Here’s a scenario:
Suppose you went live on Twitch to stream your playthrough of Destiny.
Suppose you were getting a lot of eyeballs to your live stream. Say a couple of hundred, and you just started another bounty.
Suppose while you were playing, you noticed in your channel’s chat that some of your viewers were talking about another channel, which is also streaming Destiny at the moment. These conversations then led to a massive exodus of viewers from your channel to that other channel, leaving you with an awful lot less.
What happened is what they call Twitch bombing, which is also known as Twitch raiding.
It can be facilitated by a bot or an individual with a huge following; however, it’s usually the former.
The above scenario is just one form of bombing that, although uncommon, might be familiar to some of us.
The act of bombing or raiding on Twitch is not something unheard of or unnatural within the video game streaming environment. In fact, it has been going on since 2012.
Twitch forbids this, as per their ToS; however, how users view stream bombs/raids is a mixed bag: On one hand, some favour it because they say it helps the low-ranked streamers to raise their popularity and improve viewer experience.
On the other hand, some frown upon it because it hurts both the streamers and watchers because (a) view count is diminished from a legitimate streamers, (b) viewers may be misled to a gaming channel they may not be particularly interested in, and (c) those wanting to increase their view count using bots artificially inflates their stats and endangering their account from getting shut down.
Whichever side you’re on, proponents of malware and potentially unwanted programs (PUP) have you in their crosshairs.
Malwarebytes found a couple of samples file—one a Trojan and the other a PUP—claiming to be Twitch bots that we’re going to look into here.
Sample 1: Trojan.Crypt
We have obtained the first file from twitchbomber(dot)pw, which is currently offline.
Trojan.Crypt is malware known to modify the affected system’s browser start page. Upon execution, it drops a file named twxLTeqhUg.dll, which Malwarebytes also detect as Trojan.Crypt. It then retrieves or collects information about the affected system such as the Windows Product ID, MachineGuid, DigitalProductID, and SystemBiosDate, potentially to fingerprint sandboxes or test machines.
It also drops non-malicious component files onto the Windows system directory, injects code into processes. This particular Crypt variant keeps itself hidden onto affected machines and stops Process Explorer and Task Manager from launching in an attempt to deter users from terminating it. To prevent other instances of itself from running onto already affected machines, it creates several mutexes.
File name: MediaManager.exe (111,452 bytes) SHA256: ff4a9abcecc80582778a2476fee3649312504dc2fa5721bba3a7abfe416bb7f2 Malwarebytes detection: Trojan.Crypt
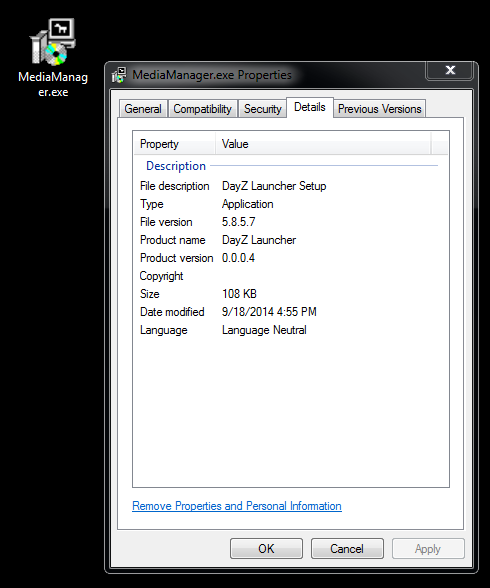
Based on the above screenshot, I think we can say that this particular file pretended to be a DayZ game file once….
Sample 2: PUP.Optional.OutBrowse
The second file we have looked at was retrieved from twitchviewbot(dot)co(dot)nf.
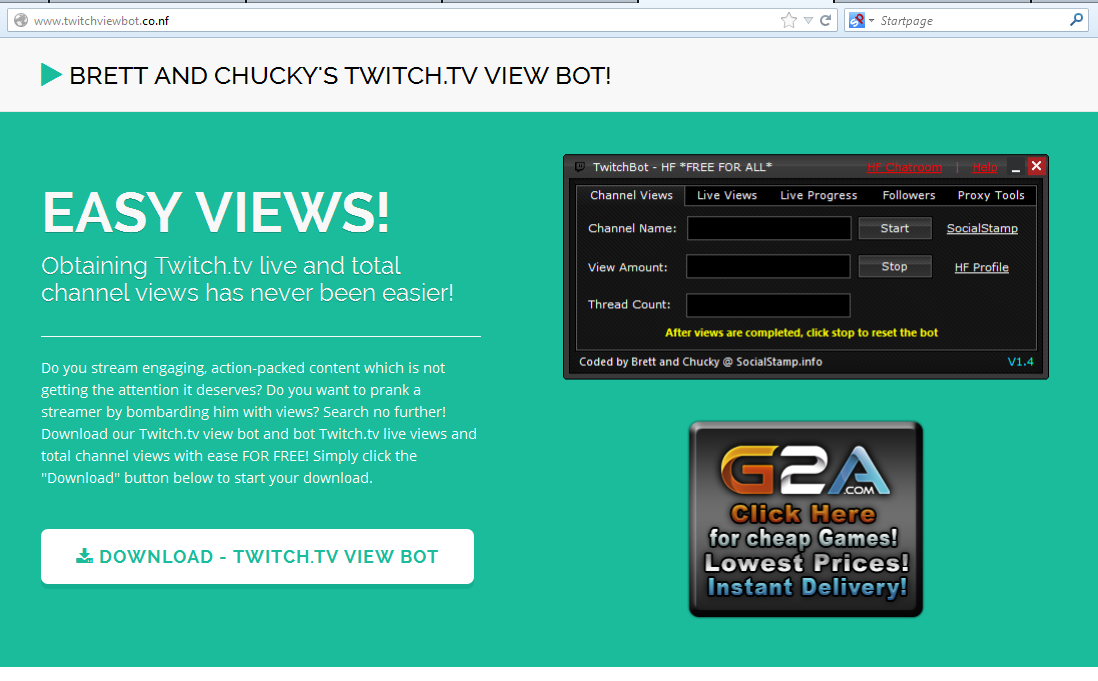
click to enlarge
EASY VIEWS!Obtaining Twitch.tv live and total channel views has never been easier!
Do you stream engaging, action-packed content which is not getting the attention it deserves? Do you want to prank a streamer by bombarding him with views? Search no further! Download our Twitch.tv view bot and Twitch.tv live views and total channel views with ease FOR FREE! Simply click the "Download" button below to start your download.
Upon execution, it displays a blue graphical user interface (GUI) courtesy of a pay-per-install (PPI) affiliate network (note the WOT rating), asking users to click the “Accept” button before the proper installation starts. Below is a gallery of relevant screenshots, showcasing what users may see during installation, along with the source page’s ToS and Privacy Policy pages, and an external download page:
File name: setup.exe (991,088 bytes) SHA256: 24c7c5789fa6fb33c7e8dd9f275315e716fcdf8af7b3a33d65802509b6b71f8a Malwarebytes detection: PUP.Optional.OutBrowse
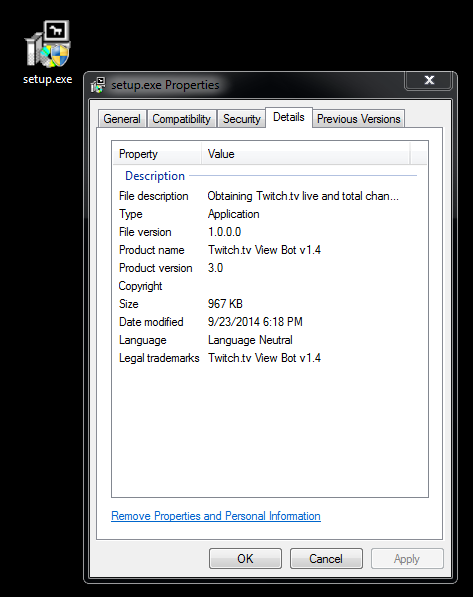
We discourage Twitch users who are interested in using bots as groups and/or individuals may take advantage of them.
Twitch.TV is growing in popularity, and as expected, a platform with so much to offer can be misused and abused by anyone willing to make a buck in a highly risky if not totally malicious fashion.
Jovi Umawing (Thanks to Joshua Cannell for the assist in file analysis.)










