Author’s Note: We at Malwarebytes continue to do our part in educating our product users and constant blog readers about day-to-day online threats and how they can avoid falling prey to them. “PUP Friday”, our latest attempt at getting users acquainted with files they may need to watch out for in the Wild Web, offers an in-depth look at some interesting and quite notable potentially unwanted programs (PUPs). Expect to see this type of content pushed out twice a month at the end of a work week.
Shell&Services and Mintcast 3.0.1 are Mintcast variants which make some annoying changes on your system if you are a Firefox user. Changes that will further expose you to the dangers of the internet. Nothing new we’d have to agree, although the method deserves some attention.
Background
In the EULA of Shell&Services, which would make for a grammar-police field day, you will find reference to hahomedia[dot]com where you can also find an online copy of said EULA. The entry it creates in the list of installed programs will show a link to jserrors[dot]info, which looks like it’s a login portal for customers of AdwareROI. AdwareROI is advertised as “an affordable adware platform that allows you to quickly & easily monetize your user base.”
What it does
Mintcast and its variants are adware applications that install two services on your system and one driver. The driver called WinDivert is a legitimate one that is also used by other applications as a network packet capture and (re)injection driver.
One of the changes the installers make and the one that we would like to focus on here, is that it creates a user.js file in C:Users{username}AppDataRoamingMozillaFirefoxProfiles{profile}.default. It only does this if there isn’t a previous file by that name. In this newly created file you will find the following lines:
- user_pref(“browser.safebrowsing.downloads.enabled”, false);
- user_pref(“browser.safebrowsing.enabled”, false);
- user_pref(“browser.safebrowsing.malware.enabled”, false);
This results in two options being unchecked (as shown below) that are part of Firefox’ safebrowsing settings.
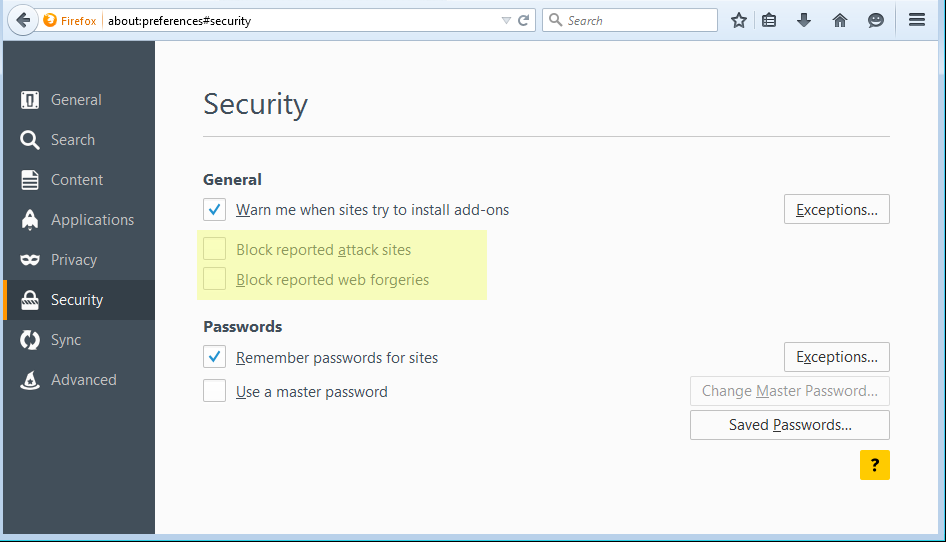
Due to the hierarchy in settings these will remain in place even if the user checks the settings manually. If you restart Firefox after re-checking those boxes, but without removing the user.js file, you will find the checkmarks are gone again. The first option in the list above, is a setting monitoring the downloaded files and if it is set to “True” it warns the user in case he downloads known malware. Setting it to “False” as this PUP does disables that option. The monitoring is done by comparing the downloads to a list of known malware distributors that Mozilla Firefox keeps track of.
The use of the user.js file is not an original idea by Mintcast. Other Potentially Unwanted Programs (PUPs) like those of the Yontoo/BrowseFox family have also been known to add a user.js file. Constant Fun for example adds the line–
- user_pref(“xpinstall.signatures.required”,false);
–that will allow unsigned extensions to be installed.
The hierarchy
I mentioned the hierarchy of settings in Firefox earlier. To explain this more elaborate, you will need to know how it works.
From the Mozilla KB:
A user.js file can make certain preference settings more or less “permanent” in a specific profile, since you’ll have to first delete or edit the user.js file to remove the entries before the preferences can be changed in the application. This has the advantage of locking in certain preference settings. A user.js file is also a way of documenting preference customizations and it makes it easier to transfer customized settings to another profile.When you launch your Mozilla application, valid preferences you’ve added to the user.js file are automatically copied to the prefs.js file (located in the same profile folder) where all user-set preferences are stored. For this reason, you should make a backup copy of the prefs.js file before you create or edit the user.js file.
So where manual settings and those stored in prefs.js can be altered by user interaction, those stored in user.js simply override those. To change them you will have to edit or delete the user.js file. So, if you run into Firefox settings that seem to re-set themselves, it’s a good start to check out the user.js file. For a complete guide how the preferences work I’d like to point you here.
Removal
Malwarebytes Anti-Malware detects and removes Shell&Services and Mintcast 3.0.1 as PUP.Optional.MintCast. This includes the lines in the user.js file where the cleanup routine will set the given lines to “True”. The premium version also blocks access to the domain hahomedia[dot]com. The removal guides for Mintcast 3.0.1 and Shell&Services can be found on the Malwarebytes forums.
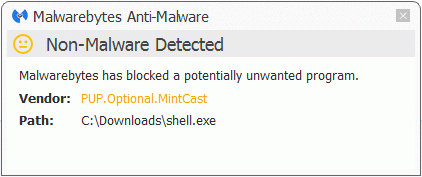
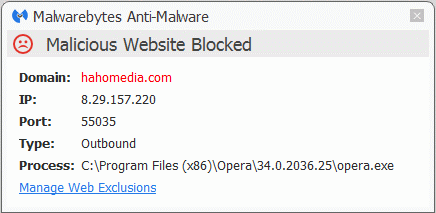
There are many more variants of the Mintcast family that show the same characteristics. You can recognize them in logs by their use of the WinDivert driver in the applications own folders and the use of the same uninstall key in the registry: HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionUninstall{29007E8C-251B-4F61-A70E-635786233494921877}_is1.
Summary
The Mintcast PUPs use the way Firefox loads its settings to make some changes that the user is not aware off and that put him at extra risk by disabling the safebrowsing settings.
Pieter Arntz











