2Fdonald-trump-campaign.html%3Femc%3Dedit_th_20160313%26nl%3Dtodaysheadlines%26nlid%3D69859133%26_r%3D0Angler EK has gone through several changes lately, in its URI patterns but also in the landing page itself. It is also the only one to use a recently patched Silverlight vulnerability.
Malwarebytes Anti-Exploit blocks the malvertising attack when it launches the exploit kit:
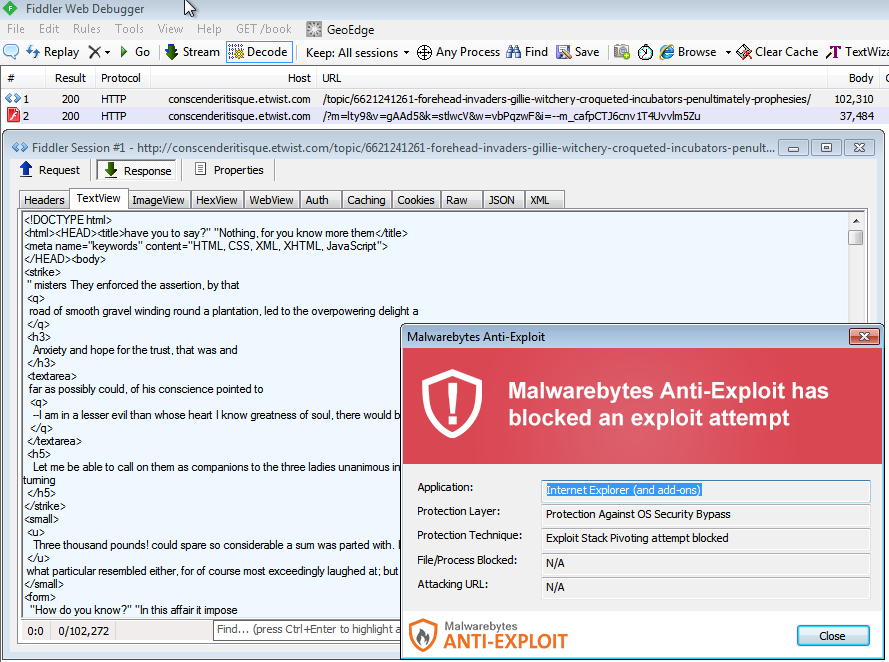
We notified the various ad networks when we first identified the attack as well as CloudFlare; we will update this blog with any new relevant information.










