Most of us have moved to mobile computing and use it daily, but we often take security for granted. After all, a cellphone is just a telephone right?
Nope. They’ve become very powerful machines, and with their functionality in the wrong hands, they can be destructive for us.
Since computer software has been around, people have been finding ways to attack it by through vulnerabilities or targeting users. And the Android mobile operating system is no different. Its success in the consumer space—and its openness—has made it a huge target for malware authors.

Let’s take a look vulnerabilities malware authors take advantage of and their favorite ways to attack.
Social Engineering
In today’s world, staying “connected” is a must and that means staying connected to the Internet and connected to work, friends, and family through text, email and social networking resources.
Our need for social interaction makes us easy targets for those who want to exploit us.
Social engineering is the top attack vector for malware authors in the mobile space and will likely stay at the top in the foreseeable future.
What You Should Be Aware of:
Fake and Infected Apps: A majority of malicious mobile apps are fake or rogue apps that claim to have some function but will also contain malicious behaviors that run without users’ knowledge. These apps can contain trojan, spying, bot and other malicious functionality. By tricking us into running their fake apps, cybercriminals can sit back and reap the financial rewards of their SMS Trojan or click bot. These apps can be found in many different locations such as the Google Play Store, 3rd Party Markets, and P2P sites.
SMS Phishing (Smishing): Phishing is big business, and the phishers have taken to text messaging to get in touch with us. Our phone numbers can fall into the wrong hands in numerous ways—like vendors selling it or a compromised contact. When your number is compromised, you can see incoming messages indicating you’ve won some contest, banking credential requests, or software updates. The sender’s number could be from a known contact or some number claiming to be from a legitimate source.
Drive-bye, QR Code, and URL Redirection: Another way to deliver malicious apps is through URLs or compromised websites. When your device’s browser is redirected to one of these URLs an app payload will be waiting on the other end. The malware payload can be anything from a trojan to spyware. Fortunately, the apps can’t easily be installed—provided you haven’t rooted or jailbroken your device.
Unknown Sources
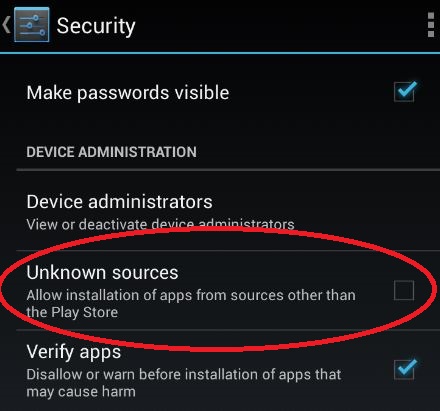
Android has a setting in place that will keep most users safe from installing malicious apps. It’s disabled by default and prevents non-Play Store apps from being installed. The setting is called “Unknown sources” and can be found in Settings -> Security.
Leaving it disabled can stop inadvertent apps from installing. For some, the allure of Android is the ability to “sideload” or install from alternative locations, and having this enabled won’t always work. Just disable this setting once you’ve installed your apps.
Reputable Markets
Sticking to Google’s Play Store is a great way to ensure you’re downloading trustworthy apps. The Play Store has been dinged a few times for hosting malware, but for the most part it is secure. The malware found isn’t highly visible and in popular apps; it’s buried deep in the thousands of apps we rarely see.
Google has also taken steps to prevent malware from getting to the Play Store. With the implementation of Bouncer, its malware analysis back end, and the acquisition of VirusTotal, I’m sure Google has stopped a lot more than has gotten in.
Amazon has an app store with a large selection of apps, and to my knowledge, no malware has been discovered hosted there—some less than reputable yes, but not out and out malware. There are many others out there. Just keep in mind that these alternative markets require you to enable the unknown sources’ setting.
Research Apps/Markets
In most cases, you will get an idea of an app or market’s reputation by doing a little research and reading reviews.
The Google Play Store is the best place to get apps with the most selection; customers have the ability to leave reviews of apps. Many customers take the time to leave a review; they’ll leave feedback as to whether an app is worthwhile or even suspected of being malware.
Other app stores also offer a way to review apps. For third party markets, you can find reviews and other information through Internet searches. Oftentimes, you’ll see questions where people are wondering the same thing about a site. Another thing you’ll find is that many bloggers or journalists will write about their favorite—or the top—app stores.
Permissions
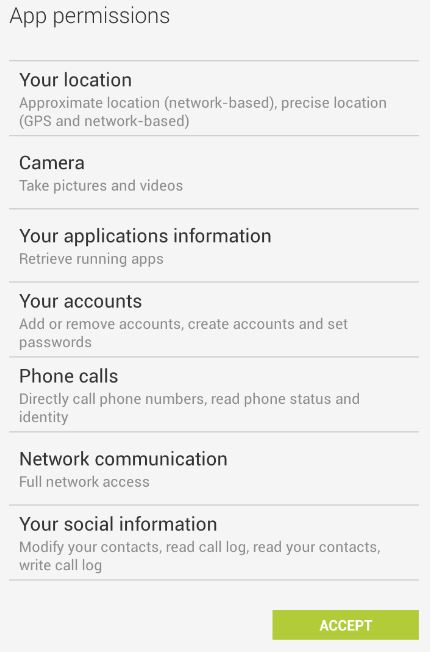
Reviewing the permission requests of an app is a good habit to have.
These permissions give insight into the functionality the app is wanting access to. In some cases, it makes sense to see something like a media player app requesting access to Telephone or wallpaper requesting SMS functionality. In these scenarios, the media player uses the telephone access to pause music for an incoming call, and the wallpaper app has functionality to share the app with friends via SMS.
So, take a minute to decide, and go with your gut. Typically, there is more than one choice for some apps. Take a look at highest rated or featured apps first.
One thing that is frustrating about Android’s permission model is that it’s all or nothing. You can’t be selective with the permission an app uses. Some encouraging news has come from Google I/O 2013 on this topic. Google is finally starting to listen and “thinking” of ways to handle this.
Lost device
Aside from malicious apps and websites to avoid, the other security concern is with lost or stolen mobile devices.
As a first layer of protection, you can utilize a lock screen like a PIN or password, Settings -> Security -> Screen Lock.
Sometimes we just misplace our device or forget it at the coffee shop, and for this reason, lost device protection is great. These apps will help locate your device using GPS. For this to work, you’ll have to look to a third party app as this functionality isn’t embedded.
There are some pretty good ones like “Where’s my Droid” and ”Android Lost.” These apps also offer other protections like remote wipe. Some of these devices are small and easily misplaced or too large for our pockets. Having some added protection will help with your piece of mind.
Conclusion
As we move further into a mobile world, we need to be aware that the bad guys are looking to exploit our weaknesses and continually target our personal data and money.
We can protect ourselves by being aware of how we’re vulnerable and also that these devices aren’t just telephones but computers that contain access to our lives. Stay secure out there, review apps you install and enjoy the mobile future.









