Update: We now have an in-depth analysis of this Malware on the blog.
There’s a piece of email spam currently in circulation, offering up a “Payment confirmation slip” worth $40,000. That’s a lot of cash, and will surely sound too good to resist for many of the recipients of the below missive.
The email, titled “RE: Payment Confirmation Slip $40,000”, reads as follows:
Dear Sir,
We were instructed today by our client to remit $40,000 to your account as against their old invoice owed for the month of June. Please confirm attached payment confirmation and advise that payment was remitted to your account, inform us upon reception.
Thanks and best regards, Ms Jo Lee
Fidelity Trust Funds Invoices, refunds, payments and free gifts from the wallet inspector are all tried and testing ways of convincing potential victims to hand over their personal information, cash, or both. Note the “RE:” in the title, a common trick of email spammers to make it look at first glance like it’s already an email chain involving replies.
Emails such as these typically come bearing gifts in the form of (non infectious) Word documents asking for things like passwords, names, addresses and bank details. However, there are also a lot of attachments harbouring Malware, and this would be one of those moments where downloading a file and running it would be a bad idea.
Attached to the email is a Zip, and inside that is a Gzip file.
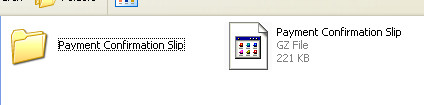
Open the Gzip up, and we’re confronted by the rather grandiose sounding “Payment Confirmation Details: Background Intelligent Transfer”, AKA discuri.exe:
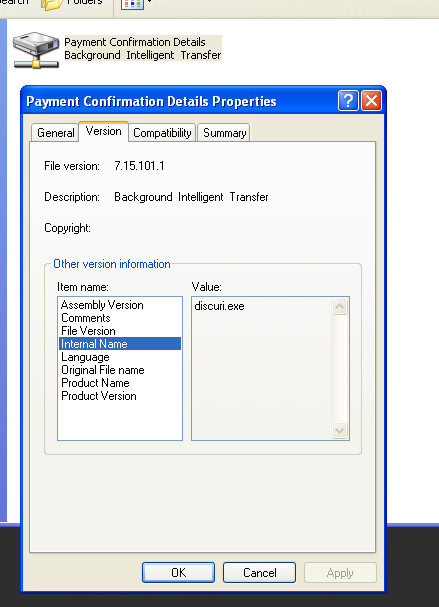
Interestingly, there is an actual “Background Intelligent Transfer Service”, but it isn’t anything to do with money transfers as the file and email are implying here. It’s actually an old Microsoft component related to asynchronous transfer of files, dating all the way back to Windows 2000.
The malware file has the ability to detect a VM (though it’s disabled in this sample) and is also wary of sandbox testing, going to sleep before getting up to mischief in an attempt to evade analysis. It also tries to prevent memory dumps and is XOR obfuscated, which is just one of a number of ways Malware tries to bypass analysis.
After some initial digging, it appears to create Zeus mutexes and connects to a particular C&C to grab content – however, so far all it is grabbing is a page not found. Either the C&C has flatlined, or the Malware is only going to grab a payload at specified times.
We’re still digging into the file for specifics and will update this post with more information as we get it. We should also have a deep dive blog about the file at a later date, so keep an eye out for that too.
For now, users of Malwarebytes Anti-Malware will find we detect this as Trojan.Passwords.MSIL. Detection for this one appears to be pretty good, as per the VirusTotal page (and VT pages don’t always reflect actual detection amounts, so the number of programs catching it could be higher).
If you’re not expecting a magical pot of money landing in your Inbox anytime soon, delete all such messages sent your way. Even if you are expecting a windfall, you’d likely know who was going to be sending it your way – you also wouldn’t need to go downloading and running random programs to do it.
When in doubt, check with the sender (assuming you know them) to ensure what you have is the real deal.
Christopher Boyd (Thanks to Joshua and Hasherezade for additional research)