The past year turned out to be an interesting introduction into the new types of threats users are facing as well as what they will continue to face, at greater levels, in the coming years.
We have continued to see the use of scammer and “assumed guilt” threats such as Ransomware and the emergence of even greater threats using similar tactics. We have seen the rise and fall of a very popular exploit kit and had an entire year of cautious surfing because of drive-by exploits and watering hole attacks.
Phone scammers have shown us that it’s not always safe to trust people who claim to be technical specialists and the battle against mobile threats has raged on in greater severity.
As we enter a new year, we can expect these threats to continue with more destructive force than we have ever experienced.
Our world is changing and much of our personal communication; banking and overall well-being is now accessible online. This trend will only continue as we adopt a new ‘online life’, where all sorts of criminals are taking advantage of those inexperienced with internet security.
We are lucky that we have been able to learn from the past year’s challenges and adopt new strategies to remain safe online. The lessons learned are invaluable when dealing with future threats; however, perhaps the greatest lesson of all would be the individual’s understanding of online threats and proper security measures. For example, while most Antivirus programs provide adequate protection, none of them will keep you safe if used improperly.
A few years ago, I said the internet was most like the ‘Wild West,’ where people were free to start their own adventure. There were outlaws, for sure, but at the same time law men who would protect the innocent.
Unfortunately, I can’t say that any more about our current situation: the cowboys are gone, and have been replaced with soldiers. The internet today is a warzone, and everybody online is part of the fight.
Biggest Threats of 2013
Ransomware
In the outlook report from 2012, we mentioned that it was the greatest year for Ransomware, and I still attest that based on uniqueness, novelty and diversity, that is true.
However, as far as damage goes, 2013 has it beat. Ransomware, as you may know, is short for Ransom Software/Malware that attempts to lock the user out of their system or encrypt their files, holding their livelihood “Ransom”, in return for cash.
Last year, we saw Ransomware that frequently posed as government agencies, such as the FBI, and demanded the user pay a fine. I called this type of scam “assumed guilt” because it accused users of crimes that they probably didn’t commit but might believe they had by accident.
Ransomware last year and into this year, was mostly spread via exploit kits. It took a while and numerous arrests but the numbers have decreased and some of the big players have even ended development of new variants.
Cryptolocker
Reveton and Urausy were two of the biggest ransomware groups of the last year but their operations do not hold a candle to the kind of damage caused by the infamous Cryptolocker.
Discovered in September, Cryptolocker actually double encrypts a user’s personal files (such as images and documents) with both a local AES key as well as a remotely created and remotely stored RSA-2048 key.
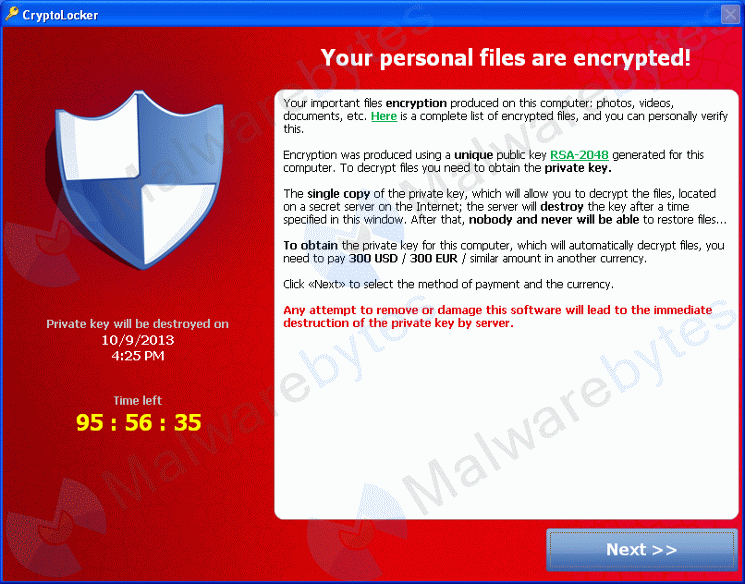
Other Ransomware from the past has claimed to encrypt files but it’s usually either a hoax or they use a simplistic encryption method that is easy enough to break and return users files back to their intended state.
The type of encryption used by Cryptolocker is the most secure standard today. Using asymmetric public key encryption, they encrypt the files with a public key locally on the system and you can only decrypt the files with the private key, stored on the remote server.
So what about RSA-2048? Can’t you break it?
Well, hypothetically, yes, we could break it; however, the time it would take to break that kind of encryption would take more time than we will be alive. To put it into perspective, using a normal desktop system to try to revert your files back to normal, without the use of the private key, would take roughly 6.4 quadrillion years.
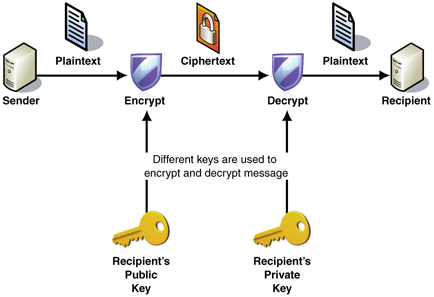
If you had a massive amount of super computers and the smartest cryptographers and mathematicians in the world working on it, it might take a little less time but nobody knows because nobody has done it yet.
The price to unlock your files has changed a bit depending on the type of currency accepted. It started out with MoneyPak cards, same as with older Ransomware but then evolved into only Bitcoins. The price was set at ~$300.
Cryptolocker informed the user that if they did not pay within the time allocated (usually 72-96 hours), the remotely stored private key would be erased and their files would never be decrypted…or so we thought.
Whether it was their original intention or not, the creators of Cryptolocker decided to give their victims a break at the cost of ~$2000 and a website was setup to allow victims to pay 10 Bitcoins and receive the key to unlock their files.
So this begs the question, was the key ever really destroyed as advertised by the Cryptolocker ransom screen? If they are able to unlock a system after the fact then the answer is no, it was stored away somewhere for later use.
The other possibility is that all distributions of a certain Cryptolocker variant used the same key with every system it infected and it is just a matter of finding those infected with the correct variant that can pay the $2k.
Either way, to unlock the files, the user has to re-infect their system with Cryptolocker and then pay an immense fee, something we highly recommend NOT to do.
The security community is still working hard on battling this threat and the threats that we will surely see in the future that imitate it.
For now, our best defenses are proactive protection to stop the malware before it has a chance to infect the system. Be it though stopping the executable or preventing the malware from reaching out to its command and control server, therefore preventing the encryption of the files in the first place.
We will visit Cryptolocker again in our section on 2014 predictions but be sure that this is not the last we will see of this style of Ransomware.
Phone Scams
Phone scammers work along the same lines as Fake AVs, where you have a third-party source telling a user that they have tons of malware on their system and it needs to be cleaned up, usually for a high price.
Phone scammers are not exclusive to 2013 but the amount of reports we get and the different types of scams these guys are using seem to be peaking.
In 2013, we have seen scammers:
- Pose as Microsoft
- Pose as an antivirus company
- Pretend they can remove malware from a Mac
- Claim that not being able to connect to an inactive web server means you are infected
- Pose as law enforcement
- …and much more!
Our Senior Researcher Jerome Segura has made three videos based on phone scammers and the tactics they use to fool unsuspecting users; I highly recommend checking them out.
- http://www.youtube.com/watch?v=3P6uv8Fy3ik
- http://www.youtube.com/watch?v=FDJWixw4TCI
- http://www.youtube.com/watch?v=s60jLxInYb4
The biggest defense against this type of scam is knowledge, you will most likely never receive a call from a legitimate software company or antivirus/anti-malware firm to remove malware they have “detected” on your system.
To help our users and readers in educating themselves on these threats, we have created a ‘Tech Support Scams – Help & Resource Page’ on our blog that is updated when new scams appear to reflect the current threat landscape.
The principles of identifying scams is age old. However, when presented with evidence of a problem in a method that the normal person does not understand, those principles go out the window. That is what these scammers try to exploit so do not become a victim.
Android Malware
Since we knew mobile phones were going to run operating systems, we knew that mobile malware would be inevitable. And 2013 showed us an increase in mobile scams and malware.
A large portion of mobile malware consists of what we refer to as SMS Trojans, malware that sends premium text messages or makes premium phone calls without the phone owners knowing about it. The user doesn’t discover what has happened until after they have received the bill. While these types of attacks are primarily seen in Eastern Europe, others exist worldwide.
A similar threat example is the Perkle crimeware kit; it infects the user’s desktop, poses as an authentication measure for the user’s banking web site and requires the scan of a QR code that downloads malware onto the user’s mobile device.
The mobile side waits for confirmation texts sent by the bank, intercepts the codes and sends them back to the desktop to gain access to the victim’s bank account.
Either way, the amount of mobile malware seen this year has increased substantially enough for the community to consider it something we are going to be dealing with much more in the future.
Blackhole Exploit Kit
In 2012 and a large portion of 2013, the BlackHole Exploit Kit was the primary method of malware delivery for cyber criminals looking to setup drive-by attacks. It hosted an assortment of different malware, depending on the need of the criminal using it, for example:
- Zeus Trojan
- ZeroAccess Rootkit
- Reveton Ransomware
- And more
The kit was sold on cyber-crime forums and black markets to would-be criminals to setup on their own (or compromised) web servers. The criminals would define which payload was to be loaded (the malware) and what exploit to use. From there, once a user visited an exploit page, the malware would be installed.
In many cases, exploit kits are rented out, purchased for a high price from one criminal and then offering to host another criminals malware for a fee.
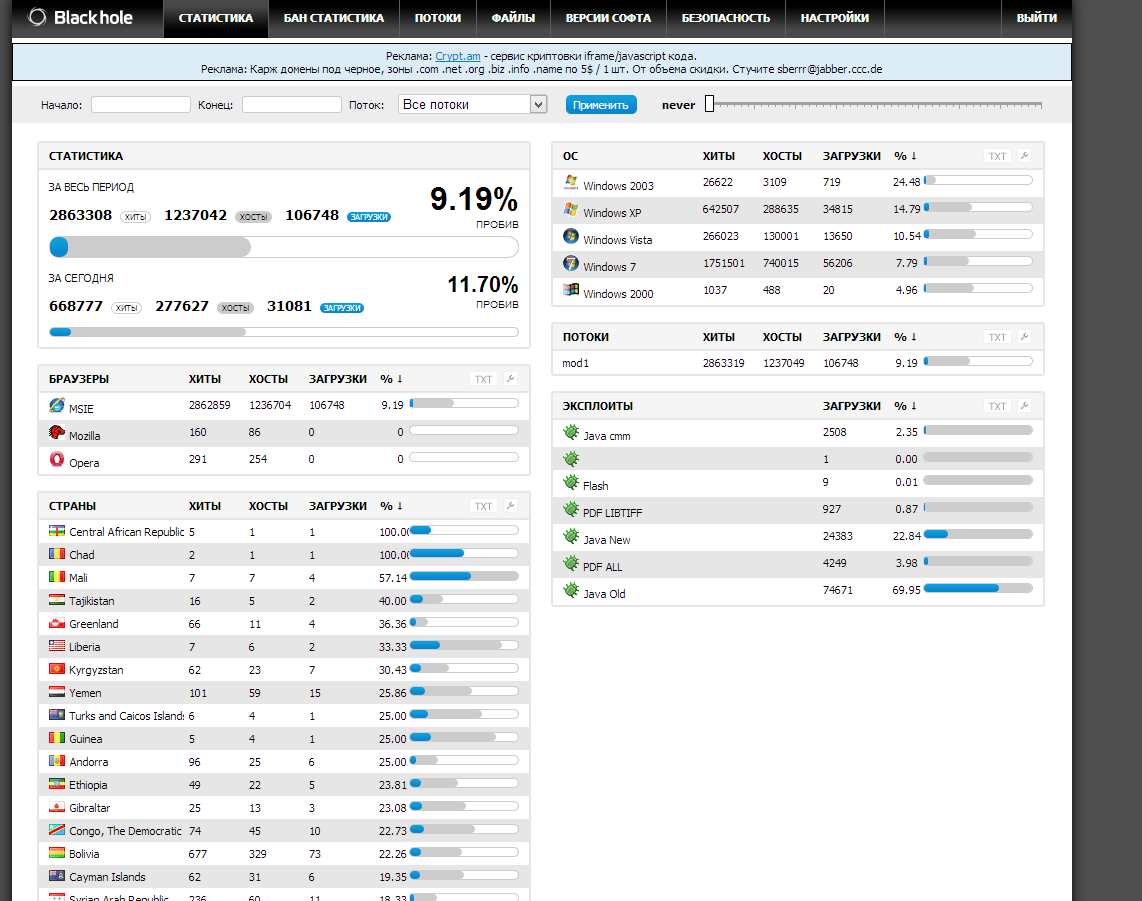
Courtesy of Kafeine @ malware.dontneedcoffee.com
In early October, law enforcement arrested the creator of the BlackHole Exploit Kit, “Paunch”, and since then, the use of BlackHole has steadily decreased.
With older versions still lingering and being used by cyber criminals as well as modified versions released by third-party sources.
As we enter 2014, we may see less and less of the older variants of BlackHole, however it’s doubtful that it will drop off the map entirely.
At the same time, we may see the emergence of a brand new dominant exploit kit that has all the ability and threat of BlackHole but with new exploits targeting more current operating systems.
DDoS Attacks against Banks
2013 had its fair share of bank attacks, be it through the use of malware or just hacking. One of the most notable examples were attacks against US banks in August: The attack began as a Distributed Denial of Service Attack against the target bank, the IT staff was able to respond and worked hard to fend off the attack, keeping their servers and services available to customers.
However, while the staff was busy dealing with the DDoS attack, malicious attackers were able to infiltrate the banks systems, unnoticed due to being concealed under the massive amount of traffic from the DDoS.
The attackers made off with a significant amount of money in this highly organized and effective cyber bank robbery.
Crime on all levels has been duplicated online, bank robbery included. Will we see more attacks? Definitely. Will they get worse? Yes. However, with every attack comes the lessons learned and shared with the community, making banking experiences even more secure.
PUPs
Potentially unwanted programs are the slightly less harmful cousins of malware, installing things on your computer you neither want or need, devouring system resources and making your computing experience a nightmare.
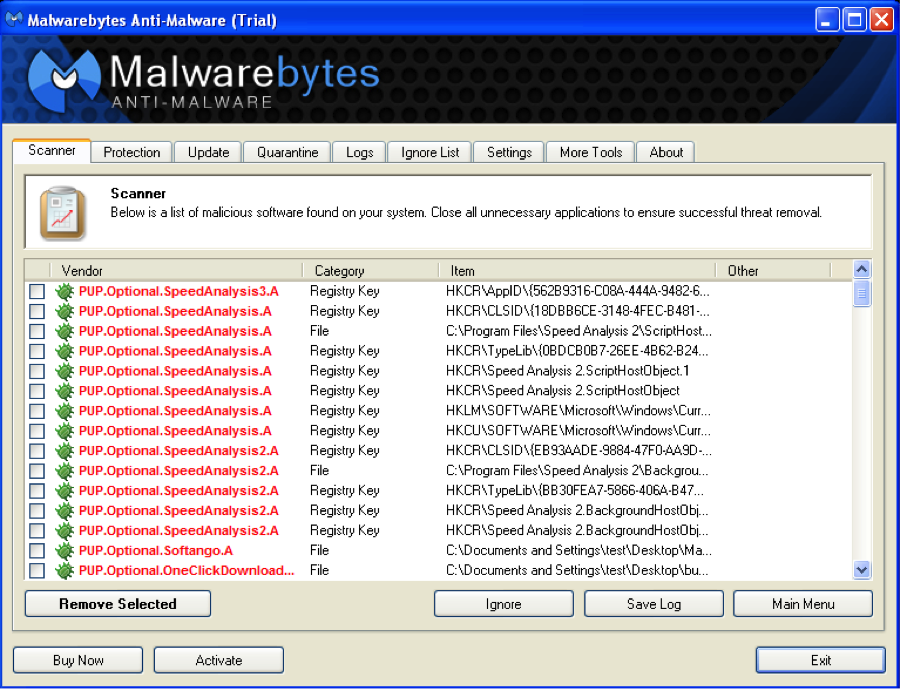
You might be wondering what exactly PUPs are, well a few examples are:
- Toolbars
- Search Agents
- Value Finders
- Etc
In July of 2013, Malwarebytes Anti-Malware began detecting PUPs and offering their removal to our users, we do not automatically flag them for removal but allow the user to choose whether they want to run the software or not.
In late November, we discovered a new type of threat with some PUP peddlers, the inclusion of a Bitcoin miner installed on the system. This is a serious threat in that running a miner on a system that is not designed to do so may cause serious damage to the system itself.
We expected such things from malware like Ransomware, however, it is an entirely different story when programs that were potentially harmless, are now doing harm to unsuspecting users.
For an official listing of what we at Malwarebytes consider “Potentially Unwanted” check out our criteria for PUP classification:
http://www.malwarebytes.org/pup/
2014 Predictions
Ransomware Evolution
2012 and then 2013 showed us the peak of Ransomware and the kind of damage it could do. From being simple psychological games that barely prevent you from continuing use of your computer, to accusing you of crimes and eventually encrypting all the files you hold dear.
Will we continue to see it in 2014 though? Most definitely.
While many people seem to know about the threats of Ransomware and properly protect themselves from it; cyber criminals just change around their attack method to counter our protections.
Seeing as how often it has been used in the wild, we can say that the attack is highly successful and therefore we can expect to see its continued use.
However, if we look at some recent activities made by the criminals using Cryptolocker, we can see that they are getting somewhat desperate. Cryptolocker now offers a “post timer” option to decrypt files, by hosting a site that offers decryption for a higher fee.
Did they do this because they weren’t seeing a very good return in investment from the original infections? Maybe they are just trying to reel in even more cash from users that were unable to pay the original fee. (Though in my opinion, if you think that users who are unwilling to pay a ransom of $300 how can you expect them to pay $2,000 or more.)
I predict that for 2014, we will see continued evolution of Ransomware, figuring out new ways to infect users and force them to pay a fee.
We will see Ransomware making more of a presence on previously less targeted platforms, such as OS X and mobile devices.
However, unlike the end of 2012 and early 2013, we will see fewer cyber gangs using Ransomware tactics. For example, there were numerous families in the wild, spreading very similar Ransomware but different enough and originating from different sources, while 2014 will most likely have fewer sources but more advanced, and therefore dangerous, malware.
Mobile and Device based Malware
Speaking of mobile malware, you can expect the continued threat of malicious software and scams targeting your mobile device in 2014.
As mentioned previously, we’ve seen an uptake in mobile malware in 2013 as mobile devices became the primary source of internet use, eCommerce and social interaction for many users.
This user trend is unlikely to go into decline as technology gets even more portable and more powerful, therefore where the users go, the criminals will follow.
Those of us in the west have been lucky that we have not endured the types of mobile threats our friends in the east have, such as Russia. SMS Trojan attacks are far more frequent in that part of the world than they are in the U.S. However, there are plenty of avenues malware authors could take to steal our money.
For example, we could see mobile malware that uses the saved Google Store credentials to buy apps that you don’t want or need. They could also use your device for malicious attacks, such as DDoS, and adding your tablet or phone to a botnet.
In addition, it is not farfetched to think that mobile devices are the next big target for remote access trojans, allowing your phone to become a surveillance camera, microphone and in the case of Bluetooth, a transmission device.
Also mentioned previously was the discovery of malware tactics that infected the desktop as well as the mobile device; you can count on the fact that we will see an increase in that type of threat.
Many online services, banks, stores, etc. are using authentication measures that require codes sent to mobile phones, making it a requirement for cyber criminals to intercept calls, text messages or anything else for the purpose of accessing secured services.
Luckily, many antivirus and Anti-Malware vendors (including us) are migrating their already trusted malware protection solutions to mobile devices to counter these threats.
Mac OS Malware
2014 will have more attacks against Mac operating systems, period.
If you’ve kept up with yearly predictions from security companies in the past, we have all said this before and usually the impact isn’t quite what we expected. It’s almost like a “boy who cried wolf” thing, but just like the story goes, those who don’t heed the warnings will inevitably become victims.
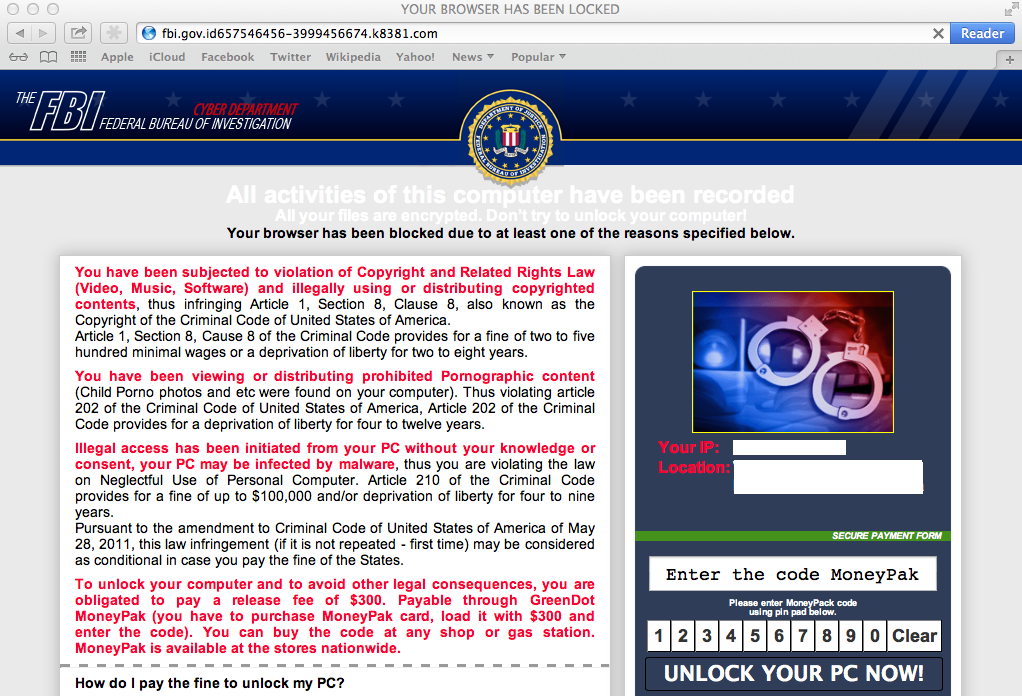
Recent history has shown us that Macs are being targeted with similar attacks as PC users. We’ve seen Ransomware, malicious browser plugins, rogue antivirus software and a slew of other malware.
In addition, computer repair scams exist for Mac users just as much as for PC users, a threat that doesn’t even require a malware infection but rather just an unsuspecting and uninformed user.
Finally, many of the plugins, extensions and third-party applications that are exploited on Windows are also used on Mac platforms and therefore susceptible to the same threats when it comes to remote code execution.
New Methods of Privacy
The biggest story in security this year has been the leaks released about the National Security Agency (NSA) and their ability to collect, intercept and decrypt all kinds of electronic communication.
Due to the new concern users may have about their privacy while online, we may very well see an increased development of privacy technologies.
From enhanced biometric software to three factor authentication, 2014 will most surely see the average user taking precautions in securing their personal data online.
As an unintentional bonus, this will in turn protect users from online scams and even malware that would otherwise be able to infiltrate and steal confidential information. Hopefully the fear of government surveillance will be enough to safeguard otherwise unprotected users and therefore starve the cyber criminals.
New Dominant Exploit Kits
As I mentioned when explaining the previous year’s threat from the BlackHole Exploit Kit, there will likely be a successor to the dominant exploit kit throne.
I predict that by the middle of 2014 we will see a new and more powerful exploit kit that possesses similar traits to BlackHole and will either be very cheap for cyber criminals to purchase or be leaked to the underground community to use for free.
However, 2013 was a great year for law enforcement, with arrests of the BEK author, numerous criminals behind the rampant use of Ransomware and even arrest of actors behind DNS Changer. The next year may follow that trend and as soon as we see a new BEK, it won’t take long for it to be taken down.
Hardware Exploits
Attacking software is easy and very effective. Users use the same software across the board, be it different versions. A cyber-criminal has a high probability of success when they target something like Java or Flash.
The other end of the spectrum is hardware attacks, where attackers use specially created software to exploit vulnerabilities in user’s firmware running on some piece of hardware. These attacks are not as common however they are incredibly powerful.
The problem is that so many users use different types of hardware in their systems and predicting what a user has running is a nearly impossible without targeted intelligence. Therefore, we only really see hardware attacks used in state-sponsored operations, where one government is trying to infiltrate the networks of another.
With the migration from PCs to Macs, we may very well see more attacks aimed at certain types of Mac hardware, only because Macs use a standard hardware build for their products.
A clever cyber-criminal might look at the most commonly used Apple product and then investigate possible ways to exploit that particular system. An attack aimed in that direction has a higher chance for success than a similar attack on the PC. The potential for information stealing, disruption and even being undetected is much greater.
The good news is that hardware attacks are very hard to come by, regardless of whether or not intelligence gathering has been performed.
For the average user, there is little likelihood that cyber criminals would target their systems because of time and resources required to develop such a threat.
It is still more likely that hardware attacks would be developed and aimed at state-sponsored entities, though as we continue to adopt new technologies and policies like “bring your own device,” the threat of infection becomes greater.
Conclusion
Casual use of the internet is no longer an option, your system should look like it’s ready for a fight, the same as you would look if you were to enter a warzone. Equipped with the proper tools, a user has a chance of being safe from online threats, an updated antivirus, a firewall, additional protection software like Anti-Malware and Anti-Exploit tools, up to date operating systems and third-party extensions and a trustworthy and secure browser.
However, all those protections would be worthless without the proper knowledge.
You can always wait until the news has reported on a threat, luckily our society treats cyber-crime as newsworthy and important as bank robberies or serial killers, hopefully that trend continues.
Though what you read or watch on the news is only a part of the required knowledge, telling you about the biggest and flashy attacks but not so much on the threats you face every single day.
To obtain the knowledge of those threats, read security vendor blogs, follow a couple of security vendors or professionals on social networking sites, listen to podcasts and other programs devoted to computer security.
Then, after you have armed yourself with enough survival knowledge that you are confident online, share it. The biggest targets for cyber-criminals are people who aren’t informed, help out your fellow-man by educating your friends and family, even if it’s in passive conversation. Share links to articles and ask questions.
This war will not be won with passive defense, installing security software and then ignoring it for a year. It must be fought with an active offensive to prevent as many victims as possible. If we can do that, if we can limit the amount of people susceptible to attacks by cyber-criminals, we will eventually starve them out of information and money.
If we can make the cyber-crime business less lucrative, we will shrink the amount of threats we experience drastically. It all starts with you.
Thanks for reading and safe surfing!











