What does MBR stand for?
MBR is short for Master Boot Record. Typically, the MBR is the first sector on a startup drive (or other partitioned media).
Sometimes it’s referred to as Master Partition Table, because, among others, it contains the location of every partition on a hard drive.
Most importantly, for this article, it contains the boot loader, which basically is a piece of executable code that starts the loading of the Operating System, or the boot-loader on a system that has more than one operating system installed.
So, in essence it is the first code that gets executed after the BIOS has done its job.
I see something nasty lurking
This is where malware comes into play. Being the first code to get executed gives you an advantage in the arms race between malware and anti-malware.
A program that can alter the MBR so that it can get something loaded into the Windows kernel is called a bootkit. Bootkits were very popular when viruses spread via floppies, but they are back and now spread through exploits and other more advanced ways then copying from floppy to floppy. A bootkit has the potential to disable all your security software before it evens gets a chance to start.
There is also a ransomware out there that moves the original MBR to a different location and places itself at the beginning of the drive. So the ransomware code is the first code that runs when the BIOS switches to the drive, to carry on the boot of the system.
But on the affected system the ransomware displays a message telling you where and how to buy a password, which will restore the original situation. With no guarantees of course. Which shouldn’t be a surprise when you are dealing with criminals.
Can I fix the MBR in case of problems?
First off: without expert help the chances of making things worse are much bigger than the chances of fixing it yourself.
FixMBR is a utility available as a command in the Windows Recovery Console. It will usually fix problems caused by multiple versions of Windows on one computer, so called multiboot systems. If you are using different operating systems then Windows you will need something else.
For example the GRUB bootloader that supports a mix of operating systems. But if your problem is caused by Malware, then it’s time to have a look at:
MBAR Malwarebytes Ant-Rootkit (beta) For a detailed guide on how to use it please read this article which appeared on this blog a while ago. Scanning the Master Boot Record can also be achieved by using the “Scan for Rootkits” option available under “Custom Scan” in Malwarebytes Anti-Malware 2.0
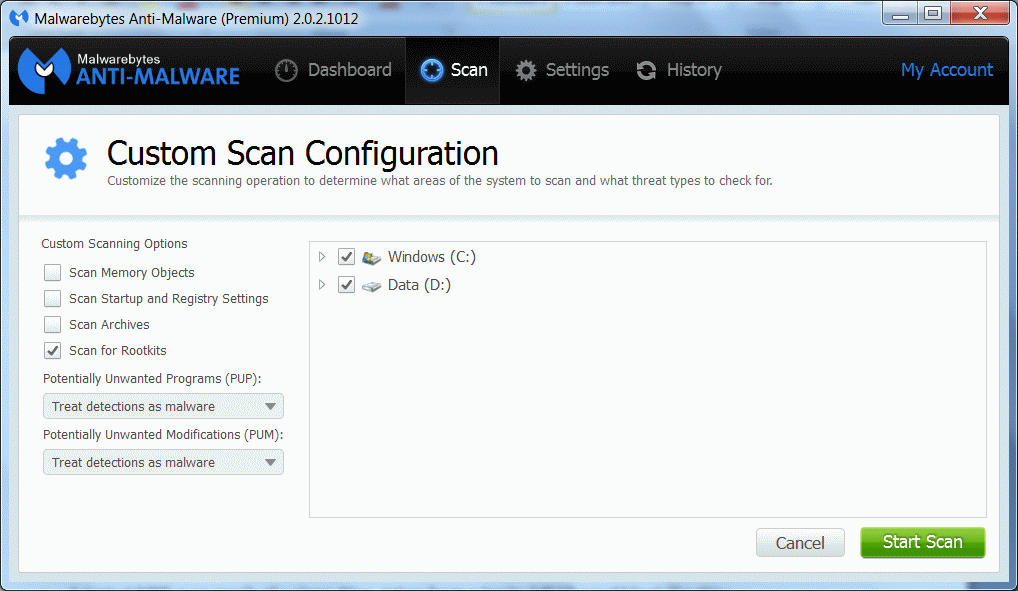
A typical MBR scan result of a clean drive, taken from a log by MBAR would look like this:
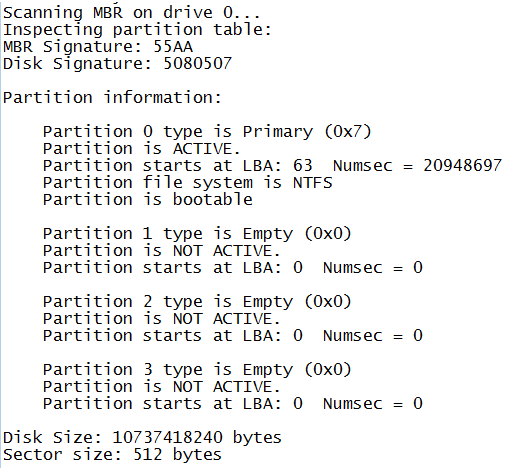
The MBR signature is important. After loading sector zero, the BIOS checks that the last two bytes of that sector are 55AA as seen on the disk. This 55AA is called a boot record signature and it tells the system that this is the end of the sector. This is something that the BIOS might require when booting. If the boot record signature is not present, you will likely get a BIOS-dependent message like this:
Error : Boot Record Signature AA55 Not Found
The sector-size of 512 bytes limits the disk size to 2TB and the number of primary partitions to 4, because of the maximum amount of information it can hold. If you have, or want more, you will need to use a GUID Partition Table Disk. Which looks to be the MBR’s successor when UEFI systems become the new standard.
Summary: the MBR is the first part of a physical drive that holds the information about the partitions on that drive and the boot loader. Malware has been known to alter the MBR to its advantage. Problems with the MBR are not easy to troubleshoot, but there are several methods to restore a workable situation. The MBR has some limitations that are becoming prevalent, but there are alternatives.
Recommended reading:
An example of Master Boot Record











