Update (Feb 25):
More info on the update can be found here.
Original story:
Releasing a software update right before the weekend is something that software vendors tend to stay away from because of its inherent risks. And yet this is precisely what Apple did last Friday when they pushed a security update which immediately prompted many people to dissect it.

The flaw (CVE-2014-1266) affects certain versions of iOS (iPod, iPad and iPhone) and OS X (laptop / desktop).
In layman’s terms, if you are connected to a public WiFi, an attacker could eavesdrop on all your HTTPS encrypted traffic by creating a fake digital certificate.
Normally, a fake digital certificate would throw a warning such as this:
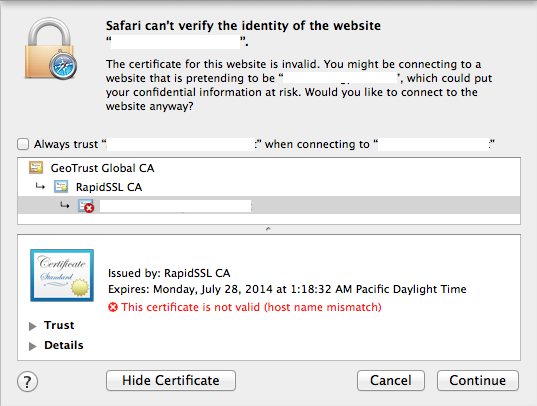
The problem lies with failing to check a digital certificate in what has been called the “gotofail“. This bug is very serious because that validation check no longer happens:
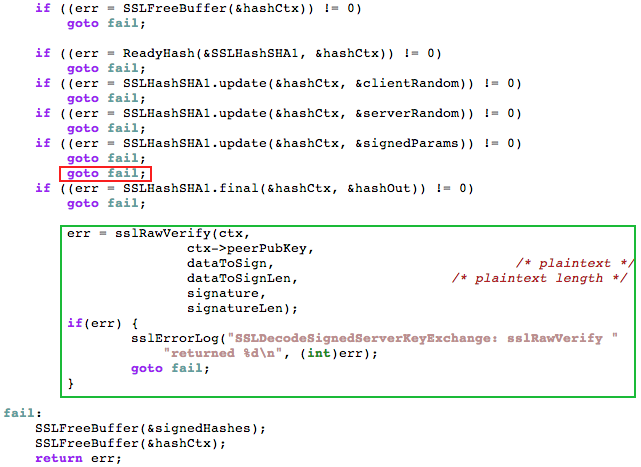
For some yet undetermined (but yet very controversial) reason, a redundant “goto fail;” (in red) statement was inserted in the code bypassing a critical check (in green).
As such, the user would no longer see any error and could potentially be connected through a rogue certificate, allowing the attacker to play man-in-the-middle and intercept/inject data.
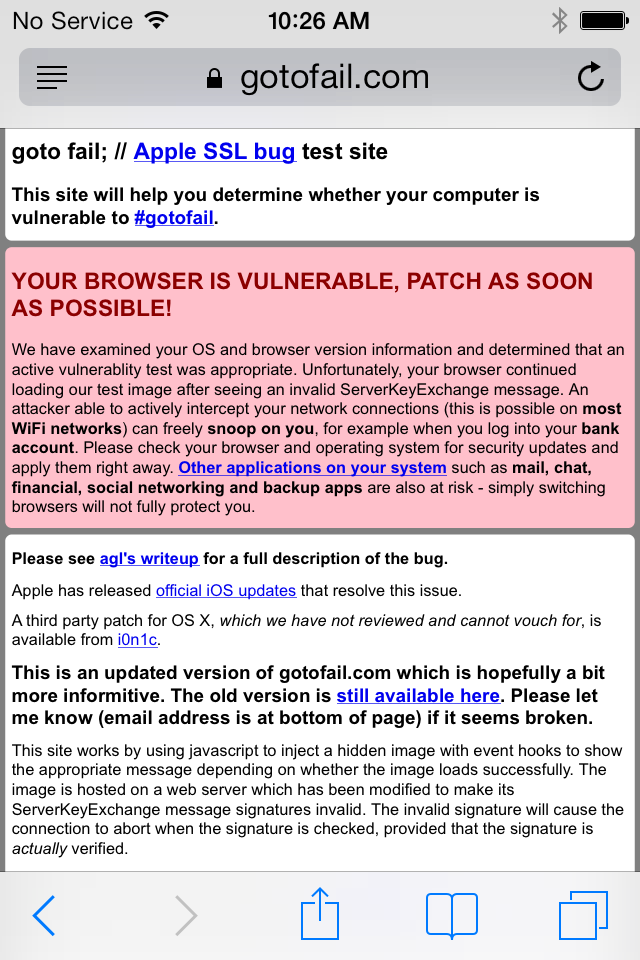
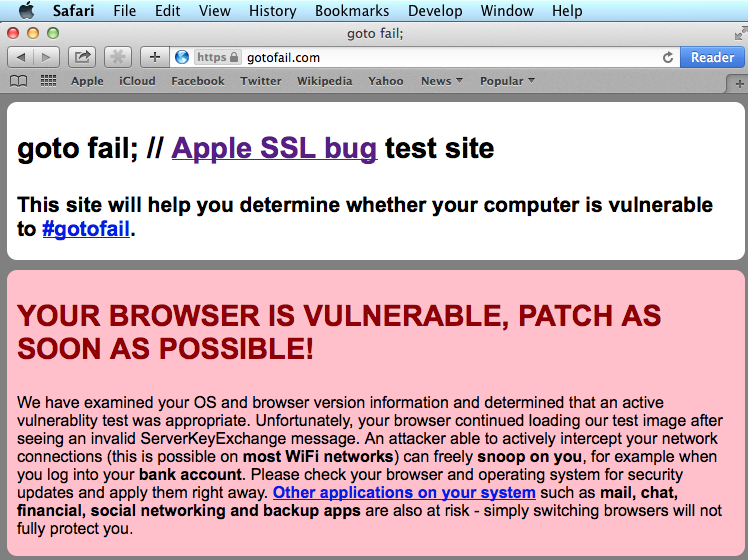
You can check if your Apple device is vulnerable to this bug by visiting gotofail.com:
Apple provided a fix for iOS which you can download from Settings> General > Software Update but has yet to release one for OS X. While waiting for an official patch, you should not connect to any public WiFi without at least:
- using a VPN to encrypt your communications within the access point
- using an alternate browser (Chrome or Firefox) not affected by this bug
Please note that other programs such as Mail, iMessage, Facetime are affected and should not be used on insecure networks.
Update: Security researcher ashk4n highlighted that even with VPN the risk may still exist unless you use a different protocol such as OpenSSL.










