Just when I thought I would be finished writing about PUPs for a bit, I came across a pop-up advising me of a new codec pack I should install. Little did I know at the time the efforts made by these PUP peddlers to sneak apps onto my system.
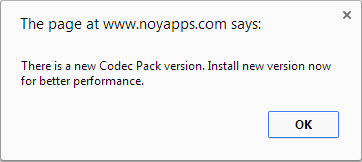
When I clicked OK, it took me to a site that recommended I install a “Codec Performer Update”. The pack supposedly includes support for all the major file types like MP3 and WMA.
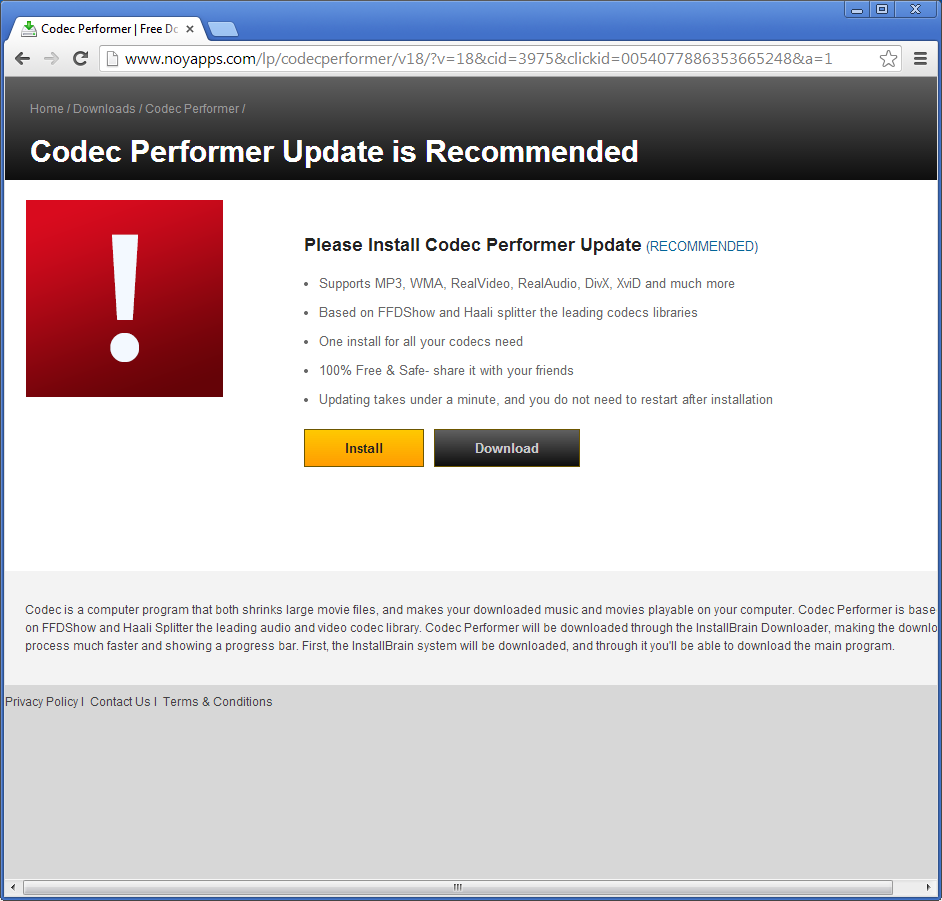
Once I downloaded the file (called CodecPerformerSetup_v4762b1.exe), I took a quick peek using some tools to see what I was dealing with.
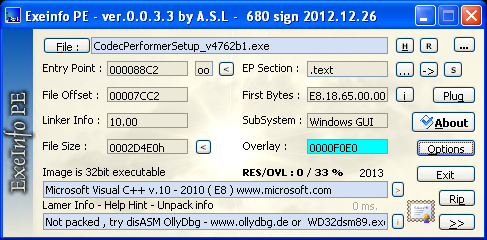
Looks like a regular binary, although it has some overlay data (data appended to the end of an image), which can sometimes be malicious.
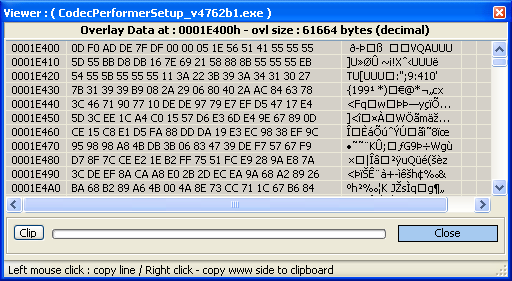
However, while there are some noticeable patterns do appear here, it seems we currently can’t do anything with this data.
Next, we’ll take a quick look at the code before we run anything.
The first thing I notice is a file being opened (itself) and an XOR of 0x55 applied to some bytes.
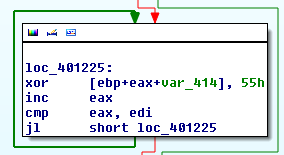
Curious, I went ahead and applied this XOR value to the overlay and it looks like we have something. Oftentimes malware will place additional binaries, shellcode, or sometimes even configuration data in the overlay.
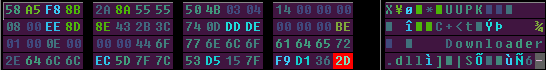
However, this isn’t the case this time. Here you can clearly see the text “Downloader.dll” that’s been de-obfuscated. All is not lost though, as it turns out this is the name of a DLL that we’ll see later.
The XOR taking place is actually de-obfuscating a zip archive instead. This archive is placed in a temp directory created at runtime.
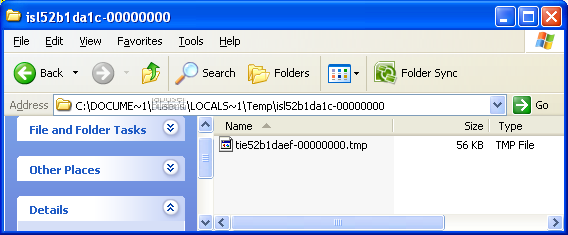
The file is unzipped with program called unzip.exe; the code for this program is embedded within CodecPerformerSetup_v4762b1.exe.
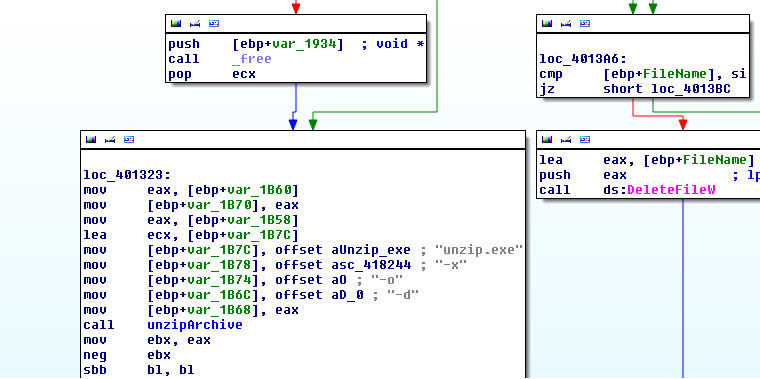
The unzipped file is called “Downloader.dll” and has a function called “a”. This is resolved using LoadLibrary/GetProcAddress.
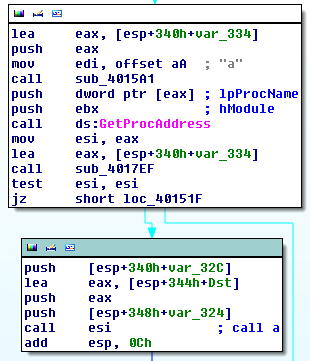
Next the “a” function resolves URLDownloadToFile, which uses some slight obfuscation. This certainly seems like a lot to go through just to install my codecs.
The beacon is to install.ibario.com, although it returned a 302 (moved temporarily) and re-routes to www.humiapp.com to grab the real Codec installer.
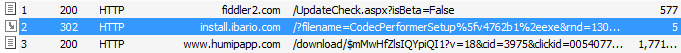
This domain is known to be used by the InstallBrain platform for file serving, as stated on the homepage.
In this case, it certainly peculiar why a legitimate application would have to jump through so many hoops—to include de-obfuscation and unzipping of another file—just to get to the real installer.
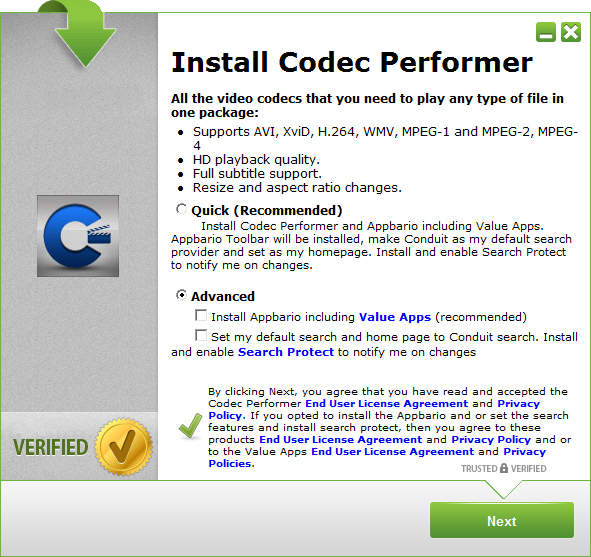
As it turns out, we do get a Codec Performer called CodecPerformerSetup.exe, but some PUPs are installed unless the “Advanced” radio button is selected and the additional software is disabled.
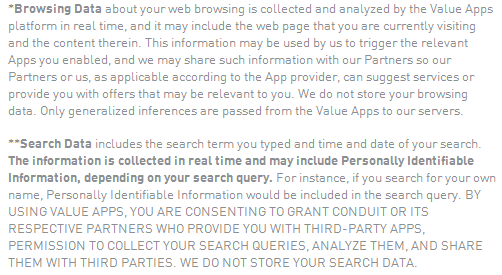
When reading the Privacy Policy of Value Apps, you’ll notice some data collection takes place, and it’s possible that Personally Identifiable Information could be collected as well.
Just last week I talked about the InstalleRex installer from WebPick, and the possible dangers of using that software.
While again, it appears we’re not getting served with malware, it’s always a good idea to stay away from this sort of thing to avoid unnecessary data collection and advertisements. Malwarebytes detects this installer as PUP.OptionalInstallBrain.A
Stayed tuned for more.
_________________________________________________________________
Joshua Cannell is a Malware Intelligence Analyst at Malwarebytes where he performs research and in-depth analysis on current malware threats. Follow him on Twitter @joshcannell










